
- October 2, 2018 | IEEE Cybersecurity Award Winners
- October 1, 2018 | Save the Date for SecDev 2019
- January 31, 2018 | IEEE SecDev 2018 Call for Papers
- December 13, 2017 | Robert Cunningham on Advancing the Art and Science of Cybersecurity
- December 6, 2017 | IEEE TryCybSI Partners on Why Active Learning is Key for Mastering Cybersecurity

IEEE Security & Privacy
IEEE Security & Privacy magazine provides articles with both a practical and research bent by the top thinkers in the field along with case studies, tutorials, columns, and in-depth interviews and podcasts for the information security industry.
IEEE Transactions on Dependable and Secure Computing
IEEE Transactions on Dependable and Secure Computing (TDSC) publishes archival research results focusing on foundations, methodologies, and mechanisms that support the achievement—through design, modeling, and evaluation—of systems and networks that are dependable and secure to the desired degree without compromising performance. Read the full scope here .
- IEEE Xplore Digital Library
- IEEE Standards
- IEEE Spectrum
- Subscribe to Newsletter
- Resource Center
- Create Account
What is Signal Processing?
- Board of Governors
- Executive Committee
- Awards Board
- Conferences Board
- Membership Board
- Publications Board
- Technical Directions Board
- Standing Committees
- Liaisons & Representatives
- Education Board
- Our Members
- Society History
- State of the Society
- SPS Branding Materials
- Publications & Resources
- IEEE Signal Processing Magazine
- IEEE Journal of Selected Topics in Signal Processing
- IEEE Signal Processing Letters
- IEEE/ACM Transactions on Audio Speech and Language Processing
- IEEE Transactions on Computational Imaging
- IEEE Transactions on Image Processing
IEEE Transactions on Information Forensics and Security
- IEEE Transactions on Multimedia
- IEEE Transactions on Signal and Information Processing over Networks
- IEEE Transactions on Signal Processing
- Data & Challenges
- Submit Manuscript
- Information for Authors
- Special Issue Deadlines
- Overview Articles
- Top Accessed Articles
- SPS Newsletter
- SPS Resource Center
- Publications Feedback
- Publications FAQ
- Dataset Papers
- Conferences & Events
- Conferences
- Attend an Event
- Conference Call for Papers
- Calls for Proposals
- Conference Sponsorship Info
- Conference Resources
- SPS Travel Grants
- Conferences FAQ
- Getting Involved
- Young Professionals
- Our Technical Committees
- Contact Technical Committee
- Technical Committees FAQ
- Data Science Initiative
- Join Technical Committee
- Young Professionals Resources
- Member-driven Initiatives
- Chapter Locator
- Award Recipients
- IEEE Fellows Program
- Call for Nominations
- Professional Development
- Distinguished Lecturers
- Past Lecturers
- Nominations
- DIS Nominations
- Seasonal Schools
- Industry Resources
- Job Submission Form
- IEEE Training Materials
- For Volunteers
- Board Agenda/Minutes
- Chapter Resources
- Governance Documents
- Membership Development Reports
- TC Best Practices
- SPS Directory
- Society FAQ
- Information for Authors-OJSP
dataport_5.jpg

Discover More About Your Free Subscription to IEEE DataPort(™)
Webinar_asi.jpg.

SPS Webinar: PhishSim: Aiding Phishing Website Detection With a Feature-Free Tool
Nominate_3.jpg.

Deadline Extended - Call for Nominations: Awards Board Chair
- Celebrating 75 Years of IEEE SPS
- Diversity, Equity, and Inclusion
- General SP Multimedia Content

- Submit a Manuscript
- Editorial Board Nominations
- Challenges & Data Collections
- Publication Guidelines
- Unified EDICS
- Signal Processing Magazine The premier publication of the society.
- SPS Newsletter Monthly updates in Signal Processing
- SPS Resource Center Online library of tutorials, lectures, and presentations.
- SigPort Online repository for reports, papers, and more.
- SPS Feed The latest news, events, and more from the world of Signal Processing.
- IEEE SP Magazine
- IEEE SPS Content Gazette
- IEEE SP Letters
- IEEE/ACM TASLP
- All SPS Publications
- SPS Entrepreneurship Forum
- Call for Papers
- Call for Proposals
- Request Sponsorship
- Conference Organizer Resources
- Past Conferences & Events
- Event Calendar
- Conferences Meet colleagues and advance your career.
- Webinars Register for upcoming webinars.
- Distinguished Lectures Learn from experts in signal processing.
- Seasonal Schools For graduate students and early stage researchers.
- All Events Browse all upcoming events.
- Join SPS The IEEE Signal Processing Magazine, Conference, Discounts, Awards, Collaborations, and more!
- Chapter Locator Find your local chapter and connect with fellow industry professionals, academics and students
- Women in Signal Processing Networking and engagement opportunities for women across signal processing disciplines
- Students Scholarships, conference discounts, travel grants, SP Cup, VIP Cup, 5-MICC
- Young Professionals Career development opportunities, networking
- Chapters & Communities
- Member Advocate
- Awards & Submit an Award Nomination
- Volunteer Opportunities
- Organize Local Initiatives
- Autonomous Systems Initiative
- Applied Signal Processing Systems
- Audio and Acoustic Signal Processing
- Bio Imaging and Signal Processing
- Computational Imaging
- Image Video and Multidimensional Signal Processing
- Information Forensics and Security
- Machine Learning for Signal Processing
- Multimedia Signal Processing
- Sensor Array and Multichannel
- Signal Processing for Communication and Networking
- Signal Processing Theory and Methods
- Speech and Language Processing
- Synthetic Aperture Technical Working Group
- Industry Technical Working Group
- Integrated Sensing and Communication Technical Working Group
- TC Affiliate Membership
- Co-Sponsorship of Non-Conference TC Events
- Mentoring Experiences for Underrepresented Young Researchers (ME-UYR)
- Micro Mentoring Experience Program (MiME)
- Distinguished Lecturer Program
- Distinguished Lecturer Nominations
- Distinguished Industry Speaker Program
- Distinguished Industry Speakers
- Distinguished Industry Speaker Nominations
- Jobs in Signal Processing: IEEE Job Site
- SPS Education Program Educational content in signal processing and related fields.
- Distinguished Lecturer Program Chapters have access to educators and authors in the fields of Signal Processing
- PROGRESS Initiative Promoting diversity in the field of signal processing.
- Job Opportunities Signal Processing and Technical Committee specific job opportunities
- Job Submission Form Employers may submit opportunities in the area of Signal Processing.
- Technical Committee Best Practices
- Conflict of Interest
- Policy and Procedures Manual
- Constitution
- Board Agenda/Minutes* Agendas, minutes and supporting documentation for Board and Committee Members
- SPS Directory* Directory of volunteers, society and division directory for Board and Committee Members.
- Membership Development Reports* Insight into the Society’s month-over-month and year-over-year growths and declines for Board and Committee Members
Popular Pages
- Information for Authors OJSP
- Awards & Submit Award Nomination
- (ISBI 2025) 2025 IEEE International Symposium on Biomedical Imaging
- IEEE TMM Special Issue on Large Multi-modal Models for Dynamic Visual Scene Understanding
- Information for Authors-SPL
- Signal Processing 101
Last viewed:
- Call for Proposals - ASRU 2023
- Deep Learning for Audio Signal Processing
- 3 year Postdoc Position (E14) "Machine Learning for Speech and Audio Processing" at Universität Hamburg, Germany
- Assistant Professor or untenured Associate Professor, Stanford Data Science and The School of Engineering
- IEEE JSTSP Special Issue on Seeking Low-dimensionality in Deep Neural Networks (SLowDNN)
- IEEE JSTSP Special Issue on Low-Bit-Resolution Signal Processing: Algorithms, Implementations, and Applications
- IEEE JSTSP Special Issue on Modelling and processing language and speech in neurodegenerative disorders
- IEEE SPM Special Issue on the Mathematics of Deep Learning
- Publications
- Guidelines for Associate Editors
Search form
You are here.
- Editorial Board
- Early Access
- Challenges & Data Collections Members
- Data Challenges
- Dataset Resources
- Challenge Papers
For Authors
- IEEE Author Center
- IEEE Copyright Form
Submit a Manuscript
Editorial Board Nominations

election_vote.jpg

Top Reasons to Join SPS Today!
1. IEEE Signal Processing Magazine 2. Signal Processing Digital Library* 3. Inside Signal Processing Newsletter 4. SPS Resource Center 5. Career advancement & recognition 6. Discounts on conferences and publications 7. Professional networking 8. Communities for students, young professionals, and women 9. Volunteer opportunities 10. Coming soon! PDH/CEU credits Click here to learn more .

Technical Co-Sponsors:
- IEEE Communications Society
- IEEE Computational Intelligence Society
- IEEE Computer Society
- IEEE Engineering in Medicine and Biology Society
- IEEE Information Theory Society
The IEEE Transactions on Information Forensics and Security covers the sciences, technologies, and applications relating to information forensics, information security, biometrics, surveillance and systems applications that incorporate these features.
For new submissions, go to Scholar One .
Reproducible research
The Transactions encourages authors to make their publications reproducible by making all information needed to reproduce the presented results available online. This typically requires publishing the code and data used to produce the publication`s figures and tables on a website; see the supplemental materials section of the information for authors . It gives other researchers easier access to the work, and facilitates fair comparisons. Recognizing the peculiarities of papers presenting deep learning techniques, the editorial board of T-IFS drafted a document with specific instructions about the information to be provided to allow research reproducibility in this kind of papers.
Multimedia content
It is now possible to submit for review and publish in Xplore supporting multimedia material such as speech samples, images, movies, matlab code etc. A multimedia graphical abstract can also be displayed along with the traditional text. More information is available under Multimedia Materials at the IEEE Author Center .
TIFS Volume 19 | 2024
Bg: a modular treatment of bft consensus toward a unified theory of bft replication.
We provide an expressive framework that allows analyzing and generating provably secure, state-of-the-art Byzantine fault-tolerant (BFT) protocols over graph of nodes, a notion formalized in the HotStuff protocol. Our framework is hierarchical, including three layers. The top layer is used to model the message pattern and abstract core functions on which BFT algorithms can be built.
WF-Transformer: Learning Temporal Features for Accurate Anonymous Traffic Identification by Using Transformer Networks
Website Fingerprinting (WF) is a network traffic mining technique for anonymous traffic identification, which enables a local adversary to identify the target website that an anonymous network user is browsing. WF attacks based on deep convolutional neural networks (CNN) get the state-of-the-art anonymous traffic classification performance. However, due to the locality restriction of CNN architecture for feature extraction on sequence data, these methods ignore the temporal feature extraction in the anonymous traffic analysis.
Steganography Embedding Cost Learning With Generative Multi-Adversarial Network
Since the generative adversarial network (GAN) was proposed by Ian Goodfellow et al. in 2014, it has been widely used in various fields. However, there are only a few works related to image steganography so far. Existing GAN-based steganographic methods mainly focus on the design of generator, and just assign a relatively poorer steganalyzer in discriminator, which inevitably limits the performances of their models.
Gait Attribute Recognition: A New Benchmark for Learning Richer Attributes From Human Gait Patterns
Compared to gait recognition, Gait Attribute Recognition (GAR) is a seldom-investigated problem. However, since gait attribute recognition can provide richer and finer semantic descriptions, it is an indispensable part of building intelligent gait analysis systems. Nonetheless, the types of attributes considered in the existing datasets are very limited.
- THIS WEEK: Join NASA’s Dr. Jacqueline Le Moigne as she shares her journey through academia, the private sector, and pivotal roles at NASA, emphasizing her work in signal processing, computer vision, and related technologies. Register now! https://x.com/IEEEsps/status/1785057479606288505
- Join NASA’s Dr. Jacqueline Le Moigne for this interactive webinar as she shares her journey through the realms of signal processing, computer vision, and related technologies, including her pivotal roles at NASA. https://x.com/IEEEsps/status/1782468413551423536
- Great crowd at the Student Job Fair at #ICASSP2024! Thank you to our sponsors for furnishing an exciting, engaging event! https://x.com/IEEEsps/status/1780817453569687559
- Thank you to our Women in Signal Processing Luncheon panelists for their wisdom and insights during today’s event at #ICASSP2024! https://x.com/IEEEsps/status/1780458637338530252
- Free Machine Learning (ML) Lecture Series from IEEE SPS From basics to recent advances, unlock the secrets of ML with Prof. Sergios Theodoridis! https://x.com/IEEEsps/status/1779931297093222415
IEEE SPS Educational Resources

Home | Sitemap | Contact | Accessibility | Nondiscrimination Policy | IEEE Ethics Reporting | IEEE Privacy Policy | Terms | Feedback
© Copyright 2024 IEEE – All rights reserved. Use of this website signifies your agreement to the IEEE Terms and Conditions . A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity.
- Home
- Program (Compact)
- Accepted Papers
- Short Talks
- Proceedings
- Symposium Presenter Information
- Registration
- Student Travel Grants
- Attendee Code of Conduct
- General Info
- Past Conferences
- Conference Organizers
- Technical Committee
MAY 20-23, 2024 AT THE HILTON SAN FRANCISCO UNION SQUARE, SAN FRANCISCO, CA
45th IEEE Symposium on Security and Privacy
Sponsored by the IEEE Computer Society Technical Committee on Security and Privacy in cooperation with the International Association for Cryptologic Research
Registration Button Register (not open)
Call For Papers
Since 1980 in Oakland, the IEEE Symposium on Security and Privacy has been the premier forum for computer security research, presenting the latest developments and bringing together researchers and practitioners. We solicit previously unpublished papers offering novel research contributions in any aspect of security or privacy. Papers may present advances in the theory, design, implementation, analysis, verification, or empirical evaluation and measurement of secure systems. Theoretical papers must make a convincing case for the relevance of their results to practice.
Topics of interest include:
- Applied cryptography
- Attacks with novel insights, techniques, or results
- Authentication, access control, and authorization
- Blockchains and distributed ledger security
- Cloud computing security
- Cyber physical systems security
- Distributed systems security
- Economics of security and privacy
- Embedded systems security
- Formal methods and verification
- Hardware security
- Hate, Harassment, and Online Abuse
- Human-centered security and privacy
- Intrusion detection and prevention
- Machine learning and computer security
- Malware and unwanted software
- Network security and measurement
- Operating systems security
- Privacy-enhancing technologies, anonymity, and censorship
- Program and binary analysis
- Protocol security
- Security and privacy metrics
- Security and privacy policies
- Security architectures
- Security for at-risk populations
- Software supply chain security
- Systems security
- User studies for security and privacy
- Web security and privacy
- Wireless and mobile security/privacy
This topic list is not meant to be exhaustive; S&P is interested in all aspects of computer security and privacy. Papers without a clear application to security or privacy, however, will be considered out of scope and may be rejected without full review.
