To read this content please select one of the options below:
Please note you do not have access to teaching notes, distribution network design: a literature review and a research agenda.
International Journal of Physical Distribution & Logistics Management
ISSN : 0960-0035
Article publication date: 1 June 2015
The purpose of this paper is threefold. First, it classifies research on distribution network design (DND) according to the methodologies adopted and themes tackled. Second, it discusses the main implications for practitioners. Finally, it proposes a few promising directions for future research.

Design/methodology/approach
The review is based on 126 papers published from 1972 to 2013 in international peer-reviewed journals in the Business, Management and Economics field. The academic papers have been analyzed and classified based on the main research methods used and the themes tackled.
It was found that most of the earlier research adopted quantitative models to deal with different decisions on DND, whereas the number of conceptual papers, proposing frameworks and classifications, is still limited. In all, 42 factors that affect DND have been identified and classified into five groups, and the relationships between factor groups and strategic decisions have been investigated. This study revealed that some important areas have not received much attention in the literature and, therefore, three potential directions for further research have been identified.
Research limitations/implications
Due to the extremely large number of papers on DND, it is possible that a few papers may have inadvertently been missed. Despite the possibility of not being all-inclusive, the authors firmly believe that the general picture presented in this paper is precise and trustworthy.
Originality/value
This review offers valuable insights for practitioners: a clear understanding of the main decisions related to DND; a comprehensive analysis of the main factors that affect the distribution network structure; a clear understanding of the relationships between factor groups and key decisions; and a guide to the models that can be used to support the different phases of DND.
- Literature review
- Supply chain management
- Distribution network design
- Logistics network
- Strategic decisions
Mangiaracina, R. , Song, G. and Perego, A. (2015), "Distribution network design: a literature review and a research agenda", International Journal of Physical Distribution & Logistics Management , Vol. 45 No. 5, pp. 506-531. https://doi.org/10.1108/IJPDLM-02-2014-0035
Emerald Group Publishing Limited
Copyright © 2015, Emerald Group Publishing Limited
Related articles
All feedback is valuable.
Please share your general feedback
Report an issue or find answers to frequently asked questions
Contact Customer Support
Advertisement
Tools and Techniques for Teaching and Research in Network Design and Simulation
- Original Research
- Open access
- Published: 17 March 2023
- Volume 4 , article number 269 , ( 2023 )
Cite this article
You have full access to this open access article

- Muhammad Azizur Rahman ORCID: orcid.org/0000-0002-0805-7461 1 &
- Algirdas Pakstas 2
2586 Accesses
Explore all metrics
Computer networking is taught for some time at universities. A network is a complex mix of applications, communications protocols and link technologies, traffic flows and routing algorithms. Teaching the networking concept, the network design process is a challenging task, requiring designers to balance user performance expectations with costs and capacities. One of the obvious approaches employed to deal with its complexity is through the use of modelling and simulation techniques. This paper examines three best educational tools that can be used in the Computer Networking course at Cardiff Metropolitan University or any University for educational purpose. The paper demonstrates that a successful teaching programme needs to combine a range of teaching tools to achieve its aims. Analysing various aspects of the course provides evaluation of the overall success of the tools. Many network design and simulation tools have been studied. Based on our research and experiment, the best educational tools were selected that could be used for the purpose of teaching in the area of computer communications networks. The wide area network modelling tool Delite, the network simulator ns-3, the topology generation tool Brite can be used together to teach students the networking concepts. These tools can not only help students to understand computer network principles but also improve their network practical skills. Currently there are various tools available that are created by different companies and groups of researchers in academia and that are intended for use as practical and/or educational tools for network design including security issues. To make this task easy, different users, researchers and companies have developed different network modelling and simulation (MS) tools. Very often, such tools are addressing different issues in the network design process which are complementary to each other. It would be useful for learning and improving the network design process by allowing the use of a variety of tools.
Similar content being viewed by others

Network Design, Simulations and Improvement, Using Riverbed Academic Edition, Version 17.5 at the Universities: A Case Study of University of Technology, Jamaica

WiMAX in Education: A Wireless Networking Lab Design

Developing an Interactive Web-Based Programming Platform for Learning Computer Networking Protocols
Avoid common mistakes on your manuscript.
Introduction
Teaching computer network is very challenging because of the abstract concepts. In the teaching of basic and advanced computer networks concepts (routing, mobility, load balancing, reliability, capacity, delay and so on), students not only have to acquire the theoretical knowledge but also the practical skills to configure and manage real computer network scenarios. Successful course delivery is a key aim for all educators. The failure of only one part of a course can have disastrous effects on the attitudes of students. The most of the Universities have been delivering computer networking course that aims to teach students the basics of computer networking. Our experience has been that to provide students with a positive learning environment requires the development and integration of a large number of teaching tools. No one tool can be a perfect for teaching in the same way that no one tool will ever be the perfect for computer networking. The teaching has culminated in a strong emphasis on the student being an active learner, as opposed to a passive receiver of information, which is then regurgitated back to the assessor.
The network design process is a challenging task, requiring designers to balance user performance expectations with costs and capacities [ 1 ]. External factors, such as government policies and regulations, the competitive situation, available technological services and products are adding complexity to the design process. Organisational strategies, culture and policies also affect the planning and design process. The amount of human and technical resources in the data communication functions of the organisation can also strongly affect the choice. Electronic communication is so ubiquitous in modern business that it is hard to develop an overall strategic vision that is comprehensive and at the same time detailed enough to be useful. Additionally, these factors can change and make the network learning and planning process even more complex. The business role of the proposed network application adds extra complexity to planning process. To improve the quality of undergraduate education such a complex topics network simulation tools best option. There are many authors who attempted to solve the question on how can students’ motivation and interest for the complex teaching material of Computer Networking and other complex module(s) be improved. Currently, many works deal to improve the pedagogy of computer networking concepts using network design and simulation tools and techniques [ 2 , 3 , 4 , 5 , 6 ]. The article [ 7 ] shows how to reduce the gap between the education in universities and real work environments in the area of computer networking using Packet tracer, GNS2, OPNET, and fat-tree simulator tools. There are some recent published papers dealing with the complex subjects in the classroom [ 8 , 9 , 10 ].
Capacity, Reliability, and Delay are three "magic words" used for describing concepts of the computer network design [ 11 ]. While capacity and delay are relatively well understood, this is not the case for reliability. The term reliability is often used interchangeable with availability and dependability. Increased redundancy in the network structure is often considered as important, or even the only way to achieve higher levels of reliability. Factors affecting performability of the communications systems are discussed. Reliability in the network design process in a context of systems approach to network design is considered in more detail. Examples of calculations of reliability figures for different network designs are considered using the Delite tool. Reliability support in communications protocols is discussed. Example of simulations and animations of network dynamics is presented using the ns-3 and nam tools. Example of topology handling is Brite tool.
To understand the details of the networking issues, students can use the Delite for the calculation of the Capacity, reliability and delays of the networking module. On the other hand, to see the dynamic behaviours, NS-3 can be used. Finally to know the network topology, Brite tool case be used. We found one article regarding the tools for teaching network [ 7 ].
The purpose of this paper is to show how simulation tools and technology can serve as an effective educational tool to enhance the learning of process of networking concepts. In this paper we examine the three teaching tools that can be used in the course of computer networking, features and design process in depth, pedagogical tool for the teaching of computer network design. If a student needs to understand the basic magic works, then they can use Delite; whereas when student needs to see dynamic characteristic of network model, then NS-3 would be the suitable for teaching. To work and gain knowledge about the topology, the Brite would be the perfect tool.
Problems in Teaching Computer Networks
The Open System Interconnection model (OSI) and communications network simulation are two parts of the important area of computer networking course. The OSI model provides an abstract function decomposition of a network protocol and is commonly used to depict network functionality of each layer. There are many tools for network analysis including cost, reliability, capacity, delay etc. both in commercial and educational sectors. It is easy for the students to build the visual connection between OSI model and network protocols of each layer.
The technical complexities of computer networks and data transmission processes and protocols present immense challenges for teaching and learning in computer network education [ 12 ]. Students often need to have intensive studying and practical experience with hands-on activities to understand the large numbers of complex and abstract conceptual details on network payers, protocols, addressing format and configurations [ 13 ]. The traditional mainstream teaching method of lecturing is found to be inadequate for motivating students in network education [ 4 ]. The common challenge often seen in teaching computer networking and data communication is the difficulty for students to understand the complex technical concepts and to visualise the various network protocols, roles, and functions in data communication [ 15 ]. More importantly, students may have further difficulty in developing the skills and ability to use higher level skills for troubleshooting and creative problem solving [ 16 ].
Some issues of the computer networking could be found in [ 17 ]. Computer Networking is difficult to learn. It advances very rapidly. Many Computer Networking topics have also quickly developed into separate subjects, notably Wireless and Mobile Networks, Optical Networks, and Network Security. It becomes increasingly difficult to teach the subject effectively, partly because the Internet’s success has attracted students with various backgrounds. Besides the issues, there are quite a number of obstacles to teaching and learning Computer Networking effectively, as outlined below. (a) The principles underlying Computer Networking are intrinsically very complex. (b) Computer Networking concepts and protocols are also very abstract to many students. (c) Unlike Computer Programming and Computer Architecture courses, for example, resource provision for hands-on practical experience in Computer Networking is problematic. A Computer Networking laboratory, if available, usually has a ready-to-use computer network on which students can conduct various experiments. However, students should also be expected to know how to set up a computer network from scratch after taking the course, very much like knowing how to write programmes after taking a Computer Programming class. But it is not quite possible to provide adequate resources to achieving that in many academic environments. (d) Many terminologies and acronyms are introduced and used in the field, and some of them are very similar, e.g. ARP and ARQ. (e) Some of the networking problems are difficult to comprehend and appreciate due to students’ common lack of practical experience.
Students and Researchers Expectations from the Network Modelling Tools
Use of network modelling and simulation tools is an important element in the process of design, deployment, testing and evaluation of any communications network. Tools are the integral parts of the overall methodology of planning and designing a network. Designers may analyse the output produced by the tools, compare several designs and select the best design according to some predetermined criteria. Tools are also needed to study and test new protocols.
Typically, every network design undergoes some standard stages and it is expected that tools may help in these stages. Network modelling and simulation tools may help [ 18 ] in:
(a) The planning of the network topology and link capacities:
It is expected that the tool will use only the links with a standard range of capacities.
Means in the case of network design and upgrade, a tool can interface with existing database systems to obtain the current network configuration directly without data entry by designer;
Typically provides an interactive graphical user interface for network editing, capacity calculation, traffic estimate, performing network optimisation, allowing users to perform “what-if” analysis and many other features;
Displays the results through menus, tables and graphical displays via animated utilisation bars, graphical statistics, diagrams, reports, charts and graphs.
Analyses the network model produced by designer;
Recommends the configurations of existing switches (e.g. how many access cards to add) and the optimal locations of new switches/routers;
Shows which links and devices are over and underused;
Predicts link and device throughput and utilisation;
Shows effects of a link or device failure;
Shows how changes in topology, device upgrades or expansion will affect performance.
(b) Considering cost-related issues:
Analyses the status of the current network, evaluates the condition of any user-defined configuration and optimises the expansion of the network based on demand and costs;
Ensures that the network is cost effective, reliable and has sufficient capacity to meet current and expected customer demand.
(v) Investigation of the network performance by modelling and simulation of dynamic traffic behaviour:
Finds out the limitations of the network as designed by increasing traffic load and investigating its performance;
Identifies the applications or protocols contributing the most to the network congestion and delay;
Predicts the response times of applications before deploying the network;
Predicts how many users an application can handle;
Confirms whether the service level agreements can or cannot be met.
Every tool uses its unique native notation to represent a network model. The users of the network design tools are network managers and engineers, network designers, researchers, and the students [ 10 , 11 , 12 , 13 , 14 , 15 , 16 , 17 , 18 , 19 ]. The following are types of network modelling tools available [ 20 , 21 ].
(a) Main design tools:
Analytical tools;
Simulation tools.
(b) Supplementary tools:
Topology generation tools;
Topology discovery tools.
Three of the educational tools are Delite (analytical tool), NS-3(simulation tools) and Brite (topology generation tool). Students can use the Delite for the calculation of the capacity, reliability and delays of the networking module. On the other hand, to see the dynamic behaviours, NS-3 can be used. Finally to know the network topology, BRITE tool case be used.
Students can get clear concepts using topology generation tool(s). They will experiment different topology algorithms using Brite tool. The students can design the topology using menu bar in Brite and it will generate a text file. Students can study the text file and change the parameters. They can design the same model (topology) in Delite tool and perform capacity, reliability and delay analysis using predefine algorithms. Delite also produces the text file and students can edit the file and parameters and perform experiments. And finally they can re-map the same model in NS-3/Ns-2 and check different paraments and dynamic behaviour and conduct performance analysis. For example, in networking course, a full coursework/assessment can be completed using 2 and/or 3 of these tools together based on the requirement of the assessment and the module.
From the assessment point of view, the sequence is:
From the tool point of view, the sequence is:
These tools will also be very useful for the network designer and researcher in their network design process or algorithm development. The use of network modelling and simulation tools is an important element in the process of design, deployment, testing and evaluation of any communications network. Tools are the integral parts of the overall methodology of planning and designing a network. Designers may analyse the output produced by the tools, compare several designs and select the best design according to some predetermined criteria. Tools are also needed to study and test new protocols.
In the following sections, we will discuss details (related files and their format, steps to design network model, etc.) of these 3 tools which are Delite, Ns-3 and Brite. These can be introduced to the students that might be useful for the students to have basic networking concepts.
Features of the Delite, NS-3 and Brite
Delite [ 22 ] is an educational and practical wide area network (WAN) design tool, which can produce network designs of limited size using a set of embedded network design algorithms. Data for such designs have to be read from the specially formatted external files. Delite can produce graphical displays representing network nodes and links as well as some additional analysis data (delay analysis and reliability analysis) in special windows. An input file contains data for the network design problem: node coordinates, link parameters, traffic parameters, as well as cost and equipment specifications.
Delite provides the network planner with a user-friendly menu-driven interface. It uses a 1000 by 1000 unit size window for a square world on the screen for displaying the network model and a separate special type of window called the ‘Delite Monitor’ for user responses and analysed output of the designed network model. The origin of the window is in the top right corner but the distance from it is measured down and to the left, i.e. the opposite way from normal X, Y coordinates. An alternative is to put the origin in the bottom left corner and make all values negative from this origin. Delite supports different types of communication links, which are T1, D96, and D56.
For each network model, Delite produces seven text files:
.INP file contains information that refer to the other files used for generating the network file;
.GEN file contains sites/nodes, their coordinates, type of link and some parameters;
.REQ file contains traffic information (SOURCE, DEST and BANDWIDTH);
.CST file contains tariff information (end to end cost);
PARMS.TBL contains several network parameters (e.g. utilisation, APHA, MESEEEHE_LEN, DUPLIXITY, etc.);
EQUIP.TBL/NOEQUIP.TBL contains equipment information (fixed), specifies the cost and capacity of the equipment that can be placed at every site;
.NET file contains the network topology (e.g. source, sink, node coordinates, etc.). This file receives the necessary information from the.INP file.
The WAN design tool Delite produces a performance report of the network model. The report includes average delays of the link, the average number of hops, link utilisation for every separate link between nodes, utilisation of each node, overall network model utilisation, etc. A separate special window named a ‘Legend’ is used for showing the output.
The algorithms used for designing the topology of a network model supported by Delite are:
The Prim Algorithm;
The Primdijkstra Algorithm;
The Tour Building (The Nearest Neighbour) Algorithm;
The Tour Building (The Farthest Neighbour) Algorithm;
The Esau–Williams Algorithm;
The Sharma Algorithm;
The Multispeed Tree Design Algorithm;
The Nearest Neighbour Esau–Williams Algorithm;
The Multicenter Esau–William Algorithm;
The Mentor Algorithm;
The Incrementour Algorithm.
Files and Model Processing Steps in Delite
There are seven text files in Delite as shown in Fig. 1 . The figure also shows the relationship among the files. The most important for the users are files.gen (original node information, coordinates and available link types) and.net (model node coordinates and additionally a table of links between nodes, i.e. actual network design). Links between nodes can be generated using a few design algorithms. Thus, various designs may have different costs, delays, reliability, average number of hops, etc. Other files are used for different purposes: noeqip.tbl and param.tbl are predefined (used to supply some network parameters), the.cst file describes the costs associated with link types (e.g. T1, T3, D96, etc.), the.req file describes the capacity of each link type, and the.inp file contains the names of files related to a particular model. The users can edit all of the files mentioned above as they are in ASCII text format. The link direction of the arrow between file types means the direction of a “call” for information, e.g. the.net file is only using.inp files and the.inp file is using all others.