Systematization of Knowledge Papers
As in past years, we solicit systematization of knowledge (SoK) papers that evaluate, systematize, and contextualize existing knowledge, as such papers can provide a high value to our community. Suitable papers are those that provide an important new viewpoint on an established, major research area, support or challenge long-held beliefs in such an area with compelling evidence, or present a convincing, comprehensive new taxonomy of such an area. Survey papers without such insights are not appropriate and may be rejected without full review. Submissions will be distinguished by the prefix “SoK:” in the title and a checkbox on the submission form. They will be reviewed by the full PC and held to the same standards as traditional research papers, but they will be accepted based on their treatment of existing work and value to the community, and not based on any new research results they may contain. Accepted papers will be presented at the symposium and included in the proceedings. You can find an overview of recent SoK papers at https://oaklandsok.github.io/ .
Submission Deadlines & Decisions (Important Updates)
Similar to 2023, there will be three submission deadlines this year. For each submission, one of the following decisions will be made:
Accept : Papers in this category will be accepted for publication in the proceedings and presentation at the conference. Within one month of acceptance, all accepted papers must submit a camera-ready copy incorporating reviewer feedback. The papers will immediately be published, open access, in the Computer Society’s Digital Library, and they may be cited as “To appear in the IEEE Symposium on Security & Privacy, May 2024”.
Reject : Papers in this category are declined for inclusion in the conference. Rejected papers must wait for one year, from the date of original submission, to resubmit to IEEE S&P. A paper will be judged to be a resubmit (as opposed to a new submission) if the paper is from the same or similar authors, and a reviewer could write a substantially similar summary of the paper compared with the original submission. As a rule of thumb, if there is more than 40% overlap between the original submission and the new paper, it will be considered a resubmission.
Public Meta-Reviews: All accepted papers will be published alongside a meta-review (< 500 words) that lists (a) the reasons the PC decided to accept the paper and (b) concerns the PC has with the paper. Authors will be given the option to write a response to the meta-review (< 500 words) which will be published as part of the meta-review. Authors will be given a draft meta-review at the time of acceptance. Authors will be given the option of addressing some or all of the concerns within one review cycle. A shepherd will remove concerns from the meta-review if they are sufficiently addressed by the revisions. Authors of papers accepted to the third submission cycle will be given the option to have their paper appear in the 2025 proceedings if they are not able to complete revisions in time for the final camera ready deadline.
The goal of this process is to provide greater transparency and to better scope change requests made by reviewers. More information about the reasons behind this change can be found here .
Re-Submission of Major Revisions from Prior Years: Authors resubmitting papers that received Major Revision decisions in 2023 will also be published with the public meta-reviews as described above.
More information about the reasons behind the above changes can be found here .
Important Dates
All deadlines are 23:59:59 AoE (UTC-12).
First deadline
- Paper submission deadline: April 13, 2023
- Early-reject notification: May 22, 2023
- Rebuttal period (interactive): June 19 - June 30, 2023
- Rebuttal text due: June 26, 2023
- Acceptance notification: July 10, 2023
- Camera-ready deadline: August 18, 2023
Second deadline
- Paper submission deadline: August 3, 2023
- Early-reject notification: September 11, 2023
- Rebuttal period (interactive): October 9 - October 20, 2023
- Rebuttal text due: October 16, 2023
- Acceptance notification: October 27, 2023
- Camera-ready deadline: December 8, 2023
Third deadline
- Paper submission deadline: December 6, 2023
- Early-reject notification: January 22, 2024
- Rebuttal period (interactive): February 19 - March 1, 2024
- Rebuttal text due: February 26, 2024
- Acceptance notification: March 8, 2024
- Camera-ready deadline: April 19, 2024
Rebuttal Period
Papers reaching the second round of reviewing will be given an opportunity to write a rebuttal to reviewer questions. The rebuttal period will be interactive, and is separate from the meta-review rebuttal given to accepted papers.
Authors have the opportunity to exchange messages with the reviewers and respond to questions asked. To this end, we will use HotCRP’s anonymous communication feature to enable a communication channel between authors and reviewers. The authors should mainly focus on factual errors in the reviews and concrete questions posed by the reviewers. New research results can also be discussed if they help to clarify open questions. More instructions will be sent out to the authors at the beginning of the rebuttal period.
2023 Major Revision Submissions & Rejected Papers
Papers submitted to one of the 2023 submission cycles may have received a Major Revision or Reject decision. For these papers, we will follow the rules defined in the 2023 Call for Papers, which allow authors of Major Revision papers to submit a revised paper to the next two submission deadlines after the notification. The table below summarizes the eligible 2023 deadlines for papers that received a revise decision or reject decision for a paper submitted to IEEE S&P’23 for each of the three 2023 cycles.
| 2023 deadlines | Revise decision Eligible 2024 deadlines | Reject decision Eligible 2024 deadlines |
| First 2023 (April 1, 2022) | None | Any 2024 deadline |
| Second 2023 (August 19, 2022) | First deadline (April 13,2023) | Second deadline (Aug 3, 2023) Third deadline (Dec 6, 2023) |
| Third 2023 (Dec 2, 2022) | First deadline (April 13, 2023) Second deadline (August 3, 2023) | Third deadline (Dec 6, 2023) |
Instructions for Paper Submission
These instructions apply to both the research papers and systematization of knowledge (SoK) papers. All submissions must be original work; the submitter must clearly document any overlap with previously published or simultaneously submitted papers from any of the authors. Failure to point out and explain overlap will be grounds for rejection. Simultaneous submission of the same paper to another venue with proceedings or a journal is not allowed and will be grounds for automatic rejection. Contact the program committee chairs if there are questions about this policy.
Anonymous Submission
Papers must be submitted in a form suitable for anonymous review: no author names or affiliations may appear on the title page, and papers should avoid revealing authors’ identity in the text. When referring to their previous work, authors are required to cite their papers in the third person, without identifying themselves. In the unusual case in which a third-person reference is infeasible, authors can blind the reference itself. Papers that are not properly anonymized may be rejected without review. PC members who have a genuine conflict of interest with a paper, including the PC Co-Chairs and the Associate Chairs, will be excluded from evaluation and discussion of that paper.
While a paper is under submission to the IEEE Security & Privacy Symposium, authors may choose to give talks about their work, post a preprint of the paper to an archival repository such as arXiv, and disclose security vulnerabilities to vendors. Authors should refrain from widely advertising their results, but in special circumstances they should contact the PC chairs to discuss exceptions. Authors are not allowed to directly contact PC members to discuss their submission.
The submissions will be treated confidentially by the PC chairs and the program committee members. Program committee members are not allowed to share the submitted papers with anyone, with the exception of qualified external reviewers approved by the program committee chairs. Please contact the PC chairs if you have any questions or concerns.
Conflicts of Interest
During submission of a research paper, the submission site will request information about conflicts of interest of the paper’s authors with program committee (PC) members. It is the full responsibility of all authors of a paper to identify all and only their potential conflict-of-interest PC members, according to the following definition. A paper author has a conflict of interest with a PC member when and only when one or more of the following conditions holds:
The PC member is a co-author of the paper.
- For student interns, the student is conflicted with their supervisors and with members of the same research group. If the student no longer works for the organization, then they are not conflicted with a PC member from the larger organization.
The PC member has been a collaborator within the past two years.
The PC member is or was the author’s primary thesis advisor, no matter how long ago.
The author is or was the PC member’s primary thesis advisor, no matter how long ago.
- The PC member is a relative or close personal friend of the author.
For any other situation where the authors feel they have a conflict with a PC member, they must explain the nature of the conflict to the PC chairs, who will mark the conflict if appropriate. The program chairs will review declared conflicts. Papers with incorrect or incomplete conflict of interest information as of the submission closing time are subject to immediate rejection.
Research Ethics Committee
Similar to 2023, IEEE S&P 2024 has a research ethics committee (REC) that will check papers flagged by reviewers as potentially including ethically fraught research. The REC will review flagged papers and may suggest to the PC Chairs rejection of a paper on ethical grounds. The REC consists of members of the PC. Authors are encouraged to review the Menlo Report for general ethical guidelines for computer and information security research.
Ethical Considerations for Vulnerability Disclosure
Where research identifies a vulnerability (e.g., software vulnerabilities in a given program, design weaknesses in a hardware system, or any other kind of vulnerability in deployed systems), we expect that researchers act in a way that avoids gratuitous harm to affected users and, where possible, affirmatively protects those users. In nearly every case, disclosing the vulnerability to vendors of affected systems, and other stakeholders, will help protect users. It is the committee’s sense that a disclosure window of 45 days https://vuls.cert.org/confluence/display/Wiki/Vulnerability+Disclosure+Policy to 90 days https://googleprojectzero.blogspot.com/p/vulnerability-disclosure-faq.html ahead of publication is consistent with authors’ ethical obligations.
Longer disclosure windows (which may keep vulnerabilities from the public for extended periods of time) should only be considered in exceptional situations, e.g., if the affected parties have provided convincing evidence the vulnerabilities were previously unknown and the full rollout of mitigations requires additional time. The authors are encouraged to consult with the PC chairs in case of questions or concerns.
The version of the paper submitted for review must discuss in detail the steps the authors have taken or plan to take to address these vulnerabilities; but, consistent with the timelines above, the authors do not have to disclose vulnerabilities ahead of submission. If a paper raises significant ethical and/or legal concerns, it will be checked by the REC and it might be rejected based on these concerns. The PC chairs will be happy to consult with authors about how this policy applies to their submissions.
Ethical Considerations for Human Subjects Research
Submissions that describe experiments that could be viewed as involving human subjects, that analyze data derived from human subjects (even anonymized data), or that otherwise may put humans at risk should:
- Disclose whether the research received an approval or waiver from each of the authors’ institutional ethics review boards (IRB) if applicable.
- Discuss steps taken to ensure that participants and others who might have been affected by an experiment were treated ethically and with respect.
If a submission deals with any kind of personal identifiable information (PII) or other kinds of sensitive data, the version of the paper submitted for review must discuss in detail the steps the authors have taken to mitigate harms to the persons identified. If a paper raises significant ethical and/or legal concerns, it will be checked by the REC and it might be rejected based on these concerns. The PC chairs will be happy to consult with authors about how this policy applies to their submissions.
Financial and Non-financial competing interests
In the interests of transparency and to help readers form their own judgements of potential bias, the IEEE Symposium on Security & Privacy requires authors and PC members to declare any competing financial and/or non-financial interests in relation to the work described. Authors need to include a disclosure of relevant financial interests in the camera-ready versions of their papers. This includes not just the standard funding lines, but should also include disclosures of any financial interest related to the research described. For example, “Author X is on the Technical Advisory Board of the ByteCoin Foundation,” or “Professor Y is the CTO of DoubleDefense, which specializes in malware analysis.” More information regarding this policy is available here .
Page Limit and Formatting
Submitted papers may include up to 13 pages of text and up to 5 pages for references and appendices, totaling no more than 18 pages. The same applies to camera-ready papers, although, at the PC chairs’ discretion, additional pages may be allowed for references and appendices. Reviewers are not required to read appendices.
Significant Change Starting with the Second Deadline (August 3, 2023):
Papers must be formatted for US letter (not A4) size paper. All submissions must use the IEEE “compsoc” conference proceedings template. LaTeX submissions using the IEEE templates must use IEEEtran.cls version 1.8b with options “conference,compsoc.” (That is, begin your LaTeX document with the line \documentclass[conference,compsoc]{IEEEtran}.). See the “IEEE Demo Template for Computer Society Conferences” Overleaf template for an example.
Papers that fail to use the “compsoc” template (including using the non-compsoc IEEE conference template), modify margins, font, or line spacing, or use egregious space scrunching are subject to rejection without review. Authors are responsible for verifying the paper format. While HotCRP provides some automated checking, the checks are limited.
Conference Submission Server
Submissions must be in Portable Document Format (.pdf). Authors should pay special attention to unusual fonts, images, and figures that might create problems for reviewers.
Links to submission servers:
Cycle 1 : https://spring.sp2024.ieee-security.org/ Cycle 2 : https://summer.sp2024.ieee-security.org/ Cycle 3 : https://winter.sp2024.ieee-security.org/
Publication and Presentation
Authors are responsible for obtaining appropriate publication clearances. One of the authors of the accepted paper is expected to register and present the paper at the conference.