Relationship of model files (7 files in total) used in Delite tool
The file processing steps are shown in Fig. 2 . The.gen file is designed and/or edited by the user and fed to the Delite tool. As a consequence,.inp,.cst, and.req files are produced using some parameters from para.tbl or noeqip.tbl files. Finally using these files (.gen,.inp,.cst,.req), the design file (.net) is produced. As the.net file contains the whole network model information, this file is used by the NeDaSE tool for transformation purposes from Delite to other formats. The.cst and.req files are not used for transformation (from Delite to other tools’ formats). This is due to the fact that there is no way to use the data of.cst (all possible combinations of link costs) or.req (all possible combinations of link bandwidths) files in other tools. All of the files are in text format and students can easily change/amend and learn about the parameter and therefore networking issues.

Model processing steps in Delite tool staring with step 1 to step 4 in sequence
The.net file carries the model information. There are three sections in the.net file [ 22 ]. The first section (Fig. 3 ) contains node/site information, coordinate of the nodes with some predefined parameters etc., the second section (Fig. 4 ) contains the topology information and predefined parameters [ 22 ] and the third section contains parameter information (not shown). Furthermore, other files (.cst,.gen,.inp,.req) are also needed to make a model workable in Delite. For this size of thesis, the structures of these files are not provided. Among these files,.cst and.req are two of the biggest files.
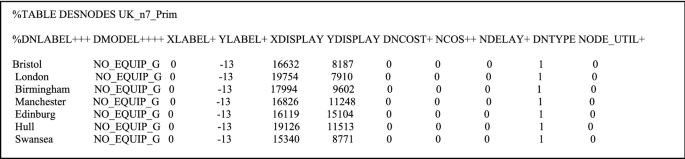
An example of the node information from Prim7UK model in Delite tool showing the nodes details (standard format)
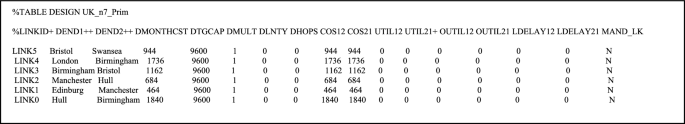
An example of the link information from Prim7UK model in Delite tool showing the link details (standard format)
In.gen file (not shown), there are three sections: node information, used link type, and parameter section. The node section carries the node name, initial node position (before applying any algorithm for a model), parent node, population concerned with a node (number of users), node level (the level of the site in the hierarchy), traffic in (entering the site) and traffic out (leaving the site) of each node. The second section contains link types that are to be used and their associated information, and the third section contains several parameters.
The traffic file.req contains the capacity of each of the possible links. These possible links are basically the links (combination) from each node to rest of the nodes of the model. If there are n nodes, then the total number of links with a bandwidth of the.req is (( n – 1) + ( n – 2) + … + ( n – n )).
The file.cst contains the costs of all of the links available for the design. If there are n nodes then there will be n + ( n – 1) + ( n – 2) + ··· + ( n – n ) links in this.cst file.
The file para.tbl (predefined and used as a template) contains information to guide the design process.
The file noeqip.tbl/eqip.tbl (also predefined and used as a template) describes equipment, e.g. multiplexers, routers including the cost and capacity of the equipment that can be placed at every site [14], p403]. This specifies the throughput of the equipment and the number of lines that can be terminated. The throughput for data switches is usually measured in packets/seconds, and the voice switches are measured in call setups/seconds.
Finally, the.inp file contains the names of all of these files.
Network Model in Delite
Features of the network Delite model are:
By default, the nodes are labelled with N1, N2, N3 and so on. The first node starts labelling with 1 rather than 0.
The location of the node is represented by x, y coordinates.
It supports text format for a node name that may have more than one word (e.g. United States).
The minimum coordinates of the square world (visualisation) of the Delite are in the left-down corner and the maximum are in the right top corner of the window/screen (shown in Fig. 5 ).
The number of nodes is limited to 100.
The.net model is designed from the.gen file. During the editing of the.net file, the node locations can be changed by the designer. Thus, the coordinates of a node may be different in.gen and.net files. Thus, in the case of transforming other models (e.g. ns-3) to the Delite model, it is necessary to generate both.gen and.net files.

Coordinate system of the Delite Model (GUI) showing the maximum and minimum points
The links of a model are duplex.
Does not allow for specifying the use of the communication protocols.
Visualisation
The visualised location of the node is always the same.
No animation is supported.
In the.net/.gen file, there are a lot of parameters that are used for the calculation of different factors (e.g. delay analysis, traffic analysis, reliability analysis, etc.).
Has to be fitted within 1000 by 1000 “square world”.
Performance analysis is done by this tool.
The models designed by the users are confined within the predefined algorithms allowed by the tool.
Figure 5 shows the visualisation screen of the Delite tool. The left lower side is the minimum points (0,0) and right upper corner is the maximum point/coordinate (1000, 1000) of the display.
NS-3 [ 23 , 24 ] network simulator, a VINT (Virtual Inter-Network Testbed) project from U.C. Berkeley/LBL/Xerox PARC, is a discrete event simulator targeted at network research, which provides substantial support for the simulation of TCP, routing and multicast protocols. The simulator is written in C + + and uses a Tcl/Otcl as a command and configuration interface. The ns-3 has the advantage that it provides numerous frameworks as the basis for extending its core capabilities. Ns-3 is derived from REAL (Realistic and Large), which is derived from NEST (Network Simulator testbed).
In ns-3, arbitrary network topologies, composed of routes, links and shared media can be defined. A rich set of protocols (e.g. TCP, TCP/Reno, TCP/Newreno, TCP/Sack1, TCP/Fack, TCP/FullTcp, TCP/Vegas, TCP/Vegas/RBP, TCP/Vegas/RBP, TCP/Asym, TCP/Reno/Asym, TCP/Newreno/Asym, TCPSink, TCPSink/DelAck, TCPSink/Asym, TCPSink/Sack1, TCPSink/Sack1/DelAck, UDP, RTP, RTCP, LossMonitor, IVS/Source, IVS/Receiver, CtrMcast/Encap, CtrMcast/Decap, Message, Message/Prune, SRM, SRM/Adaptive, Tap, Null, RtProto/DV) are available and various types of applications can be simulated. Among them are FTP, Telnet, and HTTP, which use TCP as the underlying transport protocol and applications requiring a constant bit rate (CBR) traffic pattern, Ih use the UDP transport protocol. Multiple queuing and scheduling policies can be configured such as drop tail (DropTail), random early detect (RED), explicitly congestion notification (ECN), priority and fair queuing. The simulator is event-driven and runs in a non-real time fashion. Packet losses are simulated by buffer overflows in routers, which is also the dominant way packets get lost in the Internet. There is also support for error models other than losses through buffer overflow. The routing model can be static or dynamic. The link state and distance vector routing algorithms are supported.
The network topology is specified by describing the network nodes and edges [ 25 ]. The network model represents the interconnection of network elements, hereafter called nodes. It consists of nodes and links shown in Fig. 6 .
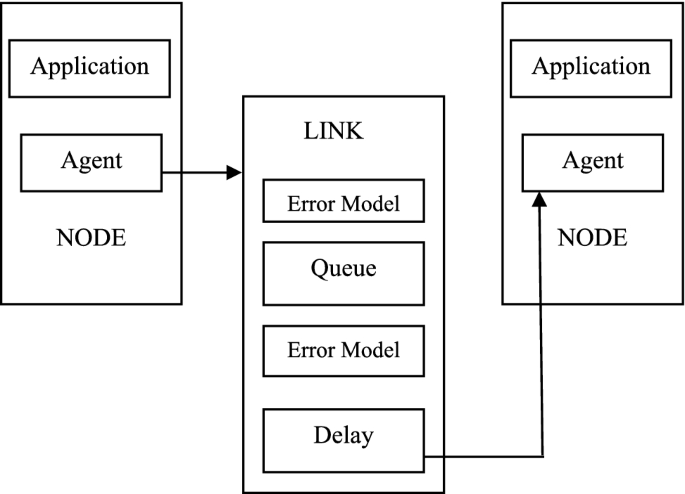
The ns-3 Network Model
In ns-3 model, single or multiple traffic generators, including statistical generators and other typical generators, such as FTP and Telnet, can be attached to any node. In addition, network and transport protocol behaviours are simulated by attaching the appropriate agents to the interested nodes. Examples of routing agents include the ones supporting static routing (Dijkstra’s SPF algorithm), dynamic routing (Distance Vector Algorithm) or multicast routing. Examples of the transport agent include the TCP agent and the UDP agent. Links are modelled on either the simplex link or duplex link with a predefined capacity, delay and queuing discipline. In addition, links can be torn down or restored at any point in time duration the simulation, simulating link failures.
ns-3 has some shortcomings [ 26 , 27 ]:
The design of ns-3, using the hybrid of Tcl, otcl and C languages leads to memory consumption in many cases;
The IP address concept is not used;
Alpha quality;
Minimal documentation;
Incomplete API;
ns-3 has no direct support for mobility or shared wireless radio channels.
Files and Model Processing Steps in ns-3
There are four files (see in Fig. 7 ) in ns-3 whose processing steps in the tool are shown in Fig. 8 . The.ns and.tcl are input files, and.nam and.tr (trace file) are the output files. The.ns or.tcl file is given to the ns-3 tool as an input and the.nam (and/or.tr) file is produced. The.tr file can be used for post-processing. This nam file is animated by the nam animator which again can produce a.ns file. Initially, the student will prepare a.ns/.tcl script for the network model using tool command language. If students are unfamiliar, then s/he can use GUI in nam animator and design the network model (drag and drop). In this case, the Nam animator will generate a.ns file automatically and the student can open and see the code(s) of the file (text format) and learn. Then the model can be execute by the nam which will execute the codes and simulate the model.