Program Committee
| Patrick Traynor | University of Florida |
| William Enck | North Carolina State University |
Associate Chairs
| Aanjhan Ranganathan | Northeastern University |
| Adam Bates | University of Illinois Urbana-Champaign |
| Andrew Paverd | Microsoft |
| Hamed Okhravi | MIT Lincoln Laboratory |
| Matt Fredrikson | Carnegie Mellon University |
| Matteo Maffei | TU Wein |
| Micah Sherr | Georgetown University |
| Sascha Fahl | CISPA |
| Tiffany Bao | Arizona State University |
| Yuan Tian | University of California, Los Angelos |
| René Mayrhofer | Johannes Kepler University Linz |
| Abbas Acar | Florida International University |
| AbdelRahman Abdou | Carleton University |
| Abhishek Jain | Johns Hopkins University |
| Adam Oest | Paypal, Inc. |
| Adam Doupé | Arizona State University |
| Adam Bates | University of Illinois at Urbana-Champaign |
| Adwait Nadkarni | William & Mary |
| Ajith Suresh | Technology Innovation Institute (TII) |
| Alena Naiakshina | Ruhr University Bochum |
| Alessandra Scafuro | NCSU |
| Alexander Block | Georgetown University & University of Maryland, College Park |
| Alfred Chen | University of California, Irvine |
| Alina Oprea | Northeastern University |
| Allison McDonald | Boston University |
| Amit Kumar Sikder | Georgia Institute of Technology |
| Andrei Sabelfeld | Chalmers University of Technology |
| Ang Chen | Rice University |
| Angelos Stavrou | Virginia Tech |
| Aniket Kate | Purdue University / Supra |
| Anindya Maiti | University of Oklahoma |
| Anupam Das | North Carolina State University |
| Apu Kapadia | Indiana University Bloomington |
| Aravind Machiry | Purdue University |
| Aurélien Francillon | EURECOM |
| Ben Stock | CISPA Helmholtz Center for Information Security |
| Benjamin Ujcich | Georgetown University |
| Benjamin Dowling | The University of Sheffield |
| Blaine Hoak | University of Wisconsin-Madison |
| Blase Ur | University of Chicago |
| Bogdan Groza | Universitatea Politehnica Timisoara |
| Brad Reaves | North Carolina State University |
| Brendan Saltaformaggio | Georgia Tech |
| Byoungyoung Lee | Seoul National University |
| Carrie Gates | Bank of America |
| Carter Yagemann | The Ohio State University |
| Casey Meehan | Vector Institute |
| Chaowei Xiao | Arizona State University |
| Chengyu Song | UC Riverside |
| Christian Wressnegger | Karlsruhe Institute of Technology (KIT) |
| Christian Peeters | Harbor Labs |
| Christina Garman | Purdue University |
| Christina Pöpper | New York University Abu Dhabi |
| Christopher A. Choquette-Choo | Google Research, Brain Team |
| Claudio Soriente | NEC laboratories Europe |
| Cristian-Alexandru Staicu | CISPA Helmholtz Center for Information Security |
| Daniel Genkin | Georgia Tech |
| Daniel Votipka | Tufts University |
| Dave (Jing) Tian | Purdue University |
| David Barrera | Carleton University |
| David Cash | University of Chicago |
| Debajyoti Das | KU Leuven |
| Deepak Kumar | Stanford University |
| Derrick McKee | MIT Lincoln Laboratory |
| Dimitrios Papadopoulos | The Hong Kong University of Science and Technology |
| Dominik Wermke | CISPA |
| Drew Davidson | University of Kansas |
| Earlence Fernandes | UC San Diego |
| Eleonora Losiouk | University of Padua |
| Emily Wenger | University of Chicago and Meta AI |
| Eric Pauley | University of Wisconsin-Madison |
| Ethan Cecchetti | University of Maryland / University of Wisconsin - Madison |
| Evgenios Kornaropoulos | George Mason University |
| Eyal Ronen | Tel Aviv University |
| Eyal Ronen | Tel Aviv University |
| Fabio Pierazzi | King's College London |
| Faysal Shezan | University of Texas at Arlington |
| Fengwei Zhang | Southern University of Science and Technology (SUStech) |
| Florian Schaub | University of Michigan |
| Florian Kerschbaum | University of Waterloo |
| Florian Tramèr | ETH Zürich |
| Fnu Suya | University of Maryland |
| Frank Li | Georgia Institute of Technology |
| Frank Piessens | KU Leuven |
| Franziska Boenisch | Vector Institute |
| Furkan Alaca | Queen's University |
| Gang Wang | University of Illinois at Urbana-Champaign |
| Gary Tan | The Pennsylvania State University |
| Georgios Portokalidis | IMDEA Software Institute |
| Ghassan Karame | Ruhr-University Bochum |
| Giancarlo Pellegrino | CISPA Helmholtz Center for Information Security |
| Giovanni Camurati | ETH Zurich |
| Grant Ho | UCSD and UChicago |
| Guevara Noubir | Northeastern University |
| Guillermo Suarez-Tangil | IMDEA Networks Institute |
| Habiba Farrukh | Purdue University |
| Hang Zhang | Georgia Institute of Technology |
| Haya Shulman | Goethe-Universität Frankfurt | Fraunhofer SIT | ATHENE |
| Heather Zheng | University of Chicago |
| Heng Yin | University of California Riverside |
| Hovav Shacham | The University of Texas at Austin |
| Hyungjoon Koo | Sungkyunkwan University |
| Insu Yun | KAIST |
| Ioana Boureanu | Univ. of Surrey, Surrey Centre for Cybersecurity |
| Jason Nieh | Columbia University |
| Jeremiah Blocki | Purdue University |
| Jianjun Chen | Tsinghua University |
| Jiarong Xing | Rice University |
| Jiska Classen | TU Darmstadt, SEEMOO |
| Johanna Ullrich | SBA Research/University of Vienna |
| Jon McCune | Google LLC |
| Jun Han | Yonsei University |
| Kangjie Lu | University of Minnesota |
| Karen Sowon | Postdoctoral research associate, Carnegie Mellon University |
| Kartik Nayak | Duke University |
| Kassem Fawaz | University of Wisconsin-Madison |
| Kavita Kumari | Technical University of Darmstadt |
| Kelsey Fulton | Colorado School of Mines |
| Kevin Borgolte | Ruhr University Bochum |
| Kevin Butler | University of Florida |
| Kexin Pei | Columbia University |
| Kovila P.L. Coopamootoo | King's College London |
| Lejla Batina | Radboud University |
| Leonardo Babun | Johns Hopkins Applied Physics Laboratory |
| Liang Wang | Princeton University |
| Lianying Zhao | Carleton University |
| Liqun Chen | University of Surrey |
| Liz Izhikevich | Stanford University |
| Luis Vargas | Harbor Labs |
| Lujo Bauer | Carnegie Mellon University |
| Mahmood Sharif | Tel Aviv University |
| Marco Squarcina | TU Wien |
| Mariana Raykova | |
| Markus Miettinen | Technical University of Darmstadt |
| Marshini Chetty | University of Chicago |
| Mathy Vanhoef | KU Leuven |
| Matthew Lentz | Duke University |
| Mauro Conti | University of Padua |
| Michael Reiter | Duke University |
| Michael Waidner | Technische Universität Darmstadt |
| Michail Maniatakos | NYU Abu Dhabi |
| Michalis Polychronakis | Stony Brook University |
| Mridula Singh | CISPA Helmholtz Center for Information Security |
| Murtuza Jadliwala | University of Texas at San Antonio |
| Nick Nikiforakis | Stony Brook University |
| Nicolas Papernot | University of Toronto and Vector Institute and Google |
| Nikita Borisov | University of Illinois at Urbana-Champaign |
| Nikos Vasilakis | Brown University |
| Ning Zhang | Washington University in St. Louis |
| Noel Warford | University of Maryland |
| Olivier Levillain | Télécom SudParis |
| Olya Ohrimenko | The University of Melbourne |
| Omar Chowdhury | Stony Brook University |
| Omer Akgul | University of Maryland |
| Panos Papadimitratos | KTH Royal Institute of Technology |
| Pardis Emami-Naeini | Duke University |
| Patrick McDaniel | University of Wisconsin-Madison |
| Paul Pearce | Georgia Institute of Technology |
| Paul Martin | Harbor Labs |
| Peter Snyder | Brave Software |
| Pratyush Mishra | University of Pennsylvania |
| Qiushi Wu | University of Minnesota |
| Quinn Burke | University of Wisconsin-Madison |
| Rahul Chatterjee | University of Wisconsin-Madison |
| Rakibul Hasan | Arizona State University |
| Ramakrishnan Sundara Raman | University of Michigan |
| Ramya Jayaram Masti | Ampere Computing |
| Reza Shokri | National University of Singapore |
| Ruoyu “Fish” Wang | Arizona State University |
| Ryan Wails | Georgetown University & U.S. Naval Research Laboratory |
| Ryan Sheatsley | University of Wisconsin-Madison |
| Saba Eskandarian | University of North Carolina at Chapel Hill |
| Saman Zonouz | Georgia Tech |
| Santiago Torres-Arias | Purdue University |
| Sara Rampazzi | University of Florida |
| Sathvik Prasad | North Carolina State University |
| Sazzadur Rahaman | University of Arizona |
| Sebastian Roth | TU Wien |
| Selcuk Uluagac | Florida International University |
| Serge Egelman | UC Berkeley / ICSI / AppCensus, Inc. |
| Shamaria Engram | MIT Lincoln Laboratory |
| Shitong Zhu | Meta Platforms, Inc. |
| Shruti Tople | Microsoft |
| Shuai Wang | HKUST |
| Sisi Duan | Tsinghua University |
| Sofia Celi | Brave Software |
| Soheil Khodayari | CISPA Helmholtz Center for Information Security |
| Srdjan Capkun | ETH Zurich |
| Suman Jana | Columbia University |
| Sunil Manandhar | IBM Research |
| Sven Bugiel | CISPA Helmholtz Center for Information Security |
| Sze Yiu Chau | The Chinese University of Hong Kong |
| Takeshi Sugawara | The University of Electro-Communications |
| Tianhao Wang | University of Virginia |
| Tobias Fiebig | Max-Planck-Institut für Informatik |
| Tushar Jois | Johns Hopkins University |
| Tyler Kaczmarek | MIT Lincoln Laboratory |
| Vasileios Kemerlis | Brown University |
| Vincent Bindschaedler | University of Florida |
| Vipul Goyal | NTT Research and CMU |
| Wajih Ul Hassan | University of Virginia |
| Wei Meng | The Chinese University of Hong Kong |
| Weiteng Chen | Microsoft Research, Redmond |
| Wenjing Lou | Virginia Tech |
| William Robertson | Northeastern University |
| Xiaojing Liao | Indiana University Bloomington |
| Xiapu Luo | The Hong Kong Polytechnic University |
| Xinlei He | CISPA Helmholtz Center for Information Security |
| Xusheng Xiao | Arizona State University |
| Yan Chen | Northwestern University |
| Yang Zhang | CISPA Helmholtz Center for Information Security |
| Yanick Fratantonio | |
| Yasemin Acar | Paderborn University & George Washington University |
| Yasemin Acar | Paderborn University |
| Yinzhi Cao | Johns Hopkins University |
| Yixin Sun | University of Virginia |
| Yongdae Kim | KAIST |
| Yuval Yarom | University of Adelaide |
| Z. Berkay Celik | Purdue University |
| Zakir Durumeric | Stanford University |
| Zane Ma | Georgia Institute of Technology |
| Zhen Huang | DePaul University |
| Zhiqiang Lin | Ohio State University |
| Zhiyun Qian | University of California, Riverside |
| Ziqiao Zhou | Microsoft Research |
- Create Account
Main navigation dropdown
Publications, recent advances in network security management, publication date, manuscript submission deadline, 16 november 2021, call for papers.
As the backbone of communications amongst objects, humans, companies, and administrations, the Internet has become a great integration platform capable of efficiently interconnecting billions of entities, from RFID chips to data centers. This platform provides access to multiple hardware and virtualized resources (servers, networking, storage, applications, connected objects) ranging from cloud computing to Internet-of-Things infrastructures. From these resources that may be hosted and distributed amongst different providers and tenants, the building and operation of complex and value-added networked systems is enabled.
These networked systems are, however, subject to a large variety of security attacks, such as distributed denial-of-service, man-in-the-middle, web-injection and malicious software attacks, orchestrated in a more or less stealthy manner through the Internet. While they are gaining in sophistication and coordination (i.e. advanced persistent threats), these attacks may affect the fundamental security goals of confidentiality, integrity, availability and non-repudiation of resources. The accessibility, distribution, and increased complexity of networked systems make them particularly vulnerable targets. In that context, cybersecurity techniques offer new perspectives for protecting these networked systems, through the elaboration of intelligent and efficient management methods for detecting, analyzing and mitigating such attacks.
IEEE Transactions on Network and Service Management (IEEE TNSM) is a premier journal for timely publication of archival research on the management of networks, systems, services and applications. Following the success of the recent TNSM Special Issues on cybersecurity techniques for managing networked systems in 2020 and 2021, this Special Issue will focus on recent advances in network security management. We welcome submissions addressing the important challenges (see the non-exhaustive list of topics below) and presenting novel research or experimentation results. Survey papers that offer an insightful perspective on related work and identify key challenges for future research will be considered as well. We look forward to your submissions!
About the Special Issue
Topics of interest for this Special Issue, include, but are not limited to the following:
- Network and service management for security
- Security of network and service management
- Security management architecture, protocols and APIs
- Secure and resilient design and deployment of networked systems
- Monitoring and detection of threats and attacks
- Artificial intelligence, machine learning for cyber-security
- Analytics and big data for security management
- Modeling for security management
- Configuration and orchestration of security mechanisms
- Algorithms for security management
- Security automation, policy-based management
- NFV-based security functions and services
- Security of programmable components
- Chaining and orchestration of security functions
- Distributed security management
- Intrusion detection, tolerance, prevention, and response
- Resilience against large-scale distributed attacks
- Trust and identity management
- Verification and enforcement of security properties
- Vulnerability prevention and remediation
- Performance of security management
- Security of cloud applications and services
- Security of data-center infrastructures
- Security of 5G networks and services
- Security of smart environments
- Security of Internet of Things
- Security of SCADA, industrial and health networks
- Security of SDN- and NFV-based systems
- Network forensics, auditing and responses to incidents
- Privacy-preserving solutions for cybersecurity
- Detailed experience reports from experimental testbeds
- Security-related business, regulation, and legal aspects
Submission Format
Papers will be evaluated based on their originality, presentation, relevance and contribution to the field of security of software-defined virtualized systems, as well as their overall quality and suitability for the special issue. The submitted papers must be written in good English and describe original research which has not been published nor currently under review by other journals or conferences. Previously published conference papers should be clearly identified by the authors at the initial submission stage and an explanation should be provided of how such papers have been extended in order to be considered for this Special Issue.
Author guidelines for the preparation of manuscript (including number of pages and potential extra page costs) can be found on the IEEE TNSM Submit a Manuscript page.
For more information, please contact Remi Badonnel .
Submission Guidelines
All manuscripts and any supplementary material should be submitted through the IEEE Manuscript Central service . Authors must indicate in the submission cover letter that their manuscript is intended for the “Recent Advances in Network Security Management ” Special Issue.
Important Dates
Paper Submission Date: 30 October 2021 16 November 2021 (Extended Deadline) Notification of Acceptance: 15 February 2022 Publication Date*: 1 June 2022
(* online published version will be available in IEEE Xplore after the camera ready version has been submitted with final DOI)
Guest Editors
Rémi Badonnel (Lead) Telecom Nancy – LORIA / INRIA, France
Sandra Scott-Hayward Queen's University Belfast, UK
Carol Fung Virginia Commonwealth University, United States
Qi Li Tsinghua University, China
Jie Zhang Nanyang Technological University (NTU), Singapore
Cristian Hesselman SIDN, The Netherlands
Fulvio Valenza Politecnico di Torino, Italy
- Home
- Program (Compact)
- Accepted Papers
- Short Talks
- Symposium Presenter Information
- Registration (Not Open)
- Student Travel Grants
- Attendee Code of Conduct
- General Info
- Past Conferences
- Conference Organizers
- Technical Committee
MAY 12-15, 2025 AT THE HYATT REGENCY SAN FRANCISCO, SAN FRANCISCO, CA
46th IEEE Symposium on Security and Privacy
Sponsored by the IEEE Computer Society Technical Committee on Security and Privacy in cooperation with the International Association for Cryptologic Research
Registration Button Register (not open)
Call for Papers
Since 1980 in Oakland, the IEEE Symposium on Security and Privacy has been the premier forum for computer security research, presenting the latest developments and bringing together researchers and practitioners. We solicit previously unpublished papers offering novel research contributions in any aspect of security or privacy. Papers may present advances in the theory, design, implementation, analysis, verification, or empirical evaluation and measurement of secure systems. Theoretical papers must make a convincing case for the relevance of their results to practice.
Topics of interest include:
- Applied cryptography
- Attacks with novel insights, techniques, or results
- Authentication, access control, and authorization
- Blockchains and distributed ledger security
- Cloud computing security
- Cyber physical systems security
- Distributed systems security
- Economics of security and privacy
- Embedded systems security
- Formal methods and verification
- Hardware security
- Hate, Harassment, and Online Abuse
- Human-centered security and privacy
- Intrusion detection and prevention
- Machine learning and computer security
- Malware and unwanted software
- Network security and measurement
- Operating systems security
- Privacy-enhancing technologies, anonymity, and censorship
- Program and binary analysis
- Protocol security
- Security and privacy metrics
- Security and privacy policies
- Security architectures
- Security for at-risk populations
- Software supply chain security
- Systems security
- User studies for security and privacy
- Web security and privacy
- Wireless and mobile security/privacy
This topic list is not meant to be exhaustive; S&P is interested in all aspects of computer security and privacy. Papers without a clear application to security or privacy, however, will be considered out of scope and may be rejected without full review.

Systematization of Knowledge Papers
As in past years, we solicit systematization of knowledge (SoK) papers that evaluate, systematize, and contextualize existing knowledge, as such papers can provide a high value to our community. Suitable papers are those that provide an important new viewpoint on an established, major research area, support or challenge long-held beliefs in such an area with compelling evidence, or present a convincing, comprehensive new taxonomy of such an area. Survey papers without such insights are not appropriate and may be rejected without full review. Submissions will be distinguished by the prefix “SoK:” in the title and a checkbox on the submission form. They will be reviewed by the full PC and held to the same standards as traditional research papers, but they will be accepted based on their treatment of existing work and value to the community, and not based on any new research results they may contain. Accepted papers will be presented at the symposium and included in the proceedings. You can find an overview of recent SoK papers at https://oaklandsok.github.io .
Submission Deadlines & Decisions
Similar to 2024, for each submission, one of the following decisions will be made:
Accept: Papers in this category will be accepted for publication in the proceedings and presentation at the conference. Within one month of acceptance, all accepted papers must submit a camera-ready copy incorporating reviewer feedback. The papers will immediately be published, open access, in the Computer Society’s Digital Library, and they may be cited as “To appear in the IEEE Symposium on Security & Privacy, May 2025”. After the symposium, papers will be behind a paywall for one year before they are again made open access.
Reject: Papers in this category are declined for inclusion in the conference. Rejected papers must wait for one year, from the date of original submission, to resubmit to IEEE S&P. A paper will be judged to be a resubmit (as opposed to a new submission) if the paper is from the same or similar authors, and a reviewer could write a substantially similar summary of the paper compared with the original submission. As a rule of thumb, if there is more than 40% overlap between the original submission and the new paper, it will be considered a resubmission.
Public Meta-Reviews: Similar to 2024, all accepted papers will be published with a meta-review (< 500 words) in the final PDF that lists: (a) the reasons the PC decided to accept the paper and (b) concerns the PC has with the paper. Authors will be given the option to write a response to the meta-review (< 500 words) which will be published as part of the meta-review. Authors will be given a draft meta-review at the time of acceptance. Authors will be given the option of addressing some or all of the concerns within one review cycle. A shepherd will remove concerns from the meta-review if they are sufficiently addressed by the revisions. The goal of this process is to provide greater transparency and to better scope change requests made by reviewers. More information about the reasons behind this change can be found on the 2024 IEEE S&P website .
Symposium Event (Important Changes)
The number of papers accepted to IEEE S&P continues to grow substantially each year. Due to conference venue limitations and costs, each accepted paper will have: (a) a short talk presentation (e.g., 5-7 minutes, length determined based on the number of accepted papers) and (b) a poster presentation immediately following the talk session containing the paper. All accepted papers are required to present both a short talk and a poster.
Important Dates
All deadlines are 23:59:59 AoE (UTC-12).
First deadline
- Paper submission deadline: June 6, 2024
- Early-reject notification: July 22, 2024
- Rebuttal period (interactive): August 19 - August 30, 2024
- Rebuttal text due: August 26, 2024
- Acceptance notification: September 9, 2024
- Camera-ready deadline: October 18, 2024
Second deadline
- Paper submission deadline: November 14, 2024
- Early-reject notification: January 20, 2025
- Rebuttal period (interactive): February 17 - February 28, 2025
- Rebuttal text due: February 24, 2025
- Acceptance notification: March 10, 2025
- Camera-ready deadline: April 18, 2025
Rebuttal Period
Papers reaching the second round of reviewing will be given an opportunity to write a rebuttal to reviewer questions. The rebuttal period will be interactive, and is separate from the meta-review rebuttal given to accepted papers. Authors have the opportunity to exchange messages with the reviewers and respond to questions asked. To this end, we will use HotCRP’s anonymous communication feature to enable a communication channel between authors and reviewers. The authors should mainly focus on factual errors in the reviews and concrete questions posed by the reviewers. New research results can also be discussed if they help to clarify open questions. More instructions will be sent out to the authors at the beginning of the rebuttal period.
Resubmission of Rejected Papers
As with previous IEEE S&P symposia with multiple submission cycles, rejected papers must wait one year before resubmission to IEEE S&P. Given the move from three submission deadlines in 2024 to two submission deadlines in 2025, rejected papers are eligible to submit according to the table below.
| First 2024 (April 13, 2023) | Either 2025 deadline |
| Second 2024 (August 3, 2023) | Either 2025 deadline |
| Third 2024 (Dec 6, 2023) | Second deadline (Nov 14, 2024) |
Instructions for Paper Submission
These instructions apply to both the research papers and systematization of knowledge (SoK) papers. All submissions must be original work; the submitter must clearly document any overlap with previously published or simultaneously submitted papers from any of the authors. Failure to point out and explain overlap will be grounds for rejection. Simultaneous submission of the same paper to another venue with proceedings or a journal is not allowed and will be grounds for automatic rejection. Contact the program committee chairs if there are questions about this policy.
Anonymous Submission
Papers must be submitted in a form suitable for anonymous review: no author names or affiliations may appear on the title page, and papers should avoid revealing authors’ identity in the text. When referring to their previous work, authors are required to cite their papers in the third person, without identifying themselves. In the unusual case in which a third-person reference is infeasible, authors can blind the reference itself. Papers that are not properly anonymized may be rejected without review. PC members who have a genuine conflict of interest with a paper, including the PC Co-Chairs and the Associate Chairs, will be excluded from evaluation and discussion of that paper.
While a paper is under submission to the IEEE Security & Privacy Symposium, authors may choose to give talks about their work, post a preprint of the paper to an archival repository such as arXiv, and disclose security vulnerabilities to vendors. Authors should refrain from widely advertising their results, but in special circumstances they should contact the PC chairs to discuss exceptions. Authors are not allowed to directly contact PC members to discuss their submission.
The submissions will be treated confidentially by the PC chairs and the program committee members. Program committee members are not allowed to share the submitted papers with anyone, with the exception of qualified external reviewers approved by the program committee chairs. Please contact the PC chairs if you have any questions or concerns.
Conflicts of Interest
During submission of a research paper, the submission site will request information about conflicts of interest of the paper’s authors with program committee (PC) members. It is the full responsibility of all authors of a paper to identify all and only their potential conflict-of-interest PC members, according to the following definition. A paper author has a conflict of interest with a PC member when and only when one or more of the following conditions holds:
The PC member is a co-author of the paper.
- For student interns, the student is conflicted with their supervisors and with members of the same research group. If the student no longer works for the organization, then they are not conflicted with a PC member from the larger organization.
- The PC member has been a collaborator within the past two years.
- The PC member is or was the author’s primary thesis advisor, no matter how long ago.
- The author is or was the PC member’s primary thesis advisor, no matter how long ago.
- The PC member is a relative or close personal friend of the author.
For any other situation where the authors feel they have a conflict with a PC member, they must explain the nature of the conflict to the PC chairs, who will mark the conflict if appropriate. The program chairs will review declared conflicts. Papers with incorrect or incomplete conflict of interest information as of the submission closing time are subject to immediate rejection.
Research Ethics Committee
Similar to 2024, IEEE S&P 2025 has a research ethics committee (REC) that will check papers flagged by reviewers as potentially including ethically fraught research. The REC will review flagged papers and may suggest to the PC Chairs rejection of a paper on ethical grounds. The REC consists of members of the PC. Authors are encouraged to review the Menlo Report for general ethical guidelines for computer and information security research.
Ethical Considerations for Vulnerability Disclosure
Where research identifies a vulnerability (e.g., software vulnerabilities in a given program, design weaknesses in a hardware system, or any other kind of vulnerability in deployed systems), we expect that researchers act in a way that avoids gratuitous harm to affected users and, where possible, affirmatively protects those users. In nearly every case, disclosing the vulnerability to vendors of affected systems, and other stakeholders, will help protect users. It is the committee’s sense that a disclosure window of 45 days https://vuls.cert.org/confluence/display/Wiki/Vulnerability+Disclosure+Policy to 90 days https://googleprojectzero.blogspot.com/p/vulnerability-disclosure-faq.html ahead of publication is consistent with authors’ ethical obligations.
Longer disclosure windows (which may keep vulnerabilities from the public for extended periods of time) should only be considered in exceptional situations, e.g., if the affected parties have provided convincing evidence the vulnerabilities were previously unknown and the full rollout of mitigations requires additional time. The authors are encouraged to consult with the PC chairs in case of questions or concerns.
The version of the paper submitted for review must discuss in detail the steps the authors have taken or plan to take to address these vulnerabilities; but, consistent with the timelines above, the authors do not have to disclose vulnerabilities ahead of submission. If a paper raises significant ethical and/or legal concerns, it will be checked by the REC and it might be rejected based on these concerns. The PC chairs will be happy to consult with authors about how this policy applies to their submissions.
Note : Submitted papers should not include full CVE identifiers in order to preserve the anonymity of the submission.
Ethical Considerations for Human Subjects Research
Submissions that describe experiments that could be viewed as involving human subjects, that analyze data derived from human subjects (even anonymized data), or that otherwise may put humans at risk should:
- Disclose whether the research received an approval or waiver from each of the authors’ institutional ethics review boards (IRB) if applicable.
- Discuss steps taken to ensure that participants and others who might have been affected by an experiment were treated ethically and with respect.
If a submission deals with any kind of personal identifiable information (PII) or other kinds of sensitive data, the version of the paper submitted for review must discuss in detail the steps the authors have taken to mitigate harms to the persons identified. If a paper raises significant ethical and/or legal concerns, it will be checked by the REC and it might be rejected based on these concerns. The PC chairs will be happy to consult with authors about how this policy applies to their submissions.
Financial and Non-financial competing interests
In the interests of transparency and to help readers form their own judgements of potential bias, the IEEE Symposium on Security & Privacy requires authors and PC members to declare any competing financial and/or non-financial interests in relation to the work described. Authors need to include a disclosure of relevant financial interests in the camera-ready versions of their papers. This includes not just the standard funding lines, but should also include disclosures of any financial interest related to the research described. For example, “Author X is on the Technical Advisory Board of the ByteCoin Foundation,” or “Professor Y is the CTO of DoubleDefense, which specializes in malware analysis.” More information regarding this policy is available here .
Page Limit and Formatting (Important Changes)
Submitted papers may include up to 13 pages of text and up to 5 pages for references and appendices, totaling no more than 18 pages. All text and figures past page 13 must be clearly marked as part of the appendix. The final camera-ready paper must be no more than 18 pages, although, at the PC chairs’ discretion, additional pages may be allowed. Reviewers are not required to read appendices.
Papers must be formatted for US letter (not A4) size paper. All submissions must use the IEEE “compsoc” conference proceedings template. LaTeX submissions using the IEEE templates must use IEEEtran.cls version 1.8b with options “conference,compsoc.” (That is, begin your LaTeX document with the line \documentclass[conference,compsoc]{IEEEtran}.). See the “IEEE Demo Template for Computer Society Conferences” Overleaf template for an example. We are not aware of an MS Word template that matches this style.
Papers that fail to use the “compsoc” template (including using the non-compsoc IEEE conference template), modify margins, font, or line spacing, or use egregious space scrunching are subject to rejection without review. Authors are responsible for verifying the paper format (e.g., compare with the above linked Overleaf template) . While HotCRP provides some automated checking, the checks are limited. Note that some LaTeX packages (e.g., \usepackage{usenix}) override the compsoc formatting and must be removed.
Conference Submission Server
Submissions must be in Portable Document Format (.pdf). Authors should pay special attention to unusual fonts, images, and figures that might create problems for reviewers.
Submission server : https://cycle1.sp2025.ieee-security.org/
Publication and Presentation
Authors are responsible for obtaining appropriate publication clearances. One of the authors of the accepted paper is expected to register and present the paper at the conference.