Relationship of model files used in ns-3 tool that shows the linkage between the input/output files

Model processing steps in ns-3 showing how to create a tcl/.ns file and simulate in Nam staring with step 1a and ending at 3b
The main file format that works behind different kinds of network topologies in the ns-3 tool is shown in this section. The ns-3 file (.ns) normally has six types of information which are; node information (Fig. 9 ), topology information (Fig. 10 ), protocols (agent) (Fig. 11 ), data source (application) (Fig. 12 ), connection (agent to agent) (Fig. 13 ) and simulation timing information (Fig. 14 ). Details can be found in this reference[ 15 ]. Users can write the code using TCL (Tool Command Language) scripting language to design the network model and execute the code that need to have these six types of information. Alternatively, using the NAM animator, user can design the model using Manu bar and tools. In this case, the code(s) will be generated automatically in background for the user. The.ns file is a text file and students can easily change/amend and learn about the parameter(s) and, therefore, networking issues.

Node information of the.ns file showing the node name and coordinates

Link information of the.ns file between the nodes, link type

Agent information of the.ns file showing the transport protocols

Traffic information of the.ns file showing the application protocols
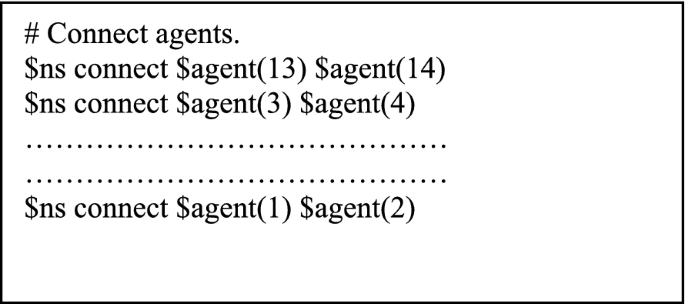
Agent Connection information of the.ns file showing the source and sink of the linkage

Simulation Time information of the.ns file showing the start of packet sending and duration of the simulation
In the node information section (Fig. 9 ), Node/site name(s), coordinates (x, y, z) of the nodes are codes. Link section (Fig. 10 ) depicts the linkage between nodes/sites, link type (simplex, duplex), queue algorithm, etc. Agent section (Fig. 11 ) covers the transmission protocol (TCP, UDP etc.), packet size, window size etc. Traffic section (Fig. 12 ) shows the application protocols, linkage with the agents, time interval to pass the packets etc. Agent connection section (Fig. 13 ) interlinks between the agents (source and sink). Finally Simulation Time section (Fig. 14 ) shows when the agent will start sending the traffic and how long simulation will continue.
Network Model in ns-3
Features of the network model in ns-3 are:
The location of the node is in 3D view. That is, each node has coordinates with the 3- dimensions (x, y, z). However, the value of the z coordinate is always 0.
Node/site name must be one word (e.g. ‘London’, ‘USA’, etc.).
The minimum coordinates of the nam (visualisation tool) of the ns-3 are in the left-down corner and the maximum are in the right top corner of the window (see in Fig. 15 ).
Medium scale network simulation tool.

Coordinate system of the tool Nam (GUI) animator showing minimum and maximum points
The.ns formatted file supports only the simplex link, whereas the.tcl formatted file supports both a simplex and duplex link.
Visualisation of the node in ns-3 starts with 0, 1, 2… and so on. The first node is numbered 0 rather than 1.
Models designed by the users are not confined within the predefined topological model/algorithm.
The notation of the.ns file (fixed style of notation for node name, agent name, traffic source name) and.tcl file are slightly different. The.tcl file supports any text names of a node, agent, or traffic source. On the contrary, the.ns file supports only a particular format.
ns-3 supports several types of communication protocols.
ns-3 model can be animated by the network animator nam.
The network animator has a graphical editor in which locations of the nodes visualised are always the same. However, during execution of the.nam file, this is not the case.
There is no performance analysis information defined in the ns-3 model file as well as nothing is stored in the trace files (.nam/.tr).
Produces a trace file (optional). The contents of the trace file are of the same type as the.nam file.
No performance analysis is done.
Figure 15 shows the visualisation screen of the nam tool. The left lower side is the minimum points and right upper corner is the maximum point/coordinate of the display.
Brite [ 25 ] is a generator based on the AS power-laws. Furthermore, BRITE also incorporates recent findings on the origin of power-laws and observations of skewed network placement and locality in network connections on the Internet. By studying a number of existing topology generators, the authors of BRITE claim that the preferential connectivity and incremental growth are the primary reasons for power-laws on the Internet. For completeness, topologies are generated that incorporate both skewed node placement and locality in network connections as well as topologies with just incremental growth and preferential connectivity. To generate a topology on a plane, the plane is first divided into HSxHS squares, then the number of nodes in each square is assigned according to the placement, NP which is either a uniform random distribution or a bounded Pareto distribution. The bounded Pareto distribution gives a skewed node placement where a non-negligible number of squares have a large number of nodes in them. Each square is further divided into LSxLS smaller squares and the assigned nodes are then uniformly distributed among the smaller squares. A backbone node is selected from each of the top-level squares populated with nodes and a spanning tree is formed among the backbone nodes. Nodes are then connected one at a time to nodes that are already connected to the backbone. A new node can have preferential connectivity (PC) in its choice of neighbouring nodes: locality based, outdegree based or both. The locality-based preferential connectivity uses a Waxman probability function to connect nodes in the topology. In outdegree-based preferential connectivity, the probability of a new node connecting to an existing node is the ratio of the existing node’s outdegree over the sum of all outdegrees of nodes in the connected network. Finally, when mixing both locality-based and outdegree-based preferential connectivity, the probability of connecting to an existing node under outdegree-based preferential connectivity is weighted by the Waxman probability between the new node and the existing node. Each new node introduces new links.
Files and Model Processing Steps in Brite
There are two text files in Brite whose processing steps are shown in Fig. 16 below. The configuration file (text file) is provided as input to the Brite and a model file is produced accordingly. Input can also be given graphically using the GUI of the tool. An input file can also be imported from other tools (e.g. Inet). The student/user provide the configuration parameter (GUI) or Topology file (from other topology generation tool) can be feed to Brite and Brite tool general the.Brite file. The user analyses the file and will have understanding of the topology concept.

Model processing steps in BRITE to design a model starting with 1a and ending at 2
The main file format that works behind different kinds of network topologies in the Brite tool is shown in Fig. 17 as a sample [ 26 ]. This is basically the.brite file (output file) that can be produced manually or from a configuration file (input). There are three sections that carry model information, node information (node number/label, coordinate) and topology information (source, sink and some parameters) respectively (details can be found in [ 26 ]). The configuration file is not shown.

The structure of the Brite file that shows the node and link information
Network Model in Brite
Features of the network model in Brite are:
The location of the node is 2D. That is, each node has the coordinate with values of x and y. There is no z coordinate.
The nodes are labelled with 0, 1, 2, 3 and so on. The first node starts with label 0 rather than 1.
The model does not work without the values of coordinates.
Large-scale network topology generator.
Generates a small backbone, with nodes placed:
randomly or
concentrated (skewed)
The links of a model in Brite are duplex.
The new node has a constant number of edges connected using:
preferential connectivity and/or
Brite does not support any communication protocol.
No trace file is produced.
It has no visualisation tool of its own.
Node name, link name, etc. are denoted by numbers rather than in text.
Contains eight different generation models: flat router models (Router Waxman, Router Barabasi), Flat Autonomous System (AS) models (AS Waxman, AS Barabasi), Imported file models (BRITE 1.0, GT-ITM, NLANR, Inet, SKITTER), Hierarchical Top-Down model, Hierarchical Bottom up model.
Add nodes one at a time (incremental growth).
To generate a topology on a plane, the plane is first divided into HSxHS squares, then the number of nodes in each square is assigned according to the node placement (NP), which is either a uniform random distribution or a bounded Pareto distribution. Each square is further divided into LSxLS smaller squares.
Two files are related to BRITE models: one configuration file (input file), and one output file. These files are structured with a fixed format and keywords.
The Table 1 shows the main characteristics and complementary features of three selected tools. After extensive research on these education tools these features (summary) have been found. Brite is used for LAN, MAN, WAN. On the other hand, Delite and NS are used for WAN design. Brite and Delite do not show the dynamic behaviour, whereas NS is used to visualise the dynamic behaviour of a network model. Please see the Table 1 for other features. If these three education tools are used in teaching the computer networking course, students will be benefitted and learn how to design and analyse a network model along with research.

Conclusions
We have presented by examples the benefit of using modelling and simulation tools in computer network courses. We have shown the use of the network simulation and design tools for teaching, their main features, internal file structure, format, relationship between files and file processing systems, how to design the network model and learn, default features of the tools, etc. However, using hands-on projects, students will see themselves in different (as designers); where, in those moments, they integrate their minds, critical thinking, communication skills, and their cumulative knowledge in the domain to provide solutions to their problems. Moreover, this approach will enable faculty to notice and consider all issues facing students when they apply the selected tools to solve their real-world like problems.
“Pilot” tools for the teaching are Delite, network simulator ns-3, topology generator Brite. We have shown the technical issues how these tools are used to design a network model and the format of the input and output files that a user/student needs to study to know/clarify the ideas of the network models. To clear the idea of the topology, students will use the Brite tools. To analysis the network models student can use the Delite tools and full analysis details can be found in [ 14 ]. To visualise the dynamic behaviours of network models (e.g. packet passing, packet loss, queuing, etc.), the NS-2/NS-3 tool would be very beneficial.
Brite generates the small as well as very large topologies. It helps to design eight types of different network models [ 17 , 18 , 19 , 20 , 21 , 22 , 23 , 24 , 25 , 26 ]. Also, models from some of the other tools (e.g. GT-IMT, Inet, Skitter, NLANR, etc.), can be fed into the Brite tool. Additionally, the output of Brite can be transformed into SSF, J-Sim, Otter, ns formats. There are great advantages of using this tool, i.e. the use of Brite means use of the other compatible tools along with Brite.
Delite is a network modelling tool that has analysis capability and predefined algorithms. Delite helps to design and analyse a network model in addition to the uses of the predefined algorithms. Delite tool can be used to teach the calculation of the Capacity, reliability and delays of the networking module. To see the dynamic behaviours, NS-3 can be used in the classroom. Finally to know the network topology, BRITE tool case be used. We found one article regarding the tools for teaching network [ 3 , 4 , 5 , 6 , 7 ].
The ns-3 (.ns) does not allow any other words rather than a set of predefined keywords. In Brite, the site name (text) is not allowed and the site is indicated only by an id number. In contrast, Delite and .tcl (ns-3) allow a user-defined site name (text). In all cases, files are structured in such a way that particular data must be placed in a fixed column having spaces in a fixed manner. ns-3 simulates the dynamic behaviour of a protocol. It can simulate most of the protocols from the TCP/IP family. Additionally, it produces a trace file which can be analysed using the post-processing utilities. Another advantage is that the user can produce a model file using either a GUI or writing code (tcl script). The editor of ns-3 (nam) is very flexible for the naive as well as expert users. In addition, new protocols can be embedded into ns-3 and tested as the tool has open source code.
This article provides issues and techniques of three computer network modelling and simulation tools for teaching Computer Networks. The theoretical concepts are rather abstract in networking subject, and students often find them too obscure to understand, many authors attempt to answer the question on how to improve students’ motivation and interest for the complex teaching material of computer networking [ 7 ]. Our investigation suggests that the designs could be started by building the network topology using Brite, then gradually students are advised to add more capabilities and features to their designs such as adding links-performance, choosing right applications (using Delite), and add more advanced features such bandwidth, packet dropping, various queuing mechanisms, build special networking model between some sites in the network and quality of service (QOS) parameters to their designs (using NS).
Data availability
All the codes, models and required information are available on request.
Atila B. Teaching computer networks: theory and problem solving. J Adv Comput Netw. 2015;3(4):299–302.
Article Google Scholar
Jiang D, Song H, Rong HW. Simulation tools and techniques for communications and networking. Mob Netw Appl. 2021. https://doi.org/10.1007/s11036-021-01746-0 .
Vandana K. A study of research tools and techniques in network congestion control. Int J Eng Res Technol (IJERT). 2014;3(2):6–10.
Yongbin Z, Ronghua L, Huiling M. teaching innovation in computer network course for undergraduate students with packet tracer. IERI Proce. 2012;2(2012):p504-510.
Google Scholar
Antonio R, Fernando P, Rafael M, Pedro MR, Antonio FS. Teaching advanced concepts in computer networks: VNUML-UM virtualization tool. IEEE Trans Learn Technol. 2013;6(1):85–96.
Marina P, Julije O. Methods in teaching computer networks: a literature review. ACM Trans Comput Educ. 2020;20(3):1–35. https://doi.org/10.1145/3394963 . ( Article No.: 19 ).
Azeddien MS, Mohamed J. Using simulation and modeling tools in teaching computer network courses. In: International Conference on IT Convergence and Security (ICITCS), Macao, China, 6–18 Dec 2013.
Perc M. High-performance parallel computing in the classroom using the public goods game as an example. Eur J Phys. 2017;38: 045801.
Silva PHO, et al. Graphical interface as a teaching aid for nonlinear dynamical systems. Eur J Phys. 2018;39:065105.
Article MATH Google Scholar
Arnold W. Teaching complex ideas: how to translate your expertise into great instruction. New York: Routledge; 2019. ( ISBN: 9781351058117 ).
Pakstas A. Reliability issues in network planning. In: Proceedings of the 8th International Conference on Telecommunications, ConTEL, Zagreb, Croatia, 15-17 June, 2005.
Ping W, Raed S. Using a team project in teaching computer networking and data communication. Issues Inf Syst. 2020;21(2):167–77.
Rashid NA, Othman Z, Johan R, Sidek SFH. Cisco Packet Tracer simulation as effective pedagogy in computer networking course. Int J Interact Mob Technol (iJIM). 2019;13(10):4–18. https://doi.org/10.3991/ijim.v13i10.11283.-5 .
Zhamanov A, Yoo S, Sakhyeva Z, Zhaparov M. Implementation and evaluation of flipped classroom as IoT element into learning process of computer network education. Int J Inf Commun Technol Educ. 2018;14(2):30–47.
Noor NM, Yayao N, Sulaiman S. Effectiveness of using cisco packet tracer as a learning tool: a case study of routing protocol. Int J Inf Educn Technol. 2018;8(1):11–6.
Elias MS, Ali AZM. Survey on the challenges faced by the lecturers in using Packet Tracer simulation in computer networking course. Proc Soc Behav Sci. 2014;131(2014):11–5.
Rocky KC, Chang, HK. Teaching computer networking with the help of personal computer networks. Proceedings of the 9th Annual SIGCSE conference on innovation and technology in computer science educationIn, ITiCSE’04, Leeds, United Kingdom, p 208–212, June 28–30, 2004.
Richard VS. Network planning and design. Polytechnic University, New York. Revised 21 Jan 2001. https://studylib.net/doc/14653654/network-planning-and-design-by-richard-van-slyke-polytech . Accessed 2 Mar 2023.
Arnold WB. Which network design tool is right for you? IT Professional 2000;2:23–31. https://doi.org/10.1109/6294.877494
Rahman MA, Algirdas P, Frank ZW. Network modelling and simulation tools, simulation modelling practice and theory. Int J Fed Eur Simul Soc EUROSIM. 2009;17(6):1011–31.
Rahman MA, Algirdas P, Frank ZW. An integrated environment for network design and simulation. In: Sobh T, Elleithy K, Mahmood A, Karim M, editors. Advances in computer, information, and systems sciences, and engineering. Springer Publication; 2006. p. 316–22.
Chapter Google Scholar
Cahn RS. Wide area network design: concepts and tools for optimization. San Francisco: Morgan Kaufman Publishers; 1998.
Kevin F, Kannan V. The ns Manual. The VINT Project, 23 May 2006. http://www.isi.edu/nsnam/ns/doc/ns_doc.pdf . Accessed 2 Mar 2023.
Deborah E, Mark H. Network Visualization with Nam, the VINT Network Animator Computer 33(11):p63–68, 2000. https://doi.org/10.1109/2.881696 , Source: IEEE Xplore.
Alberto M, Anukool L, Ibrahim M, John B. BRITE: an approach to universal topology generation. modeling, analysis and simulation of computer and telecommunication systems, 2001.In: Proceedings. Ninth International Symposium, Feb 2001. https://doi.org/10.1109/MASCOT.2001.948886 .
Riley GF. The Georgia tech network simulator. In: Proceedings of the ACM SIGCMM 2003 Workshops, Germany, 2003, pp 5–12, Aug. 2003. https://doi.org/10.1145/944773.944775 . Accessed 2 Mar 2023.
Srivastava M, Partho M, Prathima A, Nguyen G. Ethersim: a simulator for application-level performance modeling of wireless and mobile ATM networks. Comput Netw ISDN Syst. 1998;29:2067–90.
Download references
Author information
Authors and affiliations.
Cardiff School of Technologies, Cardiff Metropolitan University, Western Avenue, Cardiff, CF5 2YB, UK
Muhammad Azizur Rahman
Communications Software Engineering, Vilnius University, Universiteto g. 3, 01513 Vilnius, Lithuania
Algirdas Pakstas
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Muhammad Azizur Rahman .
Ethics declarations
Conflict of interest.
The authors would like to declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Cyber Security and Privacy in Communication Networks” guest edited by Rajiv Misra, R K Shyamsunder, Alexiei Dingli, Natalie Denk, Omer Rana, Alexander Pfeiffer, Ashok Patel and Nishtha Kesswani.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Rahman, M.A., Pakstas, A. Tools and Techniques for Teaching and Research in Network Design and Simulation. SN COMPUT. SCI. 4 , 269 (2023). https://doi.org/10.1007/s42979-023-01684-6
Download citation
Received : 20 October 2022
Accepted : 10 January 2023
Published : 17 March 2023
DOI : https://doi.org/10.1007/s42979-023-01684-6
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Network simulation
- Find a journal
- Publish with us
- Track your research
Information
- Author Services
Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Journal Proposal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Article Menu
- Subscribe SciFeed
- Recommended Articles
- Google Scholar
- on Google Scholar
- Table of Contents
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
JSmol Viewer
Computer network simulation with ns-3: a systematic literature review.