Program Committee
| William Enck | North Carolina State University |
| Cristina Nita-Rotaru | Northeastern University |
Associate Chairs
| Adwait Nadkarni | William & Mary |
| Alex Kapravelos | North Carolina State University |
| Amir Houmansadr | University of Massachusetts Amherst |
| Batista Biggio | University of Cagliari |
| Christina Garman | Purdue University |
| Ian Miers | University of Maryland, College Park |
| Ioana Boureanu | Univ. of Surrey, Surrey Centre for Cybersecurity |
| Sara Rampazzi | University of Florida |
| Sascha Fahl | CISPA |
| William Robertson | Northeastern University |
| René Mayrhofer | Johannes Kepler University Linz |
| Blase Ur | University of Chicago |
| Adam Bates | University of Illinois at Urbana-Champaign |
| Adam Doupé | Arizona State University |
| Adam Oest | Amazon |
| Adil Ahmad | Arizona State University |
| Ahmad-Reza Sadeghi | Technical University Darmstadt |
| Alena Naiakshina | Ruhr University Bochum |
| Alesia Chernikova | Northeastern University |
| Alessandro Brighente | University of Padova |
| Alexander Block | Georgetown University & University of Maryland |
| Alexandra Dmitrienko | University of Wuerzburg |
| Alexios Voulimeneas | TU Delft |
| Ali Abbasi | CISPA Helmholtz Center for Information Security |
| Álvaro Feal | Northeastern University |
| Amit Seal Ami | William & Mary |
| Ana-Maria Cretu | EPFL, Lausanne, Switzerland |
| Andrei Sabelfeld | Chalmers University of Technology |
| Andrew Kwong | UNC Chapel Hill |
| Andrew Paverd | Microsoft |
| Ang Chen | University of Michigan |
| Angelos Stavrou | Virginia Tech |
| Aniket Kate | Purdue University / Supra Research |
| Antonio Bianchi | Purdue University |
| Anupam Das | North Carolina State University |
| Anwar Hithnawi | ETH Zurich |
| Aravind Machiry | Purdue University |
| Arslan Khan | Pennsylvania State University/ Purdue University |
| Arthur Gervais | UCL |
| Ashish Kundu | Cisco Research |
| Bailey Kacsmar | University of Alberta |
| Ben Stock | CISPA Helmholtz Center for Information Security |
| Ben Weintraub | Northeastern University |
| Ben Zhao | University of Chicago |
| Benjamin Beurdouche | Mozilla |
| Blaine Hoak | University of Wisconsin-Madison |
| Bo Chen | Michigan Technological University |
| Bogdan Carbunar | Florida International University |
| Brad Reaves | North Carolina State University |
| Brendan Saltaformaggio | Georgia Institute of Technology |
| Byoungyoung Lee | Seoul National University |
| Chao Zhang | Tsinghua University |
| Charalampos Papamanthou | Yale University |
| Chen-Da Liu-Zhang | Lucerne University of Applied Sciences and Arts & Web3 Foundation |
| Christof Ferreira Torres | ETH Zürich |
| Christopher A. Choquette-Choo | Google DeepMind |
| Claudio Soriente | NEC Laboratories Europe |
| Constantin Catalin Dragan | University of Surrey |
| Daniel Genkin | Georgia Tech |
| Daniel Votipka | Tufts University |
| Daniele Cono D'Elia | Sapienza University of Rome |
| David Balash | University of Richmond |
| Debajyoti Das | KU Leuven |
| Deian Stefan | UC San Diego |
| Dimitrios Papadopoulos | HKUST |
| Diogo Barradas | University of Waterloo |
| Dominik Wermke | NC State |
| Dongdong She | Hong Kong University of Science and Technology |
| Duc Le | Visa Research |
| Earlence Fernandes | UC San Diego |
| Eleonora Losiouk | University of Padua |
| Elisa Bertino | Purdue University |
| Emiliano De Cristofaro | UC Riverside |
| Emily Wenger | Duke University |
| Endadul Hoque | Syracuse University |
| Eric Pauley | University of Wisconsin–Madison |
| Eysa Lee | Brown University |
| Fabio De Gaspari | Sapienza Università di Roma |
| Faysal hossain Shezan | University of Texas at Arlington |
| Fengwei Zhang | Southern University of Science and Technology |
| Florian Kerschbaum | University of Waterloo |
| Florian Tramer | ETH Zurich |
| Frank Li | Georgia Institute of Technology |
| Frank Piessens | KU Leuven |
| Gang Wang | University of Illinois at Urbana-Champaign |
| Gaoning Pan | Hangzhou Dianzi University |
| Georgios Smaragdakis | Delft University of Technology |
| Giovanni Camurati | ETH Zurich |
| Giovanni Cherubin | Microsoft |
| Giulia Fanti | Carnegie Mellon University |
| Giuseppe Ateniese | George Mason University |
| Guangdong Bai | The University of Queensland |
| Guangliang Yang | Fudan University |
| Guanhong Tao | University of Utah |
| Guevara Noubir | Northeastern University |
| Guillermo Suarez-Tangil | IMDEA Networks Institute |
| Habiba Farrukh | University of California, Irvine |
| Haoyu Wang | Huazhong University of Science and Technology |
| Harshad Sathaye | ETH Zürich |
| Haya Schulmann | Goethe-Universität Frankfurt |
| Heather Zheng | University of Chicago |
| Heng Yin | UC Riverside |
| Homa Alemzadeh | University of Virginia |
| Hongxin Hu | University at Buffalo |
| Hyungsub Kim | Purdue University & Indiana University |
| Imtiaz Karim | Purdue University |
| Jack Doerner | Brown University |
| Jaron Mink | Arizona State University |
| Jason Nieh | Columbia University |
| Jason (Minhui) Xue | CSIRO’s Data61 |
| Jeremiah Blocki | Purdue University |
| Jiarong Xing | Rice University |
| Jiska Classen | Hasso Plattner Institute |
| Jon McCune | |
| Jonas Hielscher | Ruhr University Bochum |
| Joseph Bonneau | a16z crypto research and New York University |
| Jun Han | KAIST |
| Kaihua Qin | Yale University |
| Kelsey Fulton | Colorado School of Mines |
| Kevin Borgolte | Ruhr University Bochum |
| Kevin Butler | University of Florida |
| Klaus v. Gleissenthall | VU Amsterdam |
| Kun Sun | George Mason University |
| Lorenzo Cavallaro | University College London |
| Lucianna Kiffer | ETH Zurich |
| Lucy Simko | Barnard College |
| Luyi Xing | Indiana University Bloomington |
| Man-Ki Yoon | North Carolina State University |
| Marco Squarcina | TU Wien |
| Maria Apostolaki | Princeton University |
| Marina Blanton | University at Buffalo |
| Markus Miettinen | Frankfurt University of Applied Sciences |
| Martin Henze | RWTH Aachen University & Fraunhofer FKIE |
| Matthew Jones | Block |
| Matthew Lentz | Duke University and Broadcom |
| Mauro Conti | University of Padua |
| Meera Sridhar | University of North Carolina Charlotte |
| Meng Shen | Beijing Institute of Technology |
| Michael Waidner | Technische Universität Darmstadt |
| Mohammad Islam | University of Texas at Arlington |
| Mridula Singh | CISPA Helmholtz Center for Information Security |
| Mu Zhang | University of Utah |
| Mulong Luo | The University of Texas at Austin |
| Muoi Tran | ETH Zurich |
| Murtuza Jadliwala | University of Texas at San Antonio |
| Muslum Ozgur Ozmen | Arizona State University |
| Nils Lukas | University of Waterloo |
| Ning Zhang | Washington University in St. Louis |
| Nuno Santos | INESC-ID and Instituto Superior Técnico, University of Lisbon |
| Omar Chowdhury | Stony Brook University |
| Peng Gao | Virginia Tech |
| Pramod Bhatotia | TU Munich |
| Pratik Sarkar | Supra Research |
| Pratyush Mishra | University of Pennsylvania |
| Qi Li | Tsinghua University |
| Qiang Tang | The University of Sydney |
| Qiben Yan | Michigan State University |
| Qingkai Shi | Nanjing University |
| Quinn Burke | University of Wisconsin-Madison |
| Rahul Chatterjee | University of Wisconsin-Madison |
| Ram Sundara Raman | University of Michigan |
| Ramya Jayaram Masti | Ampere Computing |
| Rei Safavi-Naini | University of Calgary |
| Ryan Sheatsley | University of Wisconsin-Madison |
| Saba Eskandarian | University of North Carolina at Chapel Hill |
| Saman Zonouz | Georgia Tech |
| Samira Mirbagher Ajorpaz | North Carolina State University |
| Sathvik Prasad | North Carolina State University |
| Sazzadur Rahaman | University of Arizona |
| Sen Chen | Tianjin University |
| Seyedhamed Ghavamnia | University of Connecticut |
| Sherman S. M. Chow | The Chinese University of Hong Kong |
| Shih-Wei Li | National Taiwan University |
| Shitong Zhu | Meta Platforms Inc. |
| Shuai Wang | Hong Kong University of Science and Technology |
| Siqi Ma | The University of New South Wales |
| Sisi Duan | Tsinghua University |
| Soheil Khodayari | CISPA Helmholtz Center for Information Security |
| Song Li | Zhejiang University |
| Srdjan Capkun | ETH Zurich |
| Sri AravindaKrishnan Thyagarajan | University of Sydney |
| Stephen Herwig | William & Mary |
| Sunil Manandhar | IBM Research |
| Sven Bugiel | CISPA Helmholtz Center for Information Security |
| Swarn Priya | Virginia Tech |
| Syed Rafiul Hussain | Pennsylvania State University |
| Tapti Palit | University of California, Davis |
| Teodora Baluta | National University of Singapore |
| Tianhao Wang | University of Virginia |
| Tobias Fiebig | MPI-INF |
| Trent Jaeger | UC Riverside |
| Tushar Jois | City College of New York |
| VARUN CHANDRASEKARAN | University of Illinois Urbana-Champaign |
| Varun Madathil | Yale University |
| Wajih Ul Hassan | The University of Virginia |
| Weijia He | Dartmouth College |
| Wenjing Lou | Virginia Tech |
| Xiaojing Liao | Indiana University Bloomington |
| Xinda Wang | University of Texas at Dallas |
| Xingliang Yuan | The University of Melbourne |
| Xinyu Xing | Northwestern University |
| Xusheng Xiao | Arizona State University |
| Yan Chen | Northwestern University |
| Yan Shoshitaishvili | Arizona State University |
| Yanchao Zhang | Arizona State University |
| Yaxing Yao | Virginia Tech |
| Yigitcan Kaya | UC Santa Barbara |
| Yingying Chen | Rutgers University |
| Yinxi Liu | Rochester Institute of Technology |
| Yinzhi Cao | Johns Hopkins University |
| Yizheng Chen | University of Maryland |
| Yonghwi Kwon | University of Maryland |
| Yossi Oren | Ben-Gurion University, Israel |
| Yu Ding | Google DeepMind |
| Yuan Tian | UCLA |
| Yupeng Zhang | University of Illinois Urbana Champaign |
| Yuseok Jeon | Ulsan National Institute of Science and Technology (UNIST) |
| Yuval Yarom | Ruhr University Bochum |
| Yuzhe Tang | Syracuse University |
| Z. Berkay Celik | Purdue University |
| Zane Ma | Oregon State University |
| Zhiqiang Lin | Ohio State University |
| Zhiyun Qian | University of California, Riverside |
| Zhou Li | University of California, Irvine |
| Zhuotao Liu | Tsinghua University |
| Ziming Zhao | University at Buffalo |
| Ziqi Yang | Zhejiang University |
Share this page:
Artificial Intelligence in CyberSecurity
Submission Deadline: 30 July 2019
IEEE Access invites manuscript submissions in the area of Artificial Intelligence in CyberSecurity.
Recent studies show that Artificial Intelligence (AI) has resulted in advances in many scientific and technological fields, i.e., AI-based medicine, AI-based transportation, and AI-based finance. It can be imagined that the era of AI will be coming to us soon. The Internet has become the largest man-made system in human history, which has a great impact on people’s daily life and work. Security is one of the most significant concerns in the development of a sustainable, resilient and prosperous Internet ecosystem. Cyber security faces many challenging issues, such as intrusion detection, privacy protection, proactive defense, anomalous behaviors, advanced threat detection and so on. What’s more, many threat variations emerge and spread continuously. Therefore, AI-assisted, self-adaptable approaches are expected to deal with these security issues. Joint consideration of the interweaving nature between AI and cyber security is a key factor for driving future secure Internet.
The use of AI in cybersecurity creates new frontiers for security research. Specifically, the AI analytic tools, i.e., reinforcement learning, big data, machine learning and game theory, make learning increasingly important for real-time analysis and decision making for quick reactions to security attacks. On the other hand, AI technology itself also brings some security issues that need to be solved. For example, data mining and machine learning create a wealth of privacy issues due to the abundance and accessibility of data. AI-based cyber security has a great impact on different industrial applications if applied in appropriate ways, such as self-driving security, secure vehicular networks, industrial control security, smart grid security, etc. This Special Section in IEEE Access will focus on AI technologies in cybersecurity and related issues. We also welcome research on AI-related theory analysis for security and privacy.
The topics of interest include, but are not limited to:
- Reinforcement learning for cybersecurity
- Machine learning for proactive defense
- Big data analytics for security
- Big data anonymization
- Big data-based hacking incident forecasting
- Big data analytics for secure network management
- AI-based intrusion detection and prevention
- AI approaches to trust and reputation
- AI-based anomalous behavior detection
- AI-based privacy protection
- AI for self-driving security
- AI for IoT security
- AI for industrial control security
- AI for smart grid security
- AI for security in innovative networking
- AI security applications
We also highly recommend the submission of multimedia with each article as it significantly increases the visibility, downloads, and citations of articles.
Associate Editor: Chi-Yuan Chen, National Ilan University, Taiwan
Guest Editors:
- Wei Quan, Beijing Jiaotong University, China
- Nan Cheng, University of Toronto, Canada
- Shui Yu, Deakin University, Australia
- Jong-Hyouk Lee, Sangmyung University, Republic of Korea
- Gregorio Martinez Perez, University of Murcia (UMU), Spain
- Hongke Zhang, Beijing Jiaotong University, China
- Shiuhpyng Shieh, National Chiao Tung University, Taiwan
Relevant IEEE Access Special Sections:
- Artificial Intelligence and Cognitive Computing for Communications and Networks
- Smart Caching, Communications, Computing and Cybersecurity for Information-Centric Internet of Things
- Cyber-Physical Systems
IEEE Access Editor-in-Chief: Prof. Derek Abbott, University of Adelaide
Paper submission: Contact Associate Editor and submit manuscript to: http://ieee.atyponrex.com/journal/ieee-access
For inquiries regarding this Special Section, please contact: [email protected] .
At a Glance
- Journal: IEEE Access
- Format: Open Access
- Frequency: Continuous
- Submission to Publication: 4-6 weeks (typical)
- Topics: All topics in IEEE
- Average Acceptance Rate: 27%
- Impact Factor: 3.4
- Model: Binary Peer Review
- Article Processing Charge: US $1,995
Featured Articles
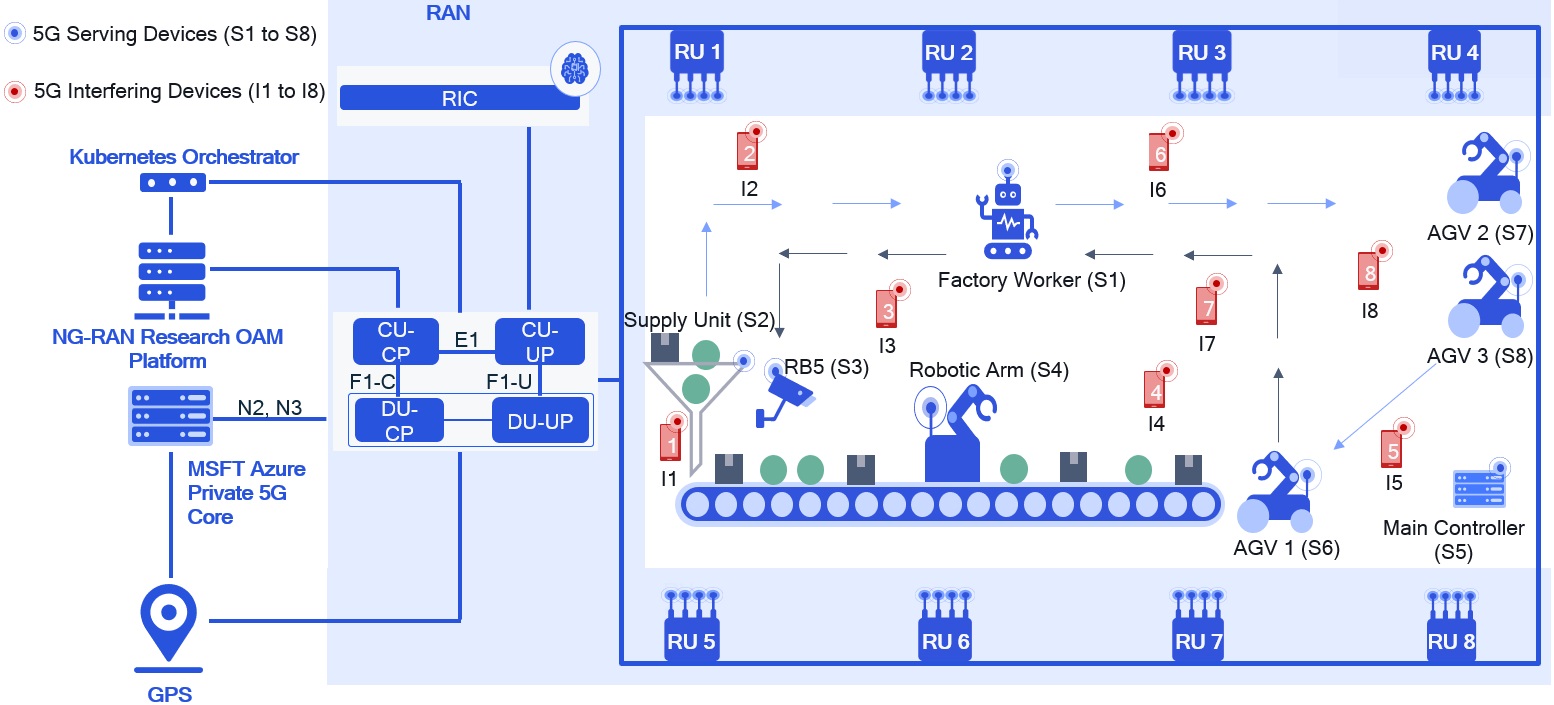
Interference-Aware Intelligent Scheduling for Virtualized Private 5G Networks
View in IEEE Xplore
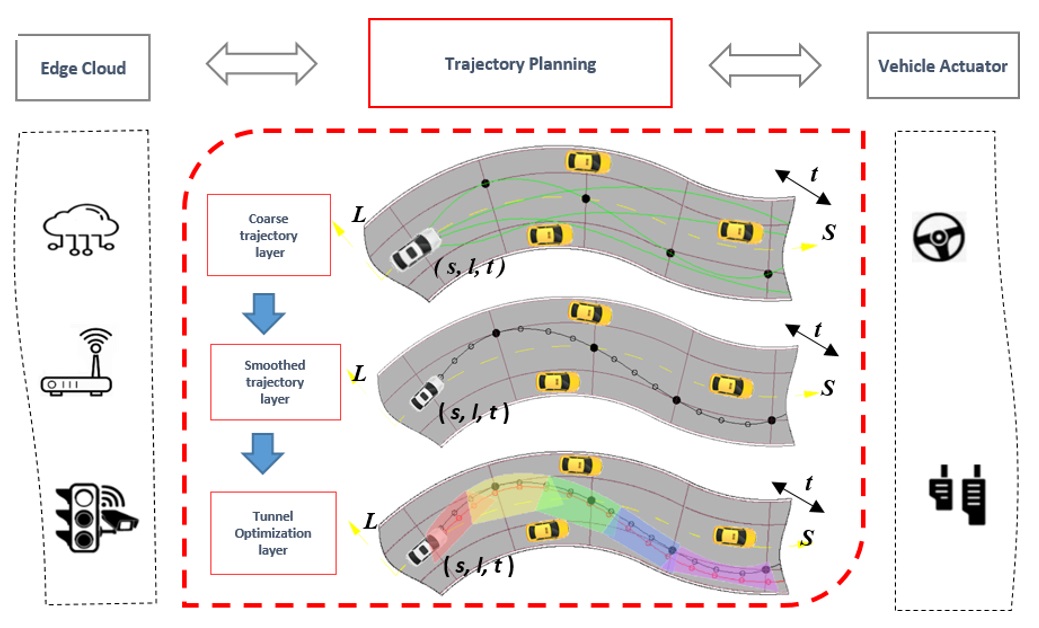
On-Road Trajectory Planning of Connected and Automated Vehicles in Complex Traffic Settings: A Hierarchical Framework of Trajectory Refinement
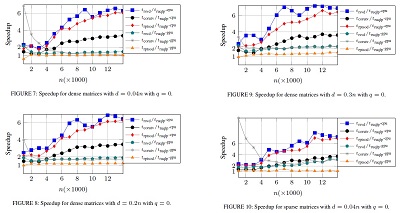
Randomized Rank-Revealing QLP for Low-Rank Matrix Decomposition
Submission guidelines.
© 2024 IEEE - All rights reserved. Use of this website signifies your agreement to the IEEE TERMS AND CONDITIONS.
A not-for-profit organization, IEEE is the world’s largest technical professional organization dedicated to advancing technology for the benefit of humanity.
AWARD RULES:
NO PURCHASE NECESSARY TO ENTER OR WIN. A PURCHASE WILL NOT INCREASE YOUR CHANCES OF WINNING.
These rules apply to the “2024 IEEE Access Best Video Award Part 2″ (the “Award”).
- Sponsor: The Sponsor of the Award is The Institute of Electrical and Electronics Engineers, Incorporated (“IEEE”) on behalf of IEEE Access , 445 Hoes Lane, Piscataway, NJ 08854-4141 USA (“Sponsor”).
- Eligibility: Award is open to residents of the United States of America and other countries, where permitted by local law, who are the age of eighteen (18) and older. Employees of Sponsor, its agents, affiliates and their immediate families are not eligible to enter Award. The Award is subject to all applicable state, local, federal and national laws and regulations. Entrants may be subject to rules imposed by their institution or employer relative to their participation in Awards and should check with their institution or employer for any relevant policies. Void in locations and countries where prohibited by law.
- Agreement to Official Rules : By participating in this Award, entrants agree to abide by the terms and conditions thereof as established by Sponsor. Sponsor reserves the right to alter any of these Official Rules at any time and for any reason. All decisions made by Sponsor concerning the Award including, but not limited to the cancellation of the Award, shall be final and at its sole discretion.
- How to Enter: This Award opens on July 1, 2024 at 12:00 AM ET and all entries must be received by 11:59 PM ET on December 31, 2024 (“Promotional Period”).
Entrant must submit a video with an article submission to IEEE Access . The video submission must clearly be relevant to the submitted manuscript. Only videos that accompany an article that is accepted for publication in IEEE Access will qualify. The video may be simulations, demonstrations, or interviews with other experts, for example. Your video file should not exceed 100 MB.
Entrants can enter the Award during Promotional Period through the following method:
- The IEEE Author Portal : Entrants can upload their video entries while submitting their article through the IEEE Author Portal submission site .
- Review and Complete the Terms and Conditions: After submitting your manuscript and video through the IEEE Author Portal, entrants should then review and sign the Terms and Conditions .
Entrants who have already submitted a manuscript to IEEE Access without a video can still submit a video for inclusion in this Award so long as the video is submitted within 7 days of the article submission date. The video can be submitted via email to the article administrator. All videos must undergo peer review and be accepted along with the article submission. Videos may not be submitted after an article has already been accepted for publication.
The criteria for an article to be accepted for publication in IEEE Access are:
- The article must be original writing that enhances the existing body of knowledge in the given subject area. Original review articles and surveys are acceptable even if new data/concepts are not presented.
- Results reported must not have been submitted or published elsewhere (although expanded versions of conference publications are eligible for submission).
- Experiments, statistics, and other analyses must be performed to a high technical standard and are described in sufficient detail.
- Conclusions must be presented in an appropriate fashion and are supported by the data.
- The article must be written in standard English with correct grammar.
- Appropriate references to related prior published works must be included.
- The article must fall within the scope of IEEE Access
- Must be in compliance with the IEEE PSPB Operations Manual.
- Completion of the required IEEE intellectual property documents for publication.
- At the discretion of the IEEE Access Editor-in-Chief.
- Disqualification: The following items will disqualify a video from being considered a valid submission:
- The video is not original work.
- A video that is not accompanied with an article submission.
- The article and/or video is rejected during the peer review process.
- The article and/or video topic does not fit into the scope of IEEE Access .
- The article and/or do not follow the criteria for publication in IEEE Access .
- Videos posted in a comment on IEEE Xplore .
- Content is off-topic, offensive, obscene, indecent, abusive or threatening to others.
- Infringes the copyright, trademark or other right of any third party.
- Uploads viruses or other contaminating or destructive features.
- Is in violation of any applicable laws or regulations.
- Is not in English.
- Is not provided within the designated submission time.
- Entrant does not agree and sign the Terms and Conditions document.
Entries must be original. Entries that copy other entries, or the intellectual property of anyone other than the Entrant, may be removed by Sponsor and the Entrant may be disqualified. Sponsor reserves the right to remove any entry and disqualify any Entrant if the entry is deemed, in Sponsor’s sole discretion, to be inappropriate.
- Entrant’s Warranty and Authorization to Sponsor: By entering the Award, entrants warrant and represent that the Award Entry has been created and submitted by the Entrant. Entrant certifies that they have the ability to use any image, text, video, or other intellectual property they may upload and that Entrant has obtained all necessary permissions. IEEE shall not indemnify Entrant for any infringement, violation of publicity rights, or other civil or criminal violations. Entrant agrees to hold IEEE harmless for all actions related to the submission of an Entry. Entrants further represent and warrant, if they reside outside of the United States of America, that their participation in this Award and acceptance of a prize will not violate their local laws.
- Intellectual Property Rights: Entrant grants Sponsor an irrevocable, worldwide, royalty free license to use, reproduce, distribute, and display the Entry for any lawful purpose in all media whether now known or hereinafter created. This may include, but is not limited to, the IEEE A ccess website, the IEEE Access YouTube channel, the IEEE Access IEEE TV channel, IEEE Access social media sites (LinkedIn, Facebook, Twitter, IEEE Access Collabratec Community), and the IEEE Access Xplore page. Facebook/Twitter/Microsite usernames will not be used in any promotional and advertising materials without the Entrants’ expressed approval.
- Number of Prizes Available, Prizes, Approximate Retail Value and Odds of winning Prizes: Two (2) promotional prizes of $350 USD Amazon gift cards. One (1) grand prize of a $500 USD Amazon gift card. Prizes will be distributed to the winners after the selection of winners is announced. Odds of winning a prize depend on the number of eligible entries received during the Promotional Period. Only the corresponding author of the submitted manuscript will receive the prize.
The grand prize winner may, at Sponsor’ discretion, have his/her article and video highlighted in media such as the IEEE Access Xplore page and the IEEE Access social media sites.
The prize(s) for the Award are being sponsored by IEEE. No cash in lieu of prize or substitution of prize permitted, except that Sponsor reserves the right to substitute a prize or prize component of equal or greater value in its sole discretion for any reason at time of award. Sponsor shall not be responsible for service obligations or warranty (if any) in relation to the prize(s). Prize may not be transferred prior to award. All other expenses associated with use of the prize, including, but not limited to local, state, or federal taxes on the Prize, are the sole responsibility of the winner. Winner(s) understand that delivery of a prize may be void where prohibited by law and agrees that Sponsor shall have no obligation to substitute an alternate prize when so prohibited. Amazon is not a sponsor or affiliated with this Award.
- Selection of Winners: Promotional prize winners will be selected based on entries received during the Promotional Period. The sponsor will utilize an Editorial Panel to vote on the best video submissions. Editorial Panel members are not eligible to participate in the Award. Entries will be ranked based on three (3) criteria:
- Presentation of Technical Content
- Quality of Video
Upon selecting a winner, the Sponsor will notify the winner via email. All potential winners will be notified via their email provided to the sponsor. Potential winners will have five (5) business days to respond after receiving initial prize notification or the prize may be forfeited and awarded to an alternate winner. Potential winners may be required to sign an affidavit of eligibility, a liability release, and a publicity release. If requested, these documents must be completed, signed, and returned within ten (10) business days from the date of issuance or the prize will be forfeited and may be awarded to an alternate winner. If prize or prize notification is returned as undeliverable or in the event of noncompliance with these Official Rules, prize will be forfeited and may be awarded to an alternate winner.
- General Prize Restrictions: No prize substitutions or transfer of prize permitted, except by the Sponsor. Import/Export taxes, VAT and country taxes on prizes are the sole responsibility of winners. Acceptance of a prize constitutes permission for the Sponsor and its designees to use winner’s name and likeness for advertising, promotional and other purposes in any and all media now and hereafter known without additional compensation unless prohibited by law. Winner acknowledges that neither Sponsor, Award Entities nor their directors, employees, or agents, have made nor are in any manner responsible or liable for any warranty, representation, or guarantee, express or implied, in fact or in law, relative to any prize, including but not limited to its quality, mechanical condition or fitness for a particular purpose. Any and all warranties and/or guarantees on a prize (if any) are subject to the respective manufacturers’ terms therefor, and winners agree to look solely to such manufacturers for any such warranty and/or guarantee.
11.Release, Publicity, and Privacy : By receipt of the Prize and/or, if requested, by signing an affidavit of eligibility and liability/publicity release, the Prize Winner consents to the use of his or her name, likeness, business name and address by Sponsor for advertising and promotional purposes, including but not limited to on Sponsor’s social media pages, without any additional compensation, except where prohibited. No entries will be returned. All entries become the property of Sponsor. The Prize Winner agrees to release and hold harmless Sponsor and its officers, directors, employees, affiliated companies, agents, successors and assigns from and against any claim or cause of action arising out of participation in the Award.
Sponsor assumes no responsibility for computer system, hardware, software or program malfunctions or other errors, failures, delayed computer transactions or network connections that are human or technical in nature, or for damaged, lost, late, illegible or misdirected entries; technical, hardware, software, electronic or telephone failures of any kind; lost or unavailable network connections; fraudulent, incomplete, garbled or delayed computer transmissions whether caused by Sponsor, the users, or by any of the equipment or programming associated with or utilized in this Award; or by any technical or human error that may occur in the processing of submissions or downloading, that may limit, delay or prevent an entrant’s ability to participate in the Award.
Sponsor reserves the right, in its sole discretion, to cancel or suspend this Award and award a prize from entries received up to the time of termination or suspension should virus, bugs or other causes beyond Sponsor’s control, unauthorized human intervention, malfunction, computer problems, phone line or network hardware or software malfunction, which, in the sole opinion of Sponsor, corrupt, compromise or materially affect the administration, fairness, security or proper play of the Award or proper submission of entries. Sponsor is not liable for any loss, injury or damage caused, whether directly or indirectly, in whole or in part, from downloading data or otherwise participating in this Award.
Representations and Warranties Regarding Entries: By submitting an Entry, you represent and warrant that your Entry does not and shall not comprise, contain, or describe, as determined in Sponsor’s sole discretion: (A) false statements or any misrepresentations of your affiliation with a person or entity; (B) personally identifying information about you or any other person; (C) statements or other content that is false, deceptive, misleading, scandalous, indecent, obscene, unlawful, defamatory, libelous, fraudulent, tortious, threatening, harassing, hateful, degrading, intimidating, or racially or ethnically offensive; (D) conduct that could be considered a criminal offense, could give rise to criminal or civil liability, or could violate any law; (E) any advertising, promotion or other solicitation, or any third party brand name or trademark; or (F) any virus, worm, Trojan horse, or other harmful code or component. By submitting an Entry, you represent and warrant that you own the full rights to the Entry and have obtained any and all necessary consents, permissions, approvals and licenses to submit the Entry and comply with all of these Official Rules, and that the submitted Entry is your sole original work, has not been previously published, released or distributed, and does not infringe any third-party rights or violate any laws or regulations.
12.Disputes: EACH ENTRANT AGREES THAT: (1) ANY AND ALL DISPUTES, CLAIMS, AND CAUSES OF ACTION ARISING OUT OF OR IN CONNECTION WITH THIS AWARD, OR ANY PRIZES AWARDED, SHALL BE RESOLVED INDIVIDUALLY, WITHOUT RESORTING TO ANY FORM OF CLASS ACTION, PURSUANT TO ARBITRATION CONDUCTED UNDER THE COMMERCIAL ARBITRATION RULES OF THE AMERICAN ARBITRATION ASSOCIATION THEN IN EFFECT, (2) ANY AND ALL CLAIMS, JUDGMENTS AND AWARDS SHALL BE LIMITED TO ACTUAL OUT-OF-POCKET COSTS INCURRED, INCLUDING COSTS ASSOCIATED WITH ENTERING THIS AWARD, BUT IN NO EVENT ATTORNEYS’ FEES; AND (3) UNDER NO CIRCUMSTANCES WILL ANY ENTRANT BE PERMITTED TO OBTAIN AWARDS FOR, AND ENTRANT HEREBY WAIVES ALL RIGHTS TO CLAIM, PUNITIVE, INCIDENTAL, AND CONSEQUENTIAL DAMAGES, AND ANY OTHER DAMAGES, OTHER THAN FOR ACTUAL OUT-OF-POCKET EXPENSES, AND ANY AND ALL RIGHTS TO HAVE DAMAGES MULTIPLIED OR OTHERWISE INCREASED. ALL ISSUES AND QUESTIONS CONCERNING THE CONSTRUCTION, VALIDITY, INTERPRETATION AND ENFORCEABILITY OF THESE OFFICIAL RULES, OR THE RIGHTS AND OBLIGATIONS OF ENTRANT AND SPONSOR IN CONNECTION WITH THE AWARD, SHALL BE GOVERNED BY, AND CONSTRUED IN ACCORDANCE WITH, THE LAWS OF THE STATE OF NEW JERSEY, WITHOUT GIVING EFFECT TO ANY CHOICE OF LAW OR CONFLICT OF LAW, RULES OR PROVISIONS (WHETHER OF THE STATE OF NEW JERSEY OR ANY OTHER JURISDICTION) THAT WOULD CAUSE THE APPLICATION OF THE LAWS OF ANY JURISDICTION OTHER THAN THE STATE OF NEW JERSEY. SPONSOR IS NOT RESPONSIBLE FOR ANY TYPOGRAPHICAL OR OTHER ERROR IN THE PRINTING OF THE OFFER OR ADMINISTRATION OF THE AWARD OR IN THE ANNOUNCEMENT OF THE PRIZES.