1. Introduction
2. related work, 3. slr process.
- Reporting the results
3.1. SLR Target
3.2. slr protocol, 4. research questions.
- RQ1: which are the impacted application domains, according to the literature?
- RQ2: how easily extensible did ns-3 prove to be with respect to its adaptation to new domains or uses?
- RQ1.1: what kind of network technologies have been simulated?
- RQ1.2: which are the related application field? (e.g., medicine, astrology, ...)
- RQ1.3: what kind of problems have been addressed?
- RQ2.1 Is it a new extension or module?
- RQ2.2 Does it use an external module or extension?
5. Review Methods
5.1. data source and search strategy, the wns3 workshop on ns-3, 5.2. selection criteria, 5.3. data extraction form.
- the first part collects all general information about the paper, as from Table 7 ;
- the second part collects the information that is more related with the research questions, to address the research questions (see Table 8 ): - for RQ1 the questions characterize the field in which ns-3 is used in terms of networks technologies, area of application and kind of problem; - for RQ2 the answers are binary (yes/no), and describe if the paper presents a new module or extension for ns-3 and if it uses an already existing module.
6.1. Included and Excluded Studies
6.2. data synthesis, 7. conclusions and future works, author contributions, acknowledgments, conflicts of interest.
- Riley, G.F.; Henderson, T.R. The ns-3 Network Simulator. In Modeling and Tools for Network Simulation ; Wehrle, K., Güneş, M., Gross, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 15–34. [ Google Scholar ] [ CrossRef ]
- Barisic, A.; Amaral, V.; Goulao, M. Domain-Specific Language Domain Analysis and Evaluation: A Systematic Literature Review ; Technical Report; Faculdade de Ciencias e Tecnologia, Universidade Nova de Lisboa: Colombia, Portugal, 2015. [ Google Scholar ] [ CrossRef ]
- Piro, G.; Grieco, L.A.; Boggia, G.; Camarda, P. Nano-Sim: Simulating Electromagnetic-Based Nanonetworks in the Network Simulator 3. In Proceedings of the 6th International ICST Conference on Simulation Tools and Techniques, Cannes, France, 6–8 March 2013; ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering): Brussels, Belgium, 2013; pp. 203–210. [ Google Scholar ]
- Raman, A.; Chou, K.; Mastorakis, S. A simulation framework for Peer-to-Peer file sharing in named data networking. In Proceedings of the 2019 Workshop on ns-3, Florence, Italy, 18–21 June 2019; pp. 57–64. [ Google Scholar ]
- Bakshi, S.; Tahiliani, M.P. Recent Acknowledgement Support for ns-3 TCP. In Proceedings of the 2019 Workshop on ns-3, Florence, Italy, 18–21 June 2019; pp. 9–16. [ Google Scholar ]
- Rohrer, J.; Mauldin, A. Implementation of epidemic routing with IP convergence layer in ns-3. In Proceedings of the 10th Workshop on ns-3, Mangalore, India, 13–14 June 2018; ACM: New York, NY, USA, 2018; pp. 69–76. [ Google Scholar ]
- Mittal, V.; Jain, V.; Tahiliani, M.P. Proportional Rate Reduction for ns-3 TCP. In Proceedings of the 10th Workshop on ns-3, Mangalore, India, 13–14 June 2018; ACM: New York, NY, USA, 2018; pp. 9–15. [ Google Scholar ]
- Selinis, I.; Katsaros, K.; Vahid, S.; Tafazolli, R. Exploiting the capture effect on DSC and BSS color in dense IEEE 802.11ax deployments. In Proceedings of the Workshop on ns-3, Porto, Portugal, 13–14 June 2017; ACM: New York, NY, USA, 2017; Volume Part F128360, pp. 47–54. [ Google Scholar ]
- Fontes, H.; Campos, R.; Ricardo, M. A trace-based ns-3 simulation approach for perpetuating real-world experiments. In Proceedings of the Workshop on ns-3, Porto, Portugal, 13–14 June 2017; ACM: New York, NY, USA, 2017; Volume Part F128360, pp. 118–124. [ Google Scholar ]
- Franchi, M.; Pecorella, T.; Ridolfi, A.; Fantacci, R.; Allotta, B. Kinematic constraints and ns-3 mobility models: The AUV issue. In Proceedings of the Workshop on ns-3, Porto, Portugal, 13–14 June 2017; ACM: New York, NY, USA, 2017; Volume Part F128360, pp. 103–109. [ Google Scholar ]
- Ford, R.; Zhang, M.; Dutta, S.; Mezzavilla, M.; Rangan, S.; Zorzi, M. A framework for end-to-end evaluation of 5G mmWave cellular networks in ns-3. In Proceedings of the Workshop on ns-3, Seattle, WA, USA, 15–16 June 2016; Volume Part F132163, pp. 85–92. [ Google Scholar ]
- Dandoush, A.; Tuholukova, A.; Alouf, S.; Neglia, G.; Simoens, S.; Derouet, P.; Dersin, P. ns-3 Based framework for simulating Communication Based Train Control (CBTC) systems. In Proceedings of the Workshop on ns-3, Seattle, WA, USA, 15–16 June 2016; Volume Part F132163, pp. 116–123. [ Google Scholar ]
- Lehmann, A.; Kreuzer, M.; Deutschmann, J.; Berold, U.; Huber, J. Topology simulation for aeronautical communication protocols with ns-3 and DCE. In Proceedings of the Workshop on ns-3, Seattle, WA, USA, 15–16 June 2016; Volume Part F132163, pp. 132–138. [ Google Scholar ]
- Hood, C.; Riley, G. On predicting the performance characteristics of the NS-3 distributed simulator for scale-free internet models. In Proceedings of the 2015 Workshop on ns-3, Castelldefels, Spain, 13–14 May 2015; ACM: New York, NY, USA, 2015; pp. 54–59. [ Google Scholar ]
- Conceicao, S.; Ribeiro, F.; Campos, R.; Ricardo, M. Novel NS-3 model enabling simulation of electromagnetic wireless underground networks. In Proceedings of the 2015 Workshop on ns-3, Castelldefels, Spain, 13–14 May 2015; ACM: New York, NY, USA, 2015; pp. 9–16. [ Google Scholar ]
- Gupta, R.; Bachmann, B.; Ford, R.; Rangan, S.; Kundargi, N.; Ekbal, A.; Rathi, K.; Sanchez, M.; De La Oliva, A.; Morelli, A. Ns-3-based real-time emulation of LTE testbed using LabVIEW platform for software defined networking (SDN) in CROWD project. In Proceedings of the 2015 Workshop on ns-3, Castelldefels, Spain, 13–14 May 2015; ACM: New York, NY, USA, 2015; pp. 91–97. [ Google Scholar ]
- Cerqueira, T.; Albano, M. RoutesMobilityModel: Easy realistic mobility simulation using external information services. In Proceedings of the 2015 Workshop on ns-3, Castelldefels, Spain, 13–14 May 2015; ACM: New York, NY, USA, 2015; pp. 40–46. [ Google Scholar ]
- Newton, B.; Aikat, J.; Jeffay, K. Simulating large-scale airborne networks with NS-3. In Proceedings of the 2015 Workshop on ns-3, Castelldefels, Spain, 13–14 May 2015; ACM: New York, NY, USA, 2015; pp. 32–39. [ Google Scholar ]
- Gómez, D.; Rodríguez, E.; Agüero, R.; Muñoz, L. Reliable communications over wireless mesh networks with inter and intra-flow network coding. In Proceedings of the 2014 Workshop on ns-3, Atlanta, USA, 7 May 2014. [ Google Scholar ]
- Tariq, M.; Swenson, B.; Narasimhan, A.; Grijalva, S.; Riley, G.; Wolf, M. Cyber-physical co-simulation of smart grid applications using NS-3. In Proceedings of the 2014 Workshop on ns-3, Atlanta, GA, USA, 7 May 2014. [ Google Scholar ]
- Zugno, T.; Polese, M.; Lecci, M.; Zorzi, M. Simulation of Next-generation Cellular Networks with ns-3: Open Challenges and New Directions. In Proceedings of the 2019 Workshop on Next-Generation Wireless with ns-3, Florence, Italy, 19 June 2019; ACM: New York, NY, USA, 2019; pp. 38–41. [ Google Scholar ]
- Gawłowicz, P.; Baldo, N.; Miozzo, M. An extension of the ns-3 LTE module to simulate fractional frequency reuse algorithms. In Proceedings of the 2015 Workshop on ns-3, Castelldefels, Spain, 13–14 May 2015; ACM: New York, NY, USA, 2015; pp. 98–105. [ Google Scholar ]
- Tian, L.; Šljivo, A.; Santi, S.; De Poorter, E.; Hoebeke, J.; Famaey, J. Extension of the IEEE 802.11 ah ns-3 Simulation Module. In Proceedings of the 10th Workshop on ns-3, Mangalore, India, 13–14 June 2018; ACM: New York, NY, USA, 2018; pp. 53–60. [ Google Scholar ]
- Bojovic, B.; Abrignani, M.D.; Miozzo, M.; Giupponi, L.; Baldo, N. Towards LTE-Advanced and LTE-A Pro Network Simulations: Implementing Carrier Aggregation in LTE Module of ns-3. In Proceedings of the Workshop on ns-3, Porto, Portugal, 13–14 June 2017; ACM: New York, NY, USA, 2017; pp. 63–70. [ Google Scholar ]
- Rahman, M.U.; Rehman, A.U.; Liu, H.; Chen, H.F. Inhibitory mechanism of 5-bromo-3-indoleacetic acid for non-structural-3 helicase hepatitis C virus with dynamics correlation network analysis. Comput. Biol. Chem. 2018 , 77 , 167–177. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Kwo, P.Y.; Lawitz, E.J.; McCone, J.; Schiff, E.R.; Vierling, J.M.; Pound, D.; Davis, M.N.; Galati, J.S.; Gordon, S.C.; Ravendhran, N.; et al. Efficacy of boceprevir, an NS3 protease inhibitor, in combination with peginterferon alfa-2b and ribavirin in treatment-naive patients with genotype 1 hepatitis C infection (SPRINT-1): An open-label, randomised, multicentre phase 2 trial. Lancet 2010 , 376 , 705–716. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Xu, L.; Wang, X.; Shen, J. Strategy and simulation of trust cluster based key management protocol for ad hoc networks. In Proceedings of the 2009 4th International Conference on Computer Science & Education, Nanning, China, 25–28 July 2009; pp. 269–274. [ Google Scholar ]
- Yu, F.; Jain, R. A Survey of Wireless Sensor Network Simulation Tools ; Washington University: St. Louis, MO, USA, 2011; pp. 1–10. Available online: https://www.cse.wustl.edu/~jain/cse567-11/ftp/sensor/ (accessed on 3 September 2019).
- Pereira, R.M.; Ruiz, L.B.; Ghizoni, M.L.A. MannaSim: A NS-2 extension to simulate wireless sensor network. In Proceedings of the ICN 2015, Barcelona, Spain, 19–24 April 2015; p. 107. [ Google Scholar ]
- Wang, Z.; Feng, X.; Qin, H.; Guo, H.; Han, G. An AUV-Aided routing protocol based on dynamic gateway nodes for underwater wireless sensor networks. J. Internet Technol. 2017 , 18 , 333–343. [ Google Scholar ] [ CrossRef ]
- Melo, R.; Polisciuc, R.; Nogueira, M.; Santos, A. Access Decision System for Seamless Connectivity in Heterogeneous Wireless Networks. In Proceedings of the 2015 XXXIII Brazilian Symposium on Computer Networks and Distributed Systems, Vitoria, Brazil, 18–22 May 2015; pp. 60–69. [ Google Scholar ] [ CrossRef ]
- Maygua-Marcillo, L.; Urquiza-Aguiar, L.; Paredes-Paredes, M. Creating a New Model in NS3 Network Simulator. Preprints 2019 , 1–5. [ Google Scholar ] [ CrossRef ]
- Wang, Y.; Jiang, Y.N.; Ma, Q.; Tian, C.; Bai, B.; Zhang, G. RDMA load balancing via data partition. In Proceedings of the 2019 28th International Conference on Computer Communication and Networks (ICCCN), Valencia, Spain, 29 July–1 August 2019; pp. 1–8. [ Google Scholar ] [ CrossRef ]
- Ayaida, M.; Messai, N.; Najeh, S.; Boris Ndjore, K. A Macroscopic Traffic Model-based Approach for Sybil Attack Detection in VANETs. Ad Hoc Netw. 2019 , 90 , 101845. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Abbas, M.; Song, W.C. THERA: Two-level hierarchical hybrid road-aware routing for vehicular networks. KSII Trans. Internet Inf. Syst. 2019 , 13 , 3369–3385. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Eder-Neuhauser, P.; Zseby, T.; Fabini, J. Malware propagation in smart grid networks: Metrics, simulation and comparison of three malware types. J. Comput. Virol. Hacking Tech. 2019 , 15 , 109–125. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Fogwell, T.; Ochola, E. Comparison analysis of AODV and DSR under attack by black hole nodes in a NS3 simulation. In Proceedings of the International Conference on Cyber Warfare and Security, Stellenbosch, South Africa, 28 February–1 March 2019; pp. 574–587. [ Google Scholar ]
- Bhattacharya, H.; Chattopadhyay, S.; Chattopadhyay, M. NS3 Based HDFS data placement algorithm evaluation framework. In Proceedings of the 2017 International Conference on Computer, Electrical & Communication Engineering (ICCECE), Kolkata, India, 22–23 December 2017; pp. 1–8. [ Google Scholar ] [ CrossRef ]
- Anadu, D.; Mushagalusa, C.; Alsbou, N.; Abuabed, A. Internet of Things: Vehicle collision detection and avoidance in a VANET environment. In Proceedings of the 2018 IEEE International Instrumentation and Measurement Technology Conference (I2MTC), Houston, TX, USA, 14–17 May 2018; pp. 1–6. [ Google Scholar ] [ CrossRef ]
- Tiennoy, S.; Saivichit, C. Using a Distributed Roadside Unit for the Data Dissemination Protocol in VANET with the Named Data Architecture. IEEE Access 2018 , 6 , 32612–32623. [ Google Scholar ] [ CrossRef ]
- Wang, T.; Hussain, A. PySNS3: A real-time communication interface and protocol for vehicular Ad-Hoc networks. In Lecture Notes of the Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering, LNICST ; Springer: Cham, Switzerland, 2018; pp. 163–171. [ Google Scholar ] [ CrossRef ]
- Xie, X.; Wang, J.; Guo, X.; Wu, X. Performance evaluation of ad-hoc routing protocols in hybrid MANET-satellite network. In Lecture Notes of the Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering, LNICST ; Springer: Cham, Switzerland, 2018; Volume 251, pp. 500–509. [ Google Scholar ] [ CrossRef ]
- Tada, N.; Patalia, T.; Rupani, P. A new approach to mitigate jamming attack in wireless adhoc network using ARC technique. In Lecture Notes of the Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering, LNICST ; Springer: Cham, Switzerland, 2018; pp. 192–204. [ Google Scholar ] [ CrossRef ]
- Liu, D.; Ni, J.; Li, H.; Shen, X. Achieving Adaptive Linkability for Cellular V2X Group Communications in 5G. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, UAE, 9–13 December 2018; pp. 1–7. [ Google Scholar ] [ CrossRef ]
- Pospelova, I.; Chebotayev, P.; Klimenko, A.; Myakochin, Y.; Polyakov, I.; Shelupanov, A.; Zykov, D. Research of G3-PLC net self-organization processes in the NS-3 modeling framework. AIP Conf. Proc. 2017 , 1899 , 060017. [ Google Scholar ] [ CrossRef ]
- Drissi, M.; Oumsis, M.; Aboutajdine, D. A Multi-Criteria Decision Framework for network selection over LTE and WLAN. Eng. Appl. Artif. Intell. 2017 , 66 , 113–127. [ Google Scholar ] [ CrossRef ]
- Abdelsalam, A.; Luglio, M.; Roseti, C.; Zampognaro, F. TCP Connection management through combined use of terrestrial and satellite IP-based links. In Proceedings of the 2017 40th International Conference on Telecommunications and Signal Processing (TSP), Barcelona, Spain, 5–7 July 2017; pp. 37–42. [ Google Scholar ] [ CrossRef ]
- Mao, Q.; Yue, P.; Xu, M.; Ji, Y.; Cui, Z. OCTMAC: A VLC based MAC protocol combining optical CDMA with TDMA for VANETs. In Proceedings of the International Conference on Computer, Information and Telecommunication Systems (CITS), Dalian, China, 21–23 July 2017; pp. 234–238. [ Google Scholar ] [ CrossRef ]
- Karimzadeh, M.; Valtulina, L.; Van Den Berg, H.; Pras, A.; Ortiz, P.; Sadre, R. MultiPath TCP to support user’s mobility in future LTE network. In Proceedings of the 2017 10th IFIP Wireless and Mobile Networking Conference (WMNC), Valencia, Spain, 25–27 September 2017; pp. 1–8. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Agarwal, R.; Shukla, P.; Goyal, S. A Practical Approach of Network Simulation. In Detecting and Mitigating Robotic Cyber Security Risks ; Kumar, R., Pattnaik, P., Pandey, P., Eds.; IGI Global: Hershey, Pennsylvania, 2017; pp. 12–27. [ Google Scholar ] [ CrossRef ]
- Liu, Y.; Piao, X.; Hou, C.; Lei, K. A CUBIC-Based explicit congestion control mechanism in named data networking. In Proceedings of the 2016 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Chengdu, China, 13–15 October 2016; pp. 360–363. [ Google Scholar ] [ CrossRef ]
- Chiu, J.C.; Liu, A.T.; Liao, C.C. Design the DNS-Like Smart Switch for Heterogeneous Network Base on SDN Architecture. In Proceedings of the 2016 International Computer Symposium (ICS), Chiayi, Taiwan, 15–17 December 2016; pp. 187–191. [ Google Scholar ] [ CrossRef ]
- Wu, W.; Li, Z.; Zhang, Y.; Guo, J.; Zhao, J. Design and implementation of distributed broadcast algorithm based on vehicle density for vanet safety-related messages. Commun. Comput. Inf. Sci. 2017 , 728 , 271–285. [ Google Scholar ] [ CrossRef ]
- Sahu, A.; Goulart, A.; Butler-Purry, K. Modeling AMI network for real-time simulation in NS-3. In Proceedings of the 2016 Principles, Systems and Applications of IP Telecommunications (IPTComm), Chicago, IL, USA, 17–20 October 2016; pp. 1–8. [ Google Scholar ]
- Yang, H.; Li, Z. A genetic-algorithm-based clustering protocol in MANET. In Proceedings of the 7th International Conference on Computing Communication and Networking Technologies, Dallas, TX, USA, 6–8 July 2016; pp. 1–5. [ Google Scholar ] [ CrossRef ]
- Deng, X.; He, L.; Li, X.; Liu, Q.; Cai, L.; Chen, Z. A reliable QoS-aware routing scheme for neighbor area network in smart grid. Peer-to-Peer Netw. Appl. 2016 , 9 , 616–627. [ Google Scholar ] [ CrossRef ]
- Wang, Z.; Guo, H.; Jiang, L.; Feng, X. AUV-aided communication method for underwater mobile sensor network. In Proceedings of the OCEANS 2016-Shanghai, Shanghai, China, 10–13 April 2016; pp. 1–7. [ Google Scholar ] [ CrossRef ]
- Wang, S.; Sun, D.; Zhang, Y. Performance analysis for ALOHA protocol of underwater acoustic networks with a serial route. Harbin Gongcheng Daxue Xuebao/J. Harbin Eng. Univ. 2016 , 37 , 360–367. [ Google Scholar ] [ CrossRef ]
- Choudhury, A.; Maszczyk, T.; Math, C.; Li, H.; Dauwels, J. An integrated simulation environment for testing V2X protocols and applications. Procedia Comput. Sci. 2016 , 80 , 2042–2052. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Kang, H.; Jiang, X.; Xiong, W. Research on wireless networking mode for the distributed satellite communication system. J. Comput. Inf. Syst. 2015 , 11 , 4211–4220. [ Google Scholar ] [ CrossRef ]
- Aburumman, A.; Seo, W.; Islam, R.; Khan, M.; Choo, K.K. A secure cross-domain SIP solution for mobile ad hoc network using dynamic clustering. In Lecture Notes of the Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering, LNICST ; Springer: Cham, Switzerland, 2015; Volume 164, pp. 649–664. [ Google Scholar ] [ CrossRef ]
- Guo, Y.; Ten, C.W.; Hu, S.; Weaver, W. Modeling distributed denial of service attack in advanced metering infrastructure. In Proceedings of the 2015 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 17–20 February 2015; pp. 1–5. [ Google Scholar ] [ CrossRef ]
- Mallissery, S.; Manohara Pai, M.; Ajam, N.; Pai, R.; Mouzna, J. Transport and traffic rule violation monitoring service in ITS: A secured VANET cloud application. In Proceedings of the 2015 12th Annual IEEE Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2015; pp. 213–218. [ Google Scholar ] [ CrossRef ]
- Tang, C.; Song, L.; Balasubramani, J.; Wu, S.; Biaz, S.; Yang, Q.; Wang, H. Comparative investigation on CSMA/CA-based opportunistic random access for internet of things. IEEE Internet Things J. 2014 , 1 , 171–179. [ Google Scholar ] [ CrossRef ]
- Molloy, T.; Yuan, Z.; Muntean, G.M. Real time emulation of an LTE network using NS-3. In Proceedings of the 25th IET Irish Signals & Systems Conference 2014 and 2014 China-Ireland International Conference on Information and Communications Technologies (ISSC 2014/CIICT 2014), Limerick, Ireland, 26–27 June 2014; Volume 2014, pp. 251–257. [ Google Scholar ] [ CrossRef ]
- Satria, T.; Karimzadeh, M.; Karagiannis, G. Performance evaluation of ICN/CCN based service migration approach in virtualized LTE systems. In Proceedings of the 2014 IEEE 3rd International Conference on Cloud Networking (CloudNet), Luxembourg, 8–10 October 2014; pp. 461–467. [ Google Scholar ] [ CrossRef ]
- Shukla, S.; Chan, S.; Tam, A.W.; Gupta, A.; Xu, Y.; Chao, H. TCP PLATO: Packet labelling to alleviate time-out. IEEE J. Sel. Areas Commun. 2014 , 32 , 65–76. [ Google Scholar ] [ CrossRef ]
- Marques, H.; Leguay, J.; Khalifé, H.; Conan, V.; Lavaux, D. Transparent IP proxy for tactical ad hoc networks. In Proceedings of the MILCOM 2013-2013 IEEE Military Communications Conference, San Diego, CA, USA, 17–20 November 2013; pp. 842–847. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Wang, Y.; Rozhnova, N.; Narayanan, A.; Oran, D.; Rhee, I. An improved hop-by-hop interest shaper for congestion control in named data networking. ACM SIGCOMM Comput. Commun. Rev. 2013 , 43 , 567–572. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Tsokalo, I.; Mudriievskyi, S.; Lehnert, R. Development and calibration of a PLC simulation model for UPA-compliant networks. In Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics) ; Springer: Berlin/Heidelberg, Germany, 2013; Volume 8115 LNCS, pp. 197–208. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Meneguette, R.; Bittencourt, L.; Madeira, E. User-centric mobility management architecture for vehicular networks. In Lecture Notes of the Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering, LNICST ; Springer: Berlin/Heidelberg, Germany, 2013; Volume 58, pp. 42–56. [ Google Scholar ] [ CrossRef ]
- Carvin, D.; Kremer, G.; Owezarski, P.; Berthou, P. Assessment and event based analysis of dynamic wireless networks. In Proceedings of the 9th International Conference on Network and Service Management (CNSM 2013), Zürich, Switzerland, 14–18 October 2013; pp. 175–179. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Biddlestone, S.; Redmill, K.; Miucic, R.; Ozguner, U. An integrated 802.11p WAVE DSRC and vehicle traffic simulator with experimentally validated urban (LOS and NLOS) propagation models. IEEE Trans. Intell. Transp. Syst. 2012 , 13 , 1792–1802. [ Google Scholar ] [ CrossRef ]
- Vetrivelan, P.; Narayanasamy, P.; John Charlas, J. A multi-constraint real-time vehicular (MCRV) mobility framework for 4G heterogeneous Vehicular Ad-Hoc Networks. In Proceedings of the International MultiConference of Engineers and Computer Scientists, Hong Kong, China, 14–16 March 2012; Volume 2195, pp. 423–428. [ Google Scholar ]
- Vetrivelan, P.; Narayanasamy, P. SMIRT with call admission control (CAC) based vertical handover decision for seamless mobility in multi-access 4G heterogeneous wireless overlav networks. In Proceedings of the International Multiconference of Engineers & Computer Scientists, Hong Kong, China, 14–16 March 2012; Volume 2195, pp. 408–413. [ Google Scholar ]
- Qwasmi, N.; Ahmed, F.; Liscano, R. Simulation of DDOS attacks on P2P metworks. In Proceedings of the 2011 IEEE International Conference on High Performance Computing and Communications, Banff, AB, Canada, 2–4 September 2011; pp. 610–614. [ Google Scholar ] [ CrossRef ]
- Katkar, P.S.; Ghorpade, D.V.R. Comparative study of network simulator: NS2 and NS3. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2016 , 6 , 608–612. [ Google Scholar ]
- Siraj, S.; Gupta, A.; Badgujar, R. Network simulation tools survey. Int. J. Adv. Res. Comput. Commun. Eng. 2012 , 1 , 199–206. [ Google Scholar ]
- Pan, J.; Jain, R. A Survey of Network Simulation Tools: Current Status and Future Developments. 2008, Volume 2, p. 45. Available online: https://www.cse.wustl.edu/~jain/cse567-08/ftp/simtools/index.html (accessed on 3 September 2019).
- Korkalainen, M.; Sallinen, M.; Kärkkäinen, N.; Tukeva, P. Survey of wireless sensor networks simulation tools for demanding applications. In Proceedings of the 2009 Fifth International Conference on Networking and Services, Valencia, Spain, 20–25 April 2009; pp. 102–106. [ Google Scholar ]
- Venkataramanan, V.; Lakshmi, S. A Case Study of Various Wireless Network Simulation Tools. Int. J. Commun. Netw. Inf. Secur. 2018 , 10 , 389–396. [ Google Scholar ]
- Mehta, S.; Ullah, N.; Kabir, M.H.; Sultana, M.N.; Kwak, K.S. A Case Study of Networks Simulation Tools for Wireless Networks. In Proceedings of the 2009 Third Asia International Conference on Modelling Simulation, Bali, Indonesia, 25–29 May 2009; pp. 661–666. [ Google Scholar ] [ CrossRef ]
- Dorathy, I.; Chandrasekaran, M. Simulation tools for mobile ad hoc networks: A survey. J. Appl. Res. Technol. 2018 , 16 , 437–445. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Mallapur, S.V.; Patil, S.R. Survey on simulation tools for mobile ad-hoc networks. In. J. Comput. Netw. Wirel. Commun. 2012 , 2 , 241–248. [ Google Scholar ]
- Toor, A.S.; Jain, A. A survey on wireless network simulators. Bull. Electrical Eng. Inform. 2017 , 6 , 62–69. [ Google Scholar ]
- Miozzo, M.; Bartzoudis, N.; Requena, M.; Font-Bach, O.; Harbanau, P.; López-Bueno, D.; Payaró, M.; Mangues, J. SDR and NFV extensions in the ns-3 LTE module for 5G rapid prototyping. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [ Google Scholar ]
- Giupponi, L.; Henderson, T.; Bojovic, B.; Miozzo, M. Simulating LTE and Wi-Fi coexistence in unlicensed spectrum with NS-3. arXiv 2016 , arXiv:1604.06826. [ Google Scholar ]
- Zhong, P.; Li, Y.; Huang, W.; Kui, X.; Zhang, Y.; Chen, Y. An Extension to ns-3 for Simulating Mobile Charging with Wireless Energy Transfer. In Communications in Computer and Information Science ; Zou, B., Han, Q., Sun, G., Jing, W., Peng, X., Lu, Z., Eds.; Data Science. ICPCSEE 2017; Springer: Singapore, 2017; Volume 728, pp. 256–270. [ Google Scholar ]
- Alwahab, D.A.; Laki, S. A simulation-based survey of active queue management algorithms. In Proceedings of the 6th International Conference on Communications and Broadband Networking, Singapore, 24–26 February 2018; pp. 71–77. [ Google Scholar ]
- Jian, Y.; Krishnaswamy, B.; Austin, C.M.; Bicen, A.O.; Einolghozati, A.; Perdomo, J.E.; Patel, S.C.; Fekri, F.; Akyildiz, I.F.; Forest, C.R.; et al. nanoNS3: A network simulator for bacterial nanonetworks based on molecular communication. Nano Commun. Netw. 2017 , 12 , 1–11. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Bisio, I.; Delucchi, S.; Lavagetto, F.; Marchese, M.; Portomauro, G.; Zappatore, S. An Ns-3 based simulative and emulative platform. In Modeling and Simulation of Computer Networks and Systems ; Elsevier: Amsterdam, The Netherlands, 2015; pp. 555–575. [ Google Scholar ]
- Kim, E.; Riley, G.F. Automatic State Saving and Rollback in ns-3. In Proceedings of the 2017 ACM SIGSIM Conference on Principles of Advanced Discrete Simulation, Singapore, 24–26 May 2017; pp. 263–266. [ Google Scholar ]
- Maskooki, A.; Sabatino, G.; Mitton, N. Chapter 21—Analysis and performance evaluation of the next generation wireless networks. In Modeling and Simulation of Computer Networks and Systems ; Obaidat, M.S., Nicopolitidis, P., Zarai, F., Eds.; Morgan Kaufmann: Boston, MA, USA, 2015; pp. 601–627. [ Google Scholar ] [ CrossRef ]
- Fernandes, D.A.; Neto, M.; Soares, L.F.; Freire, M.M.; Inácio, P.R. Chapter 10—On the self-similarity of traffic generated by network traffic simulators. In Modeling and Simulation of Computer Networks and Systems ; Obaidat, M.S., Nicopolitidis, P., Zarai, F., Eds.; Morgan Kaufmann: Boston, MA, USA, 2015; pp. 285–311. [ Google Scholar ] [ CrossRef ]
- Amoretti, M.; Picone, M.; Zanichelli, F.; Ferrari, G. Chapter 16—Simulating wireless and mobile systems: The Integration of DEUS and Ns-3. In Modeling and Simulation of Computer Networks and Systems ; Obaidat, M.S., Nicopolitidis, P., Zarai, F., Eds.; Morgan Kaufmann: Boston, MA, USA, 2015; pp. 465–484. [ Google Scholar ] [ CrossRef ]
- Tsioliaridou, A.; Liaskos, C.; Dedu, E.; Ioannidis, S. Packet routing in 3D nanonetworks: A lightweight, linear-path scheme. Nano Commun. Netw. 2017 , 12 , 63–71. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Hossain, Z.; Xia, Q.; Jornet, J.M. TeraSim: An ns-3 extension to simulate Terahertz-band communication networks. Nano Commun. Netw. 2018 , 17 , 36–44. [ Google Scholar ] [ CrossRef ]
- Barolli, A.; Oda, T.; Ikeda, M.; Barolli, L.; Xhafa, F.; Loia, V. Node placement for wireless mesh networks: Analysis of WMN-GA system simulation results for different parameters and distributions. J. Comput. Syst. Sci. 2015 , 81 , 1496–1507. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Habbal, A.; Goudar, S.I.; Hassan, S. A Context-aware Radio Access Technology selection mechanism in 5G mobile network for smart city applications. J. Netw. Comput. Appl. 2019 , 135 , 97–107. [ Google Scholar ] [ CrossRef ]
- Aldalbahi, A.; Rahaim, M.; Khreishah, A.; Ayyash, M.; Ackerman, R.; Basuino, J.; Berreta, W.; Little, T.D. Extending ns3 to simulate visible light communication at network-level. In Proceedings of the 2016 23rd International Conference on Telecommunications (ICT), Thessaloniki, Greece, 16–18 May 2016; pp. 1–6. [ Google Scholar ]
- Rajankumar, P.; Nimisha, P.; Kamboj, P. A comparative study and simulation of AODV MANET routing protocol in NS2 & NS3. In Proceedings of the 2014 International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 5–7 March 2014; pp. 889–894. [ Google Scholar ]
- Aldalbahi, A.; Rahaim, M.; Khreishah, A.; Ayyash, M.; Little, T.D. Visible light communication module: An open source extension to the ns3 network simulator with real system validation. IEEE Access 2017 , 5 , 22144–22158. [ Google Scholar ] [ CrossRef ]
- Liu, W.; Wang, X.; Zhang, W.; Yang, L.; Peng, C. Coordinative simulation with SUMO and NS3 for vehicular ad hoc networks. In Proceedings of the 2016 22nd Asia-Pacific Conference on Communications (APCC), Yogyakarta, Indonesia, 25–27 August 2016; pp. 337–341. [ Google Scholar ]