- Limitation of Liability: The Sponsor, Award Entities and their respective parents, affiliates, divisions, licensees, subsidiaries, and advertising and promotion agencies, and each of the foregoing entities’ respective employees, officers, directors, shareholders and agents (the “Released Parties”) are not responsible for incorrect or inaccurate transfer of entry information, human error, technical malfunction, lost/delayed data transmissions, omission, interruption, deletion, defect, line failures of any telephone network, computer equipment, software or any combination thereof, inability to access web sites, damage to a user’s computer system (hardware and/or software) due to participation in this Award or any other problem or error that may occur. By entering, participants agree to release and hold harmless the Released Parties from and against any and all claims, actions and/or liability for injuries, loss or damage of any kind arising from or in connection with participation in and/or liability for injuries, loss or damage of any kind, to person or property, arising from or in connection with participation in and/or entry into this Award, participation is any Award-related activity or use of any prize won. Entry materials that have been tampered with or altered are void. If for any reason this Award is not capable of running as planned, or if this Award or any website associated therewith (or any portion thereof) becomes corrupted or does not allow the proper playing of this Award and processing of entries per these rules, or if infection by computer virus, bugs, tampering, unauthorized intervention, affect the administration, security, fairness, integrity, or proper conduct of this Award, Sponsor reserves the right, at its sole discretion, to disqualify any individual implicated in such action, and/or to cancel, terminate, modify or suspend this Award or any portion thereof, or to amend these rules without notice. In the event of a dispute as to who submitted an online entry, the entry will be deemed submitted by the authorized account holder the email address submitted at the time of entry. “Authorized Account Holder” is defined as the person assigned to an email address by an Internet access provider, online service provider or other organization responsible for assigning email addresses for the domain associated with the email address in question. Any attempt by an entrant or any other individual to deliberately damage any web site or undermine the legitimate operation of the Award is a violation of criminal and civil laws and should such an attempt be made, the Sponsor reserves the right to seek damages and other remedies from any such person to the fullest extent permitted by law. This Award is governed by the laws of the State of New Jersey and all entrants hereby submit to the exclusive jurisdiction of federal or state courts located in the State of New Jersey for the resolution of all claims and disputes. Facebook, LinkedIn, Twitter, G+, YouTube, IEEE Xplore , and IEEE TV are not sponsors nor affiliated with this Award.
- Award Results and Official Rules: To obtain the identity of the prize winner and/or a copy of these Official Rules, send a self-addressed stamped envelope to Kimberly Rybczynski, IEEE, 445 Hoes Lane, Piscataway, NJ 08854-4141 USA.
Information Security
Featured article, related topics, top conferences on information security, top videos on information security.

Xplore Articles related to Information Security
Periodicals related to information security, e-books related to information security, courses related to information security, standards related to information security, top organizations on information security, most published xplore authors for information security.
- Home
- Program (Compact)
- Accepted Papers
- Short Talks
- Symposium Presenter Information
- Virtual Socials
- Registration
- Student Travel Grants
- Attendee Code of Conduct
- General Info
- Past Conferences
- Conference Organizers
- Technical Committee
MAY 24-27, 2021
42nd IEEE Symposium on Security and Privacy
Sponsored by the IEEE Computer Society Technical Committee on Security and Privacy in cooperation with the International Association for Cryptologic Research
Registration and Access
Conference Paper Abstracts due Friday November 4!
Only papers with an abstract submitted by the deadline will be reviewed.
Call For Papers
Since 1980 in Oakland, the IEEE Symposium on Security and Privacy has been the premier forum for computer security research, presenting the latest developments and bringing together researchers and practitioners. We solicit previously unpublished papers offering novel research contributions in any aspect of security or privacy. Papers may present advances in the theory, design, implementation, analysis, verification, or empirical evaluation and measurement of secure systems.
Topics of interest include:
- Access control and authorization
- Application security
- Attacks and defenses
- Authentication
- Blockchains and distributed ledger security
- Censorship resistance
- Cloud security
- Cyber physical systems security
- Distributed systems security
- Economics of security and privacy
- Embedded systems security
- Hardware security
- Intrusion detection and prevention
- Malware and unwanted software
- Mobile and Web security and privacy
- Language-based security
- Machine learning and AI security
- Network and systems security
- Privacy technologies and mechanisms
- Protocol security
- Secure information flow
- Security and privacy for the Internet of Things
- Security and privacy metrics
- Security and privacy policies
- Security architectures
- Usable security and privacy
- Trustworthy computing
- Web security
This topic list is not meant to be exhaustive; S&P is interested in all aspects of computer security and privacy. Papers without a clear application to security or privacy, however, will be considered out of scope and may be rejected without full review.
Systematization of Knowledge Papers
As in past years, we solicit systematization of knowledge (SoK) papers that evaluate, systematize, and contextualize existing knowledge, as such papers can provide a high value to our community. Suitable papers are those that provide an important new viewpoint on an established, major research area, support or challenge long-held beliefs in such an area with compelling evidence, or present a convincing, comprehensive new taxonomy of such an area. Survey papers without such insights are not appropriate and may be rejected without full review. Submissions will be distinguished by the prefix “SoK:” in the title and a checkbox on the submission form. They will be reviewed by the full PC and held to the same standards as traditional research papers, but they will be accepted based on their treatment of existing work and value to the community, and not based on any new research results they may contain. Accepted papers will be presented at the symposium and included in the proceedings.
Quarterly Submissions
Based on the experience in the past two years, the reviewing process for IEEE S&P is changed to a quarterly submission model. Within 2.5 months of submission, author notifications of Accept/Revise/Reject decisions will be sent out. For each submission, one of the following decisions will be made:
Accept : Papers in this category will be accepted for publication in the proceedings and presentation at the conference, possibly after making minor changes with the oversight of a shepherd. Within one month of acceptance, all accepted papers must submit a camera-ready copy incorporating reviewer feedback. The papers will immediately be published, open access, in the Computer Society’s Digital Library, and they may be cited as “To appear in the IEEE Symposium on Security & Privacy, May 2021”.
Revise : A limited number of papers will be invited to submit a revision; such papers will receive a specific set of expectations to be met by that revision. Authors can submit a revised paper to the next two quarterly submission deadlines after the notification. The authors should clearly explain in a well-marked appendix how the revisions address the comments of the reviewers. The revised paper will then be re-evaluated, and either accepted or rejected.
Reject : Papers in this category are declined for inclusion in the conference. Rejected papers must wait for one year, from the date of original submission, to resubmit to IEEE S&P. A paper will be judged to be a resubmit (as opposed to a new submission) if the paper is from the same or similar authors, and a reviewer could write a substantially similar summary of the paper compared with the original submission. As a rule of thumb, if there is more than 40% overlap between the original submission and the new paper, it will be considered a resubmission.
All papers accepted by February 21, 2021 will appear in the proceedings of the symposium in May 2021 and invited to present their work. These include papers that were submitted in December 2020 and were accepted without revision, or papers that were submitted by June 2020, got the Revise decision, and resubmitted the revised paper in December.
Important Dates
All deadlines are 23:59:59 AoE (UTC-12).
Spring Quarter Deadline
- Paper submission deadline: March 5, 2020
- Early-reject notification: April 17, 2020 April 21, 2020
- Acceptance notification: May 22, 2020
- Camera-ready deadline: July 1, 2020
Summer Quarter Deadline
- Paper submission deadline: June 4, 2020
- Early-reject notification: July 17, 2020
- Acceptance notification: August 21, 2020
- Camera-ready deadline: September 30, 2020
Fall Quarter Deadline
- Paper submission deadline: September 3, 2020
- Early-reject notification: October 16, 2020
- Acceptance notification: November 20, 2020
- Camera-ready deadline: December 29, 2020
Winter Quarter Deadline
- Paper submission deadline: December 3, 2020
- Early-reject notification: January 15, 2021
- Acceptance notification: February 19, 2021
- Camera-ready deadline: March 28, 2021
Revised Submissions
As described above, some number of papers will receive a Revise decision, rather than Accept or Reject. This decision will be accompanied by a detailed summary of the expectations for the revision, in addition to the standard reviewer comments. The authors may prepare a revision, which may include running additional experiments, improving the paper’s presentation, or other such improvements. Papers meeting the expectations will typically be accepted. Those that do not will be rejected. Only in exceptional circumstances will additional revisions be requested. Upon receiving a Revise decision, authors can choose to withdraw their paper or not submit a revision, but they will be asked to not submit the same or similar work again (following the same rules as for Rejected papers) for one year from the date of the original submission. Authors can submit a revised paper to the next two quarterly submission deadlines after the notification. Revisions must be accompanied by a summary of the changes that were made.
Submission Statistics
After finishing the first three cycles, a total of 77 papers were accepted (including revised papers from the previous year). In total, 643 papers were submitted, resulting in an acceptance rate of 12.0%.
Instructions for Paper Submission
These instructions apply to both the research papers and systematization of knowledge papers. All submissions must be original work; the submitter must clearly document any overlap with previously published or simultaneously submitted papers from any of the authors. Failure to point out and explain overlap will be grounds for rejection. Simultaneous submission of the same paper to another venue with proceedings or a journal is not allowed and will be grounds for automatic rejection. Contact the program committee chairs if there are questions about this policy.
Anonymous Submission
Papers must be submitted in a form suitable for anonymous review: no author names or affiliations may appear on the title page, and papers should avoid revealing authors’ identity in the text. When referring to their previous work, authors are required to cite their papers in third person, without identifying themselves. In the unusual case in which a third-person reference is infeasible, authors can blind the reference itself. Papers that are not properly anonymized may be rejected without review.
While a paper is under submission to the IEEE Security & Privacy Symposium, authors may choose to give talks about their work, post a preprint of the paper online, and disclose security vulnerabilities to vendors. Authors should refrain from widely advertising their results, but in special circumstances they should contact the PC chairs to discuss exceptions. Authors are not allowed to contact directly the program committee members to discuss their submission.
The submissions will be treated confidentially by the PC chairs and the program committee members. Program committee members are not allowed to share the submitted papers with anyone, with the exception of qualified external reviewers approved by the program committee chairs. Please contact the PC chairs if you have any questions or concerns.
Conflicts of Interest
Drawn from the acm sigmod 2015 cfp.
During submission of a research paper, the submission site will request information about conflicts of interest of the paper's authors with program committee (PC) members. It is the full responsibility of all authors of a paper to identify all and only their potential conflict-of-interest PC members, according to the following definition. A paper author has a conflict of interest with a PC member when and only when one or more of the following conditions holds:
- The PC member is a co-author of the paper.
- For student interns, the student is conflicted with their supervisors and with members of the same research group. If the student no longer works for the organization, then they are not conflicted with a PC member from the larger organization.
- The PC member has been a collaborator within the past two years.
- The PC member is or was the author's primary thesis advisor, no matter how long ago.
- The author is or was the PC member's primary thesis advisor, no matter how long ago.
- The PC member is a relative or close personal friend of the author.
For any other situation where the authors feel they have a conflict with a PC member, they must explain the nature of the conflict to the PC chairs, who will mark the conflict if appropriate. Papers with incorrect or incomplete conflict of interest information as of the submission closing time are subject to immediate rejection.
Financial and Non-financial competing interests NEW
In the interests of transparency and to help readers form their own judgements of potential bias, the IEEE Symposium on Security & Privacy requires authors and PC members to declare any competing financial and/or non-financial interests in relation to the work described. Authors need to include a disclosure of relevant financial interests in the camera-ready versions of their papers. This includes not just the standard funding lines, but should also include disclosures of any financial interest related to the research described. For example, "Author X is on the Technical Advisory Board of the ByteCoin Foundation," or "Professor Y is the CTO of DoubleDefense, which specializes in malware analysis." More information regarding this policy is available here .
Ethical Considerations for Vulnerability Disclosure
Where research identifies a vulnerability (e.g., software vulnerabilities in a given program, design weaknesses in a hardware system, or any other kind of vulnerability in deployed systems), we expect that researchers act in a way that avoids gratuitous harm to affected users and, where possible, affirmatively protects those users. In nearly every case, disclosing the vulnerability to vendors of affected systems, and other stakeholders, will help protect users. It is the committee’s sense that a disclosure window of 45 days https://vuls.cert.org/confluence/display/Wiki/Vulnerability+Disclosure+Policy to 90 days https://googleprojectzero.blogspot.com/p/vulnerability-disclosure-faq.html ahead of publication is consistent with authors’ ethical obligations.
The version of the paper submitted for review must discuss in detail the steps the authors have taken or plan to take to address these vulnerabilities; but, consistent with the timelines above, the authors do not have to disclose vulnerabilities ahead of submission. If a paper raises significant ethical and/or legal concerns, it might be rejected based on these concerns. The PC chairs will be happy to consult with authors about how this policy applies to their submissions.
Ethical Considerations for Human Subjects Research
Submissions that describe experiments on human subjects, that analyze data derived from human subjects (even anonymized data), or that otherwise may put humans at risk should:
- Disclose whether the research received an approval or waiver from each of the authors' institutional ethics review boards (IRB) if applicable.
- Discuss steps taken to ensure that participants and others who might have been affected by an experiment were treated ethically and with respect.
If a submission deals with any kind of personal identifiable information (PII) or other kinds of sensitive data, the version of the paper submitted for review must discuss in detail the steps the authors have taken to mitigate harms to the persons identified. If a paper raises significant ethical and/or legal concerns, it might be rejected based on these concerns. The PC chairs will be happy to consult with authors about how this policy applies to their submissions.
Page Limit and Formatting
Submitted papers may include up to 13 pages of text and up to 5 pages for references and appendices, totaling no more than 18 pages. The same applies to camera-ready papers, although, at the PC chairs’ discretion, additional pages may be allowed for references and appendices. Reviewers are not required to read appendices.
Papers must be formatted for US letter (not A4) size paper. The text must be formatted in a two-column layout, with columns no more than 9.5 in. tall and 3.5 in. wide. The text must be in Times font, 10-point or larger, with 11-point or larger line spacing. Authors are encouraged to use the IEEE conference proceedings templates. LaTeX submissions should use IEEEtran.cls version 1.8b. All submissions will be automatically checked for conformance to these requirements. Failure to adhere to the page limit and formatting requirements are grounds for rejection without review.