- Jha, R.K.; Kharga, P. A comparative performance analysis of routing protocols in MANET using NS3 simulator. Int. J. Comput. Netw. Inf. Security 2015 , 7 , 62–68. [ Google Scholar ]
- Bhatia, D.; Sharma, D.P. A comparative analysis of proactive, reactive and hybrid routing protocols over open source network simulator in mobile ad hoc network. Int. J. Appl. Eng. Res. 2016 , 11 , 3885–3896. [ Google Scholar ]
- Naik, L.; Khan, R.; Mishra, R. Analysis of node velocity effects in MANET routing protocols using network simulator (NS3). Int. J. Comput. Appl. 2016 , 144 , 1–5. [ Google Scholar ] [ CrossRef ]
- Aman, A.H.M.; Hashim, A.H.A.; Ramli, H.A.M. Simulation Analysis for Multicast Context Delivery Network Mobility Management. Indones. J. Electr. Eng. Inform. (IJEEI) 2017 , 5 , 390–394. [ Google Scholar ]
- Saluja, A.; Dargad, S.; Mistry, K. A Detailed Analogy of Network Simulators—NS1, NS2, NS3 and NS4. Int. J. Future Revolut. Comput. Sci. Commun. Eng. 2017 , 3 , 291–295. [ Google Scholar ]
- Spaho, E.; Bylykbashi, K.; Barolli, L.; Takizawa, M. Routing in a DTN: Performance evaluation for random waypoint and steady state random waypoint using NS3 simulator. In Advances on P2P, Parallel, Grid, Cloud and Internet Computing, 3PGCIC 2017 ; Xhafa, F., Caballé, S., Barolli, L., Eds.; Lecture Notes on Data Engineering and Communications Technologies; Springer: Cham, Switzerland, 2017; Volume 13, pp. 133–141. [ Google Scholar ]
- Patel, R.; Patel, N.; Patel, S. An Approach to Analyze Behavior of Network Events in NS2 and NS3 Using AWK and Xgraph. In Information and Communication Technology for Competitive Strategies ; Springer: Cham, Switzerland, 2019; pp. 137–147. [ Google Scholar ]
- Amiri-Nezhad, M.; Guerrero-Zapata, M.; Bellalta, B.; Cerdà-Alabern, L. Simulation of multi-radio multi-channel 802.11-based mesh networks in ns-3. EURASIP J. Wirel. Commun. Netw. 2014 , 2014 , 118. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Nurchis, M.; Bellalta, B. Performance Evaluation of LAA-LTE and WiFi Coexistence in Unlicensed 5 GHz Band Under Asymmetric Network Deployments Using NS3. In Proceedings of the International Workshop on Multiple Access Communications, Aalborg, Denmark, 21–22 November 2016; Springer: Cham, Switzerland, 2016; pp. 86–97. [ Google Scholar ]
- Paliwal, G.; Taterh, S. Impact of Dense Network in MANET Routing Protocols AODV and DSDV Comparative Analysis Through NS3. In Soft Computing: Theories and Applications ; Springer: Cham, Switzerland, 2018; pp. 327–335. [ Google Scholar ]
- Khattak, R.; Chaltseva, A.; Riliskis, L.; Bodin, U.; Osipov, E. Comparison of wireless network simulators with multihop wireless network testbed in corridor environment. In Proceedings of the Multiple Access Communications, Lecture Notes in Computer Science, MACOM 2016, Thessaloniki, Greece, 25–27 May 2016; Madsen, T., Nielsen, J., Pratas, N., Eds.; Springer: Cham, Switzerland, 2011; Volume 10121, pp. 80–91. [ Google Scholar ]
- Nabou, A.; Laanaoui, M.D.; Ouzzif, M. The Effect of Transmit Power on MANET Routing Protocols Using AODV, DSDV, DSR and OLSR in NS3. In Advanced Intelligent Systems for Sustainable Development (AI2SD’2018), Proceedings of the Advances in Intelligent Systems and Computing AI2SD 2018, Tangier, Morocco, 12–14 July 2018 ; Ezziyyani, M., Ed.; Springer: Cham, Switzerland, 2018; Volume 915, pp. 274–286. [ Google Scholar ]
- Henderson, T.R.; Lacage, M.; Riley, G.F.; Dowell, C.; Kopena, J. Network simulations with the ns-3 simulator. SIGCOMM Demonstr. 2008 , 14 , 527. [ Google Scholar ]
- Afanasyev, A.; Moiseenko, I.; Zhang, L. ndnSIM: NDN Simulator for NS-3 ; University of California: Los Angeles, CA, USA, 2012; Volume 4. [ Google Scholar ]
- Mastorakis, S.; Afanasyev, A.; Moiseenko, I.; Zhang, L. ndnSIM 2: An Updated NDN Simulator for NS-3; NDN, Technical Report NDN-0028. 2016, pp. 1–8. Available online: http://named-data.net/publications/techreports/ndn-0028-2-ndnsim-v2/ (accessed on 3 September 2019).
- Pei, G.; Henderson, T.R. Validation of OFDM error rate model in ns-3. Boeing Res. Technol. 2010 , 1–15. Available online: https://pdfs.semanticscholar.org/3f0a/b039b235bd0fa1e833876ba78e7ea99d9a04.pdf (accessed on 3 September 2019).
- Carneiro, G.; Fortuna, P.; Ricardo, M. FlowMonitor: A network monitoring framework for the network simulator 3 (NS-3). In Proceedings of the Fourth International ICST Conference on Performance Evaluation Methodologies and Tools, Pisa, Italy, 20–22 October 2009; ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering): Brussels, Belgium, 2009; pp. 1–10. [ Google Scholar ]
- Arbabi, H.; Weigle, M.C. Highway mobility and vehicular ad-hoc networks in ns-3. In Proceedings of the Winter Simulation Conference, Baltimore, MA, USA, 5–8 December 2010; pp. 2991–3003. [ Google Scholar ]
- Stoffers, M.; Riley, G. Comparing the ns-3 propagation models. In Proceedings of the 2012 IEEE 20th International Symposium on Modeling, Analysis and Simulation of Computer and Telecommunication Systems, San Francisco, CA, USA, 7–9 August 2012; pp. 61–67. [ Google Scholar ]
- Narra, H.; Cheng, Y.; Cetinkaya, E.K.; Rohrer, J.P.; Sterbenz, J.P. Destination-sequenced distance vector (DSDV) routing protocol implementation in ns-3. In Proceedings of the 4th International ICST Conference on Simulation Tools and Techniques, Barcelona, Spain, 21–25 March 2011; ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering): Brussels, Belgium, 2011; pp. 439–446. [ Google Scholar ]
- Van den Abeele, F.; Haxhibeqiri, J.; Moerman, I.; Hoebeke, J. Scalability analysis of large-scale LoRaWAN networks in ns-3. IEEE Internet Things J. 2017 , 4 , 2186–2198. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Wu, X.; Brown, K.N.; Sreenan, C.J.; Alvarez, P.; Ruffini, M.; Marchetti, N.; Payne, D.; Doyle, L. An XG-PON module for the NS-3 network simulator. In Proceedings of the 6th International ICST Conference on Simulation Tools and Techniques, Cannes, France, 5–7 March 2013; ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering): Brussels, Belgium, 2013; pp. 195–202. [ Google Scholar ]
- Lu, Z.; Qu, G.; Liu, Z. A Survey on Recent Advances in Vehicular Network Security, Trust, and Privacy. IEEE Trans. Intell. Transp. Syst. 2019 , 20 , 760–776. [ Google Scholar ] [ CrossRef ]
- Dong, Q.; Chen, Y.; Li, X.; Zeng, K. A Survey on Simulation Tools and Testbeds for Cognitive Radio Networks Study. arXiv 2018 , arXiv:1808.09858. [ Google Scholar ]
- Alenazi, M.J.F.; Cheng, Y.; Zhang, D.; Sterbenz, J.P.G. Epidemic routing protocol implementation in ns-3. In Proceedings of the 2015 Workshop on ns-3, Castelldefels, Spain, 13–14 May 2015; ACM: New York, NY, USA, 2015; pp. 54–59. [ Google Scholar ]
Click here to enlarge figure
| Tool | ns-3 | ns-3 | OMNET++ | SWANS | NetSim | QualNet |
|---|---|---|---|---|---|---|
| Interface | C++/Python | C++/OTcl | C++/NED | Java | C/Java/.NET | Parsec (C Based) |
| License | Free | Free | Free for academic | Free | Commercial | Commercial |
| Parallelism | No | No | MPI/PVM | No | - | SMP/Beowulf |
| O.S. | Linux, FreeBSD, Mac OS X, Windows | Linux, FreeBSD, Mac OS X, Windows | Linux, Mac OS X, Windows | Linux, Mac OS X, Windows | Windows | Linux, Mac OS X, Windows, Unix |
| Mobility Support | Yes | Yes | No | Yes | Yes | Yes |
| GUI Support | Limited | Yes | Yes | Yes | Yes | Yes |
| Data Source | Web Site |
|---|---|
| Scopus | |
| The ACM Digital Library | |
| IEEE Xplore | |
| Springer | |
| Elsevier Science Direct |
| Source | Number of Docs for ns3 | Number of Docs for ns-3 | |
|---|---|---|---|
| 1 | Google Scholar | 28,700 | 32,500 |
| 2 | Elsevier | 7 | 27,109 |
| 3 | Springer | 21 | 73,518 |
| 4 | IEEE Explore D.L. | 457 | 1816 |
| 5 | The ACM Digital Library | 394 | 290,550 |
| C.2.0 | General |
|---|---|
| C.2.1 | Network Architecture and Design |
| C.2.2 | Network Protocols |
| C.2.3 | Network Operations |
| C.2.4 | Distributed Systems |
| C.2.5 | Local and Wide-Area Networks |
| C.2.6 | Internetworking |
| C.2.m | Miscellaneous |
| implementation | 31 |
| implementing | 2 |
| improved | 2 |
| improvement | 1 |
| improving | 2 |
| enhancing | 1 |
| extending | 2 |
| extension | 3 |
| integration | 1 |
| integrating | 1 |
| Type | Criteria | |
|---|---|---|
| 1 | Exclusion | Informal literature |
| 2 | Exclusion | Duplicated papers |
| 3 | Exclusion | Papers that did not comply research questions |
| 4 | Exclusion | Papers not written in English language |
| 5 | Inclusion | Papers that report any kind of use of ns-3 |
| Id | ... |
|---|---|
| Author | ... |
| Title | ... |
| Year | ... |
| Venue | ... |
| Citations | ... |
| RQ1 | Which are the impacted Application Domains? |
| Q1.1 | What kind of the network technologies are simulated? (e.g., WSN, wireless networks, |
| mobile networks, internetworking...) | |
| Q1.2 | Which are the related application field? (e.g., medicine, astrology, ...) |
| Q1.3 | What kind of problem is addressed? (e.g., security, assessment, experimental methodology...) |
| RQ2 | How much is this approach extensible? |
| Q2.1 | Is it a new extension or module? yes/no |
| Q2.2 | Does it use an external module or extension? yes/no |
| 2009 | 2010 | 2011 | 2012 | 2013 | 2014 | |
|---|---|---|---|---|---|---|
| Query | 2% | 0% | 2% | 6% | 5% | 5% |
| search | (3) | (0) | (3) | (8) | (7) | (7) |
| Selected | 2% | 0% | 2% | 7% | 6% | 6% |
| papers | (2) | (0) | (2) | (8) | (7) | (7) |
| 2015 | 2016 | 2017 | 2018 | 2019 | TOTAL | |
|---|---|---|---|---|---|---|
| Query | 16% | 19% | 23% | 13% | 9% | 100% |
| search | (21) | (23) | (28) | (17) | (11) | 128 |
| Selected | 16% | 19% | 22% | 12% | 8% | 100% |
| papers | (19) | (23) | (27) | (15) | (10) | 120 |
| Application study | 68 |
| Module extension | 5 |
| Conceptual study | 36 |
| Survey | 11 |
| Id | Quality Assessment Criteria | Score |
|---|---|---|
| A1 | What is the relevance of the paper according to the | |
| conference/journal where it was published? | ||
| A2 | What is the relevance of the citation according to its | |
| related citations? | ||
| A3 | How clearly is the problem of the study described? | |
| A4 | How clearly is the research context stated? | |
| A5 | How explicitly are the contributions presented? | |
| A6 | How explicitly are the insights and issues for future | |
| work stated? | ||
| RQ1 | Which are the Impacted Application Domains? | ||
|---|---|---|---|
| Q1.1 | What kind of network technologies are simulated? | % | n |
| MANET | 14% | 16 | |
| WSN | 8% | 10 | |
| Wireless Networks | 12% | 14 | |
| Mobile Networks | 15% | 18 | |
| Networking | 27% | 32 | |
| VANET | 17% | 18 | |
| Other | 7% | 9 | |
| Q1.2 | Which are the related application fields? | ||
| Medicine | |||
| Physics | |||
| Astronomy | |||
| Other | |||
| Q1.3 | What kind of problem is addressed? | ||
| Security | 11% | 11 | |
| Assessment | 33% | 34 | |
| Network Protocol | 26% | 27 | |
| Physical Layer | 6% | 6 | |
| Performance | 24% | 24 |
| RQ2 | How Much Is This Approach Extensible? | ||
|---|---|---|---|
| Q2.1 | Is it a new extension or module? | % | n |
| Yes | 17% | 20 | |
| No | 83% | 100 | |
| Q2.2 | Does it use an external module or extension? | ||
| Yes | 31% | 37 | |
| No | 89% | 83 |
| 2009 | 2010 | 2011 | 2012 | 2013 | 2014 | 2015 | 2016 | 2017 | 2018 | 2019 |
|---|---|---|---|---|---|---|---|---|---|---|
| 2 | 0 | 2 | 8 | 7 | 7 | 19 | 23 | 27 | 15 | 10 |
Share and Cite
Campanile, L.; Gribaudo, M.; Iacono, M.; Marulli, F.; Mastroianni, M. Computer Network Simulation with ns-3: A Systematic Literature Review. Electronics 2020 , 9 , 272. https://doi.org/10.3390/electronics9020272
Campanile L, Gribaudo M, Iacono M, Marulli F, Mastroianni M. Computer Network Simulation with ns-3: A Systematic Literature Review. Electronics . 2020; 9(2):272. https://doi.org/10.3390/electronics9020272
Campanile, Lelio, Marco Gribaudo, Mauro Iacono, Fiammetta Marulli, and Michele Mastroianni. 2020. "Computer Network Simulation with ns-3: A Systematic Literature Review" Electronics 9, no. 2: 272. https://doi.org/10.3390/electronics9020272
Article Metrics
Article access statistics, further information, mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals
- DOI: 10.4236/IIM.2014.63012
- Corpus ID: 5965458
Literature Review on Network Design Problems in Closed Loop and Reverse Supply Chains
- Muthusamy Aravendan , R. Panneerselvam
- Published 24 April 2014
- Business, Engineering, Environmental Science
- Intelligent Information Management
23 Citations
Dual and multi-channel closed-loop supply chains: a state of the art review, optimal design of closed-loop supply chain networks with multifunctional nodes, literature review: strategic network optimization models in waste reverse supply chains, dual channel closed loop supply chains: a state of the art review, proposed design of white sugar industrial supply chain system based on blockchain technology, a closed-loop packaging network design model to foster infinitely reusable and recyclable containers in food industry, simultaneous optimization of closed- and open-loop supply chain networks with common components, a comprehensive review of closed loop supply chain, a bi-objective two-stage stochastic optimization model for sustainable reverse supply chain network design under carbon tax policy and government subsidy considering product quality, 70 references, development of rfid-based reverse logistics system, reverse logistics network design: a framework for decision making, integrating reverse logistics into the strategic planning of a supply chain, production , manufacturing and logistics reverse logistics network design for the collection of end-of-life vehicles in mexico, strategic network design for reverse logistics and remanufacturing using new and old product modules, designing a reverse logistics network for optimal collection, recovery and quality-based product-mix planning, a dynamic pricing approach for returned products in integrated forward/reverse logistics network design, the dynamic design of a reverse logistics network from the perspective of third-party logistics service providers, an integrated forward/reverse logistics network optimization model for multi-stage capacitated supply chain, modeling reverse logistics process in the agro-industrial sector: the case of the palm oil supply chain, related papers.
Showing 1 through 3 of 0 Related Papers