Reviews from Prior Submissions
Drawn from the acm ccs 2020 cfp, new this year.
For papers that were previously submitted to, and rejected from, another conference, authors are required to submit a separate document containing the prior reviews along with a description of how those reviews were addressed in the current version of the paper. Authors are only required to include reviews from the last time the paper was submitted. Reviewers will be asked to complete their reviews before reading the provided supplementary material to avoid being biased in formulating their own opinions; once their reviews are complete, however, reviewers will be given the opportunity to provide additional comments based on the submission history of the paper. Authors who try to circumvent this rule (e.g., by changing the title of the paper without significantly changing the contents) may have their papers rejected without further consideration, at the discretion of the PC chairs.
Authors need to make sure that the prior reviews do not reveal the identity of the authors, the authors need to carefully remove all information that might violate the anonymous submission requirements.
Submissions must be in Portable Document Format (.pdf). Authors should pay special attention to unusual fonts, images, and figures that might create problems for reviewers.
Conference Submission Server
- Papers for the spring quarter cycle must be submitted at: https://oakland21-spring.syssec.rub.de/hotcrp/
- Papers for the summer quarter cycle must be submitted at: https://oakland21-summer.syssec.rub.de/hotcrp/
- Papers for the fall quarter cycle must be submitted at: https://oakland21-fall.syssec.rub.de/hotcrp/
- Papers for the winter quarter cycle must be submitted at: https://oakland21-winter.syssec.rub.de/hotcrp/
Publication and Presentation
Authors are responsible for obtaining appropriate publication clearances. One of the authors of the accepted paper is expected to present the paper at the conference.
Program Committee
| Alina Oprea | Northeastern University |
| Thorsten Holz | Ruhr-Universität Bochum |
| Adam Aviv | The George Washington University |
| Davide Balzarotti | Eurecom |
| Gilles Barthe | MPI-SP and IMDEA Software Institute |
| Lujo Bauer | Carnegie Mellon University |
| Karthikeyan Bhargavan | Inria |
| Antonio Bianchi | Purdue University |
| Nataliia Bielova | Inria |
| Battista Biggio | University of Cagliari |
| Eric Bodden | Paderborn University and Fraunhofer IEM |
| Joseph Bonneau | New York University |
| Kevin Borgolte | Princeton University |
| Ioana Boureanu | University of Surrey |
| Billy Brumley | Tampere University |
| Chris Brzuska | Aalto University |
| Kevin Butler | University of Florida |
| Brent Byunghoon Kang | KAIST |
| Srdjan Capkun | ETH Zurich |
| Nicholas Carlini | |
| David Cash | University of Chicago |
| Lorenzo Cavallaro | King's College London |
| Melissa Chase | Microsoft Research Redmond |
| Rahul Chatterjee | University of Wisconsin-Madison |
| Nicolas Christin | Carnegie Mellon University |
| Henry Corrigan-Gibbs | EPFL and MIT CSAIL |
| Manuel Costa | Microsoft Research |
| Cas Cremers | CISPA Helmholtz Center for Information Security |
| Weidong Cui | Microsoft Research |
| Rachel Cummings | Georgia Institute of Technology |
| Anupam Das | North Carolina State University |
| Nathan Dautenhahn | Rice University |
| Emiliano De Cristofaro | University College London |
| Brendan Dolan-Gavitt | New York University |
| Adam Doupé | Arizona State University |
| Markus Dürmuth | Ruhr-Universität Bochum |
| Giulia Fanti | Carnegie Mellon University |
| Sebastian Faust | TU Darmstadt |
| Kassem Fawaz | University of Wisconsin-Madison |
| Tobias Fiebig | TU Delft |
| Anders Fogh | Intel Corporation |
| Cedric Fournet | Microsoft Research |
| Michael Franz | University of California Irvine |
| Matt Fredrikson | Carnegie Mellon University |
| Adria Gascon | Google Research |
| Arthur Gervais | Imperial College London |
| Neil Gong | Duke University |
| Guofei Gu | Texas A&M University |
| Andreas Haeberlen | University of Pennsylvania |
| Matthew Hicks | Virginia Tech |
| Thorsten Holz chair | Ruhr-Universität Bochum |
| Amir Houmansadr | UMass Amherst |
| Catalin Hritcu | Max Planck Institute for Security and Privacy (MPI-SP) |
| Luca Invernizzi | |
| Tibor Jager | Bergische Universität Wuppertal |
| Suman Jana | Columbia University |
| Limin Jia | Carnegie Mellon University |
| Aniket Kate | Purdue University |
| Stefan Katzenbeisser | University of Passau |
| Yongdae Kim | Korea Advanced Institute of Science and Technology (KAIST) |
| David Kohlbrenner | UC Berkeley |
| Katharina Krombholz | CISPA Helmholtz Center for Information Security |
| Ralf Kuesters | University of Stuttgart |
| Boris Köpf | Microsoft Research |
| Tancrède Lepoint | |
| Qi Li | Tsinghua University |
| Frank Li | Georgia Institute of Technology |
| Xiaojing Liao | Indiana University Bloomington |
| David Lie | University of Toronto |
| Zhiqiang Lin | The Ohio State University |
| Martina Lindorfer | TU Wien |
| Matteo Maffei | TU Wien |
| Sergio Maffeis | Imperial College London |
| Clémentine Maurice | CNRS, IRISA |
| Michelle Mazurek | University of Maryland |
| Damon McCoy | New York University |
| Andrew Miller | University of Illinois at Urbana-Champaign |
| Nick Nikiforakis | Stony Brook University |
| Guevara Noubir | Northeastern University |
| Olga Ohrimenko | The University of Melbourne |
| Alina Oprea chair | Northeastern University |
| Yossi Oren | Ben-Gurion University |
| Nicolas Papernot | University of Toronto and Vector Institute |
| Mathias Payer | EPFL |
| Paul Pearce | Georgia Tech and ICSI |
| Marcus Peinado | Microsoft Research |
| Giancarlo Pellegrino | CISPA Helmholtz Center for Information Security |
| Roberto Perdisci | University of Georgia |
| Frank Piessens | KU Leuven |
| Benny Pinkas | VMware Research / Bar Ilan University |
| Jason Polakis | University of Illinois at Chicago |
| Michalis Polychronakis | Stony Brook University |
| Christina Pöpper | New York University Abu Dhabi |
| Zhiyun Qian | University of California Riverside |
| Ananth Raghunathan | |
| Aanjhan Ranganathan | Northeastern University |
| Kasper Rasmussen | University of Oxford |
| Mariana Raykova | |
| Konrad Rieck | TU Braunschweig |
| William Robertson | Northeastern University |
| Christian Rossow | CISPA Helmholtz Center for Information Security |
| Andrei Sabelfeld | Chalmers University of Technology |
| Brendan Saltaformaggio | Georgia Institute of Technology |
| Dominique Schröder | Friedrich-Alexander-Universität Erlangen-Nürnberg |
| Jörg Schwenk | Ruhr-Universität Bochum |
| Vyas Sekar | Carnegie Mellon University |
| Simha Sethumadhavan | Columbia University/Chip Scan |
| Srinath Setty | Microsoft Research |
| Hovav Shacham | The University of Texas at Austin |
| Emily Shen | MIT Lincoln Laboratory |
| Elaine Shi | Cornell |
| Reza Shokri | National University of Singapore (NUS) |
| Yan Shoshitaishvili | Arizona State University |
| Emily Stark | |
| Deian Stefan | UC San Diego |
| Ben Stock | CISPA Helmholtz Center for Information Security |
| Thorsten Strufe | Karlsruhe Institute of Technology (KIT) and CeTI/TU-Dresden |
| Gang Tan | Penn State University |
| Vanessa Teague | Thinking Cybersecurity and The Australian National University |
| Kurt Thomas | |
| Yuan Tian | University of Virginia |
| Carmela Troncoso | EPFL |
| Jonathan Ullman | Northeastern University |
| Selcuk Uluagac | Florida International University |
| Blase Ur | University of Chicago |
| Xiao Wang | Northwestern University |
| Yuval Yarom | University of Adelaide and Data61 |
| Yanfang (Fanny) Ye | Case Western Reserve University |
| Ting-Fang Yen | DataVisor |
| Heng Yin | UC Riverside |
| Fengwei Zhang | Southern University of Science and Technology (SUSTech) |
| Ben Zhao | University of Chicago |
| Yajin Zhou | Zhejiang University |
| Thyla van der Merwe | Mozilla |
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

IMAGES
COMMENTS
Currently, corporations are more into using distributed systems and relying on networks and communication facilities for transmitting critical and important information that needs to be secured. Therefore, protecting corporations' information becomes more important, and information security is essential to maintain. Information security is defined as protecting the information, the system, and ...
Data are today an asset more critical than ever for all organizations we may think of. Recent advances and trends, such as sensor systems, IoT, cloud computing, and data analytics, are making possible to pervasively, efficiently, and effectively collect data. However for data to be used to their full power, data security and privacy are critical. Even though data security and privacy have been ...
Cyber Security is a blend of innovative headways, process cycles and practices. The goal of cyber security is to ensure protection of applications, networks, PCs, and critical information from attack. ... This paper reviews research work done in cybersecurity including the types of cybersecurity. The paper also discusses threats and prevention ...
A Security Model and Fully Verified Implementation for the IETF QUIC Record Layer. Antoine Delignat-Lavaud (Microsoft Research), Cedric Fournet (Microsoft Research), Bryan Parno (Carnegie Mellon University), Jonathan Protzenko (Microsoft Research), Tahina Ramananandro (Microsoft Research), Jay Bosamiya (Carnegie Mellon University), Joseph ...
IEEE Transactions on Dependable and Secure Computing (TDSC) publishes archival research results focusing on foundations, methodologies, and mechanisms that support the achievement—through design, modeling, and evaluation—of systems and networks that are dependable and secure to the desired degree without compromising performance. Read the ...
Pryde: A Modular Generalizable Workflow for Uncovering Evasion Attacks Against Stateful Firewall Deployments. Soo-jin Moon (Carnegie Mellon University), Milind Srivastava (Carnegie Mellon University), Yves Bieri (Compass Security), Ruben Martins (Carnegie Mellon University), Vyas Sekar (Carnegie Mellon University) Video-Based Cryptanalysis ...
A Secret-Free Hypervisor: Rethinking Isolation in the Age of Speculative Vulnerabilities. Hongyan Xia (Microsoft Research), David Zhang (Microsoft), Wei Liu (Microsoft), Istvan Haller (Microsoft Research), Bruce Sherwin (Microsoft), David Chisnall (Microsoft Research) A Systematic Look at Ciphertext Side Channels on AMD SEV-SNP.
The IEEE Transactions on Information Forensics and Security covers the sciences, technologies, and applications relating to information forensics, information security, biometrics, surveillance and systems applications that incorporate these features. For new submissions, go to Scholar One.
In this study, an overview of the concept of cyber security has been presented. The paper first explains what cyber space and cyber security is. Then the costs and impact of cyber security are discussed. ... Date Added to IEEE Xplore: 11 January 2022 ISBN Information: Electronic ISBN: 978-1-6654-1758-7 Print ...
As a rule of thumb, if there is more than 40% overlap between the original submission and the new paper, it will be considered a resubmission. All papers accepted by March 4, 2022 will appear in the proceedings of the symposium in May 2022 and invited to present their work.
Similar to 2023, IEEE S&P 2024 has a research ethics committee (REC) that will check papers flagged by reviewers as potentially including ethically fraught research. The REC will review flagged papers and may suggest to the PC Chairs rejection of a paper on ethical grounds. The REC consists of members of the PC. Authors are encouraged to review ...
Following the success of the recent TNSM special issues on cybersecurity techniques for managing networked systems in 2020 and 2021, this special issue will focus on recent advances in network security management. We welcome submissions addressing the important challenges (see the non-exhaustive list of topics below) and presenting novel research or experimentation results.
Similar to 2024, IEEE S&P 2025 has a research ethics committee (REC) that will check papers flagged by reviewers as potentially including ethically fraught research. The REC will review flagged papers and may suggest to the PC Chairs rejection of a paper on ethical grounds. The REC consists of members of the PC. Authors are encouraged to review ...
Submission Deadline: 30 July 2019. IEEE Access invites manuscript submissions in the area of Artificial Intelligence in CyberSecurity. Recent studies show that Artificial Intelligence (AI) has resulted in advances in many scientific and technological fields, i.e., AI-based medicine, AI-based transportation, and AI-based finance.
The classification of models for applying machine learning to cyber security is the focus of this paper. Published in: 2023 Systems of Signals Generating and Processing in the Field of on Board Communications. Date of Conference: 14-16 March 2023. Date Added to IEEE Xplore: 11 April 2023.
Problems of **information security** technology the "Internet of Things". **Information Security** Methods' Application Based on the Digital Management Approaches and the Deming Cycle in Improving the Modern Production's Processes. More links. Audio, Speech, and Language Processing, IEEE Transactions on. Automatic Control, IEEE Transactions on.
We solicit previously unpublished papers offering novel research contributions in any aspect of security or privacy. Papers may present advances in the theory, design, implementation, analysis, verification, or empirical evaluation and measurement of secure systems. Topics of interest include: Access control and authorization; Anonymity
The opportunity, nearly a necessity, is for security artificial intelligence (AI)/machine learning (ML) to act as a force multiplier by augmenting the cybersecurity workforce's ability to defend at scale and speed. The agility created by AI/ML augmentation of a cybersecurity system (henceforth, "security AI/ML" or "security AI/ML system ...
security research issues in this paper to help researchers. We identify literature gaps and propose future research to advance this . ... IEEE Systems Journal, vol. 11 (4), pp. 2536-2545, 2015.
In today's rapidly evolving corporate environments, ensuring comprehensive security measures is paramount. This paper presents SafeguardNet, a deep transfer learning-based model designed to enhance corporate safety through effective multiclass threat detection. Recognizing the limitations of existing binary threat detection systems, our approach introduces a diverse dataset encompassing a ...
The cyber security has become a hot research topic nowadays. The term cyber security is frequently employed replaceable with the term data security. In recent days, each system faces the cyber security threat virtually and the model framework should have the capacity to combine the security features and work as the system's integral elements. Various works have been conducted to discover the ...
With the rapid development of computer networking in all walks of life, network information security has attracted more and more attention from users. From the overall network information security to the security of a single computer and communication security has become a research focus. At present, the research on the computer's stand-alone information security has achieved initial results ...
The term Cyber security usually refers to high tech, procedures, and usage anticipated that are intended to preserve networks, devices, programs, and information from assault, damage, or illegal access. Cyber security may also refer to as information technology. Cyber security is important because numerous bodies function with the help of security itself and, then the role of cyber security ...
The examination of these 76 papers revealed threats to personal information in electronic payments, including phishing, malicious software, and data breaches. To address these security issues, electronic payment platforms need to implement multi-factor authentication, and biometric technology, and enhance the use of encryption technologies for ...
This paper proposes a novel approach that leverages advances in artificial intelligence and database management to address challenges prevalent in the education industry. The core motivation stems from the need to mitigate issues such as data bias, information overload and resource constraints that are common in educational settings. For this purpose, we have created a comprehensive database ...