IMAGES
VIDEO
COMMENTS
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on NETWORK DESIGN. Find methods information, sources, references or conduct a literature review on...
The purpose of this paper is threefold. First, it classifies research on distribution network design (DND) according to the methodologies adopted and themes tackled. Second, it discusses the main implications for practitioners. Finally, it proposes a few promising directions for future research.
This paper gives a comprehensive review of literature of the design of networks for the reverse logistics as well as for the reverse logistics coupled with forward logistics.
After summarizing the major developments in telecommunications network design technologies/services, we describe some promising future research directions to address an environment where technology is ever-changing and traffic forecasting is difficult.
In this paper, we review more than 100 papers on recent literature regarding intermodal network design from a hub location perspective. We discuss recent trends and provide more than 20 future research directions focused on the modeling of realistic intermodal transportation systems.
This chapter aims at analysing the main trends and characteristics of the literature regarding networks and organizations in the last 20 years (2002–2021). Following Massaro, Dumay, and Guthrie (2016) we developed a structured literature review, starting with setting boundaries to our research.
A network is a complex mix of applications, communications protocols and link technologies, traffic flows and routing algorithms. Teaching the networking concept, the network design process is a challenging task, requiring designers to balance user performance expectations with costs and capacities.
In this systematic literature review we aim to analyze, basing our investigation on available literature, the adoption of a popular network simulator, namely ns-3, and its use in the scientific community.
This paper gives a comprehensive review of literature of the design of networks for the reverse logistics as well as for the reverse logistics coupled with forward logistics. The contri-butions of the researchers are classified into nine categories based on the methods used to design the logistics network. Keywords.
Originality/value – This review offers valuable insights for practitioners: a clear understanding of the main decisions related to DND; a comprehensive analysis of the main factors that affect